Cloud Goblin
Phishing, Canaries and OPSEC fails
A Rise of Whatsapp impersonation Scams
In today's cybersecurity landscape, the methods employed by malicious actors have evolved significantly. One of the most recent and effective tactics is the use of popular messaging apps such as WhatsApp to stage targeted attacks. These attacks can take many forms, but one of the most concerning is when a malicious actor impersonates a senior executive of a company, to trick employees and obtain sensitive information.
Investigation
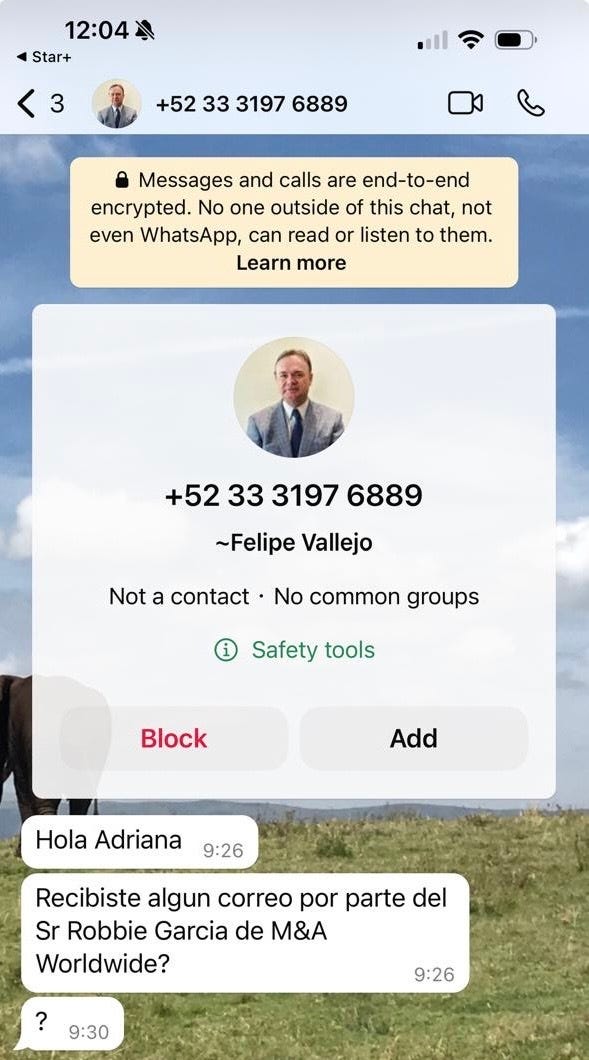
A company employee received a WhatsApp message from an unknown number. The sender introduced himself as a vice president of the company, which may be believable because of the professional tone and urgency of the message. The combination of the alleged authority of the sender and the urgency of the request is designed to lessen the victim's suspicions and cause him to act quickly.
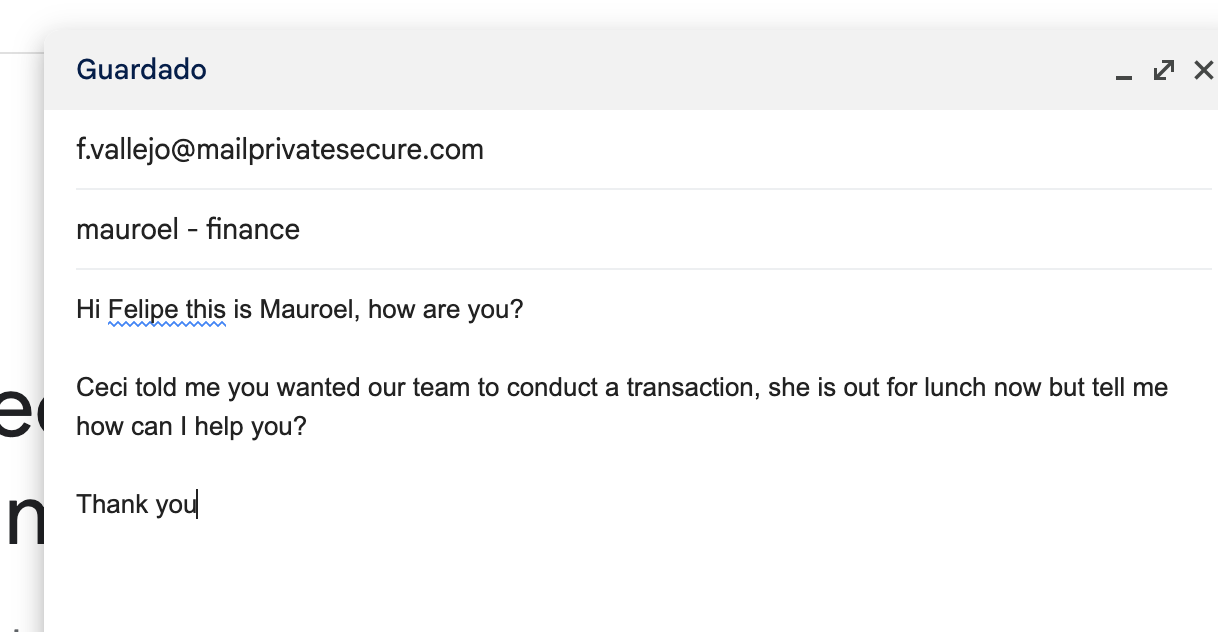
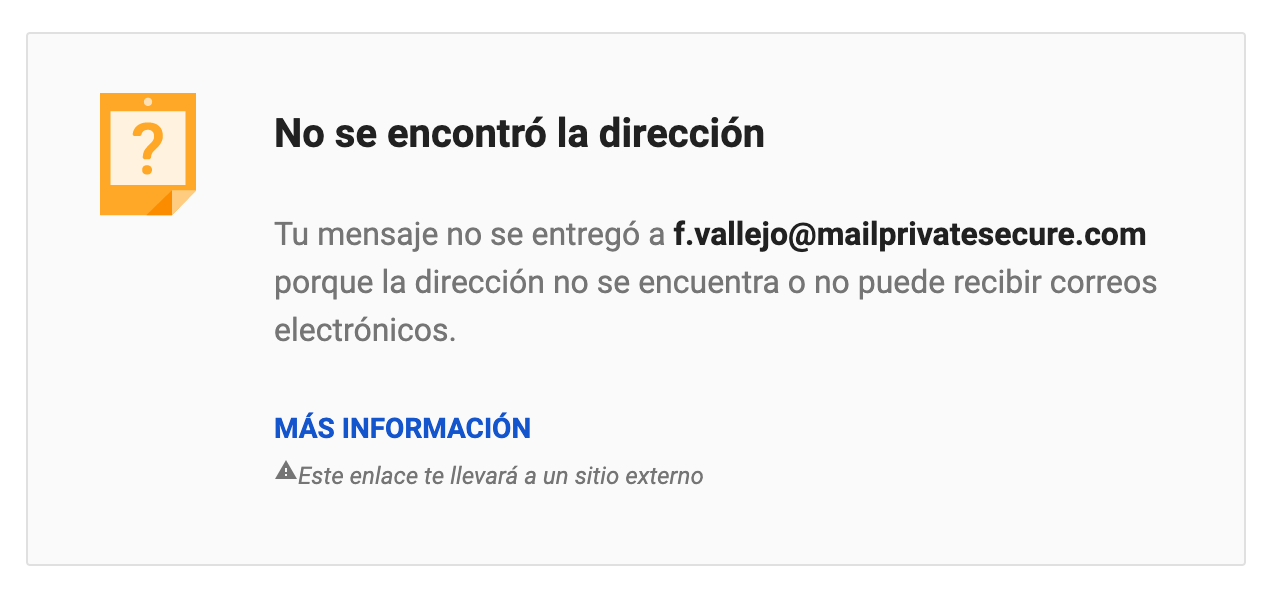
The victim receives messages with a commanding tone, instructing them to make contact through another medium using an unfamiliar email domain. On closer inspection, this domain appears dubious, aiming to perpetuate the conversation and deliver the next set of instructions.
Thanks to robust security training, the victim quickly recognized the potential for suspicious activity and, maintaining a calm demeanor, proactively reported the incident to the Quetzal Team, who immediately initiated a thorough investigation using the available data to uncover the source and extent of the threat.
At first glance, the lack of emails volume suggested that the domain was recently created.
However, after a series of checks, a surprising OPSEC fail caught our attention: the SOA (Start of Authority) DNS record somehow contained the malicious actor personal email 🙄.
After examining the phone number and making a call, we found that the malicious actor answered by his own without making use of automated systems.
