How do you say "phishing" in Polish?
🇵🇱 Phishingowe
North Koreans, North Koreans, North Koreans. It’s all we talk about these days. So when we come across another kind of vermin Threat Actor, it feels… refreshing.
This time, everything was different: I couldn’t blame my least favourite site in the world, I couldn’t point fingers at ACME’s top customer, and I couldn’t even rip apart a malware sample.
But at least, I found a novel and creative way to compromise victims in the crypto sector. Let’s get to it.
Potential Coverage
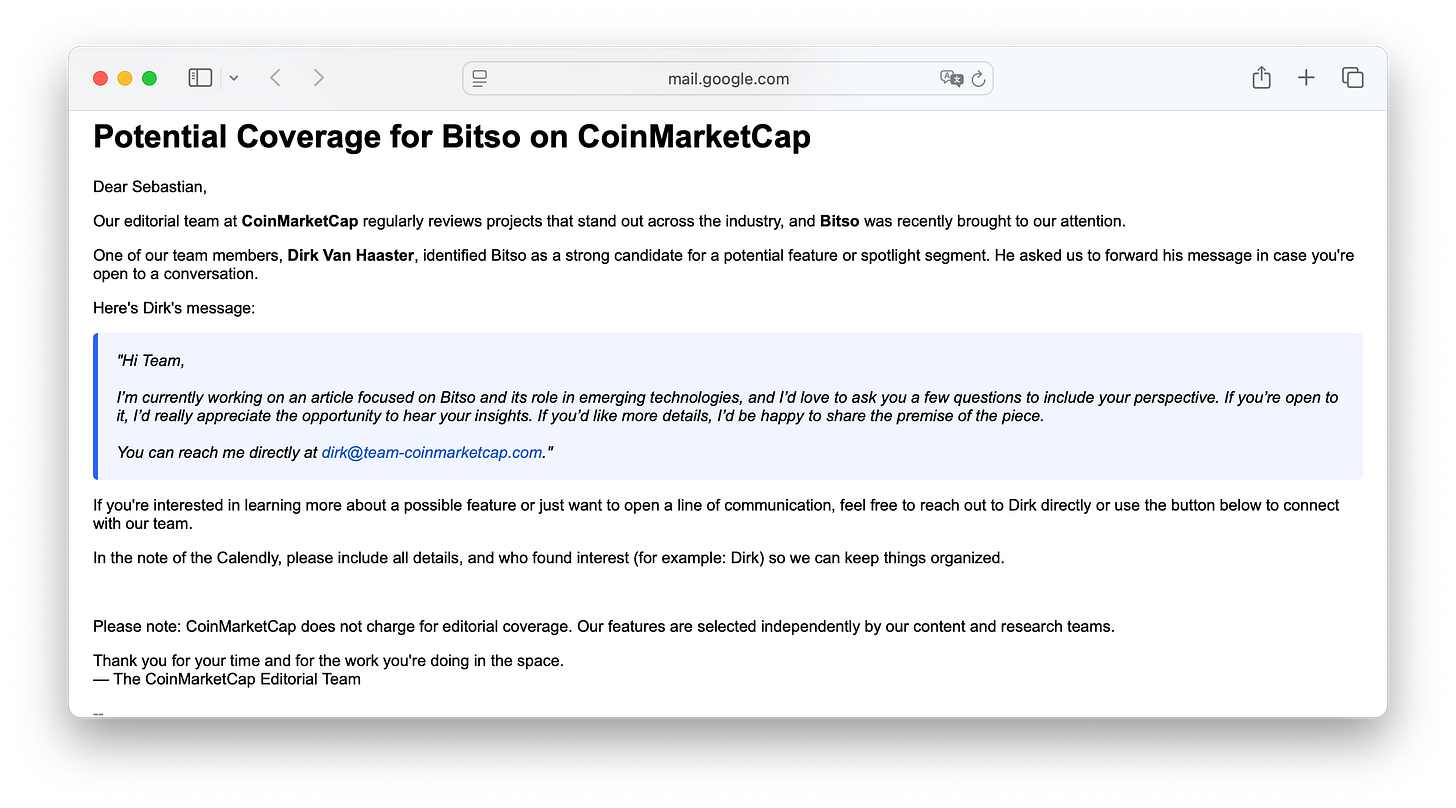
It all started with an email from someone claiming to work at CoinMarketCap’s editorial team, wanting to write an article about our company.
It was sent to specific people within the organisation, those with slightly more exposure than the average employee.
The first thing we noticed was the fake domain: team-coinmarketcap[.]com, registered just a few days earlier, on July 26th