The situation pointed out two possible scenarios: the attacker was either quite sophisticated in performing a bespoke, hand-crafted attack… or his lack of knowledge prevented him from automating the task.
Chasing the End of the Digital Rainbow
Armed with this information, the Quetzal Team took the initiative to deceive the malicious actor into believing we had fallen for their trap.
We communicated through the e-mail address the malicious actor provided emphasizing that the victim was on her lunch break.
The malicious actor was quick to respond by requesting bank information in a demanding tone.
With the intention of continuing the game, the Team crafted and sent a link with “bank information” that was actually… a canary token 🥷🏼.
A canary token is a strategic security measure designed to detect unauthorized access or data breaches. This mechanism involves placing a harmless, easily monitored piece of data in a location where it should remain untouched. If accessed, the token triggers an alert, signaling system administrators to a potential security threat.
There’s more than meets the eye. This email contains a link to a Canary Token, but that’s not all. Invisible to the eye, it also includes a 1x1 pixel transparent image (called a web bug), which serves as another Canary Token.
Flying over the Pot of Gold
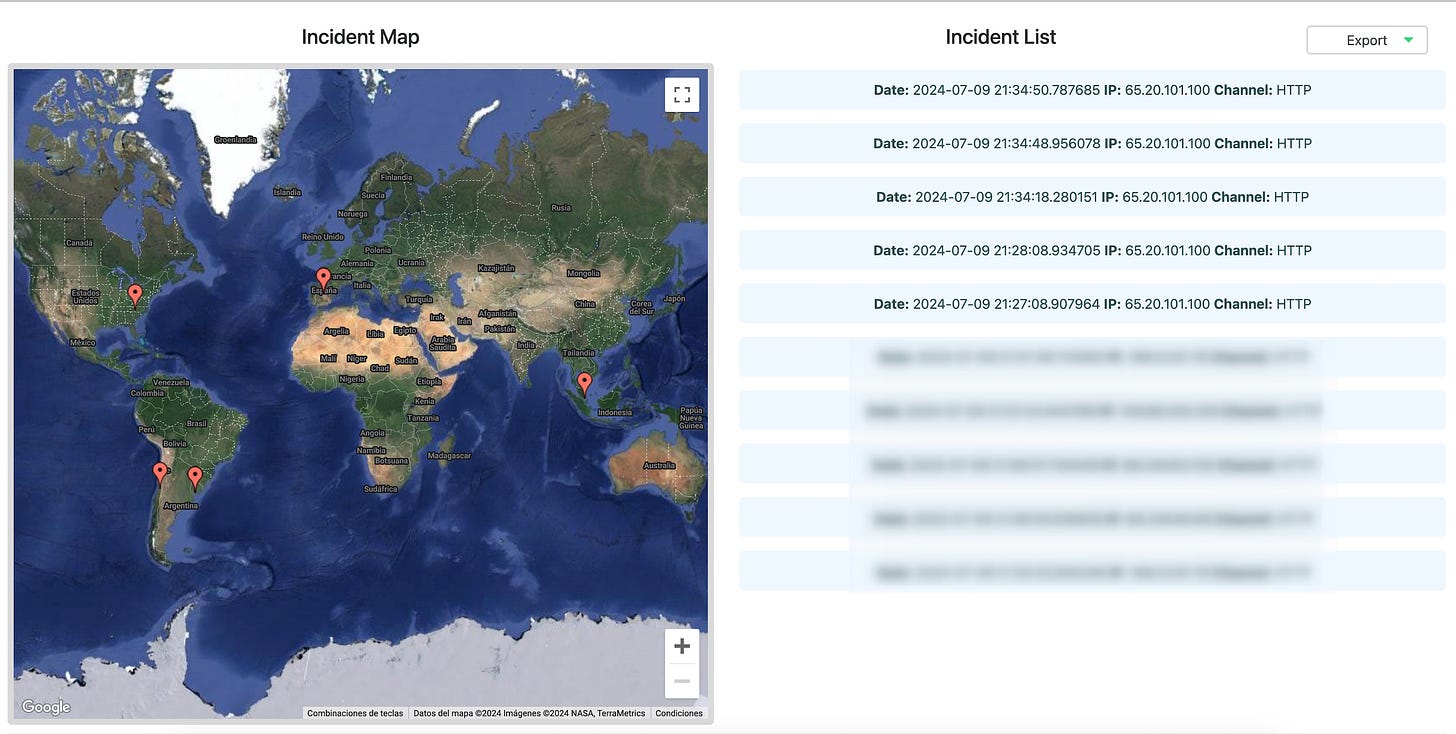
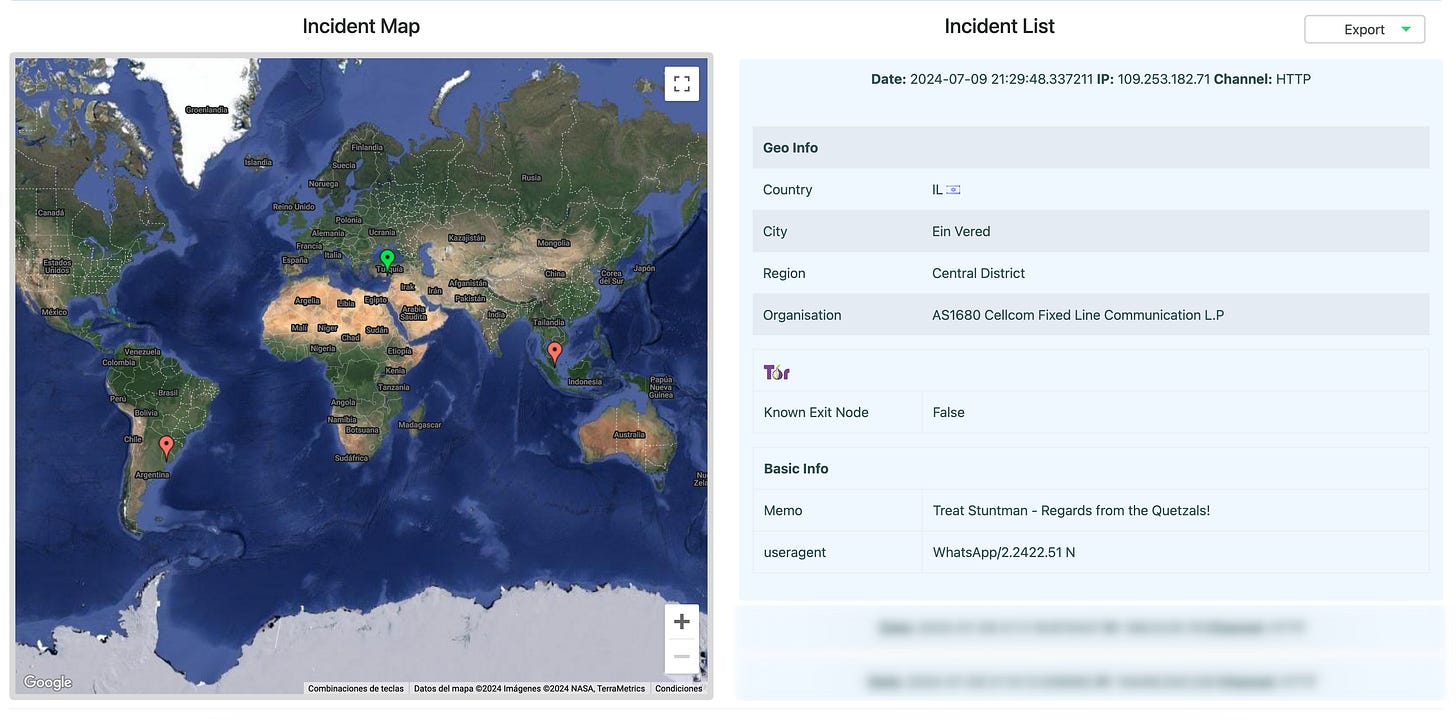
The malicious actor took the bait, triggering the alert system. Initially, one of our canary tokens - the one embedded in the link - suggested the attack originated from a VPS from VULTR in Spain, accessed via Mozilla.
But the plot thickens. The other canary token - the web bug - exposed the truth: our cunning intruder was actually using a mobile connection from Israel, and opened the link from none other than... his WhatsApp 🤦🏻♂️.
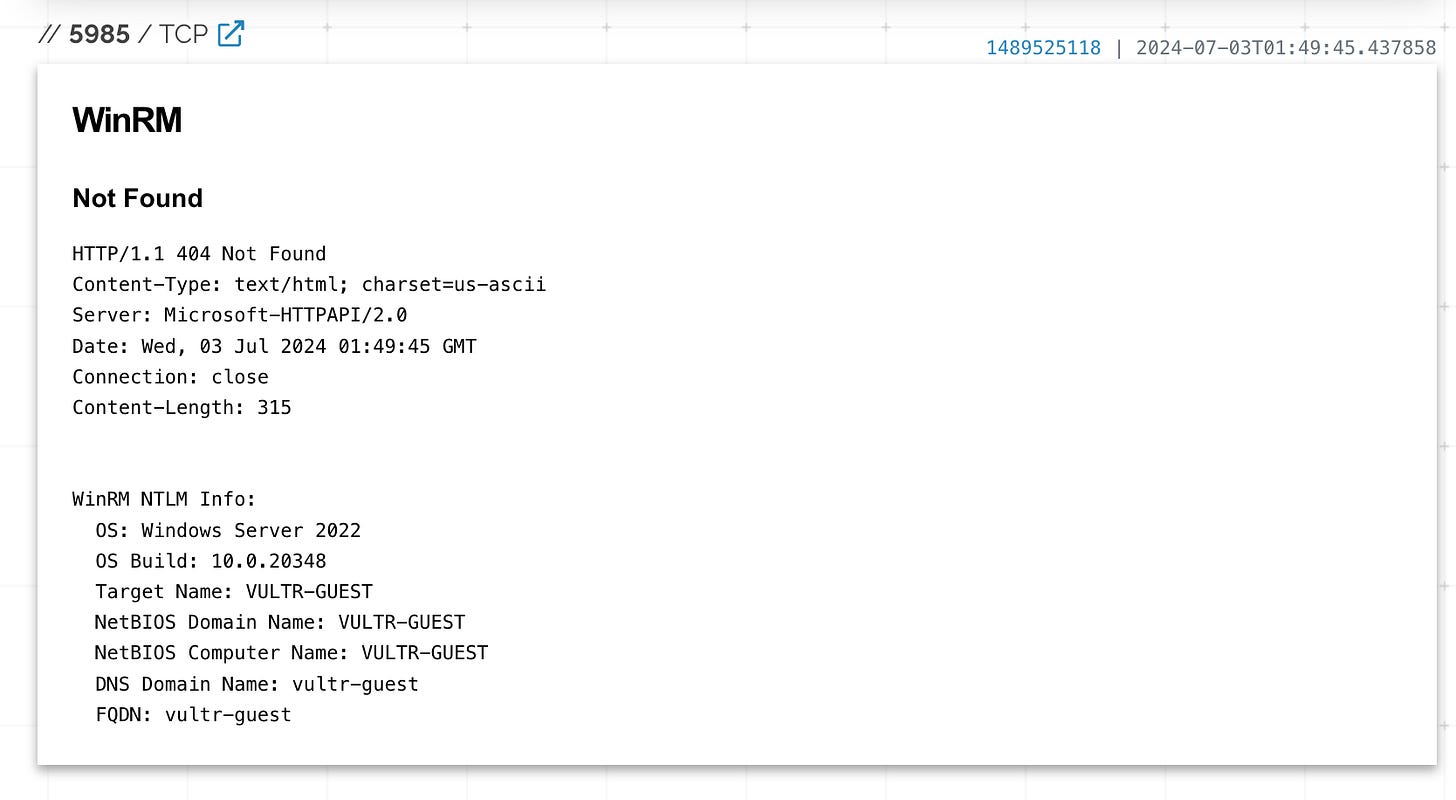
Armed with this new information, the Quetzal Team initiated a new IP analysis. This deeper dive confirmed that the malicious actor was using VULTR domain services.
Further investigation, based on fingerprinting, revealed that the actor was operating from a Windows system.
And the WinRM port enabled for remote management.
The actor realizes they've been caught and swiftly changes their profile picture to that of an unrelated man. A reverse image search reveals him to be the Director of Hoteles Misión in Mexico.
This indicates that the campaign is targeting the country as a whole, not just Bitso or the crypto sector.
One Last Treasure
Quetzal Team reported the entire infrastructure of the malicious actor, which gradually began to vanish without any trace of its existence.
Clearly, we’re the first to roll out a comprehensive set of Indicators of Compromise (IOCs) into a pulse and all the juicy details we’ve painstakingly gathered.
After that, Cloud Goblin ran away, but not before we could pocket some new IOCs.
I’m Uriel Corral, Security Engineer at Bitso, and I hope you liked my article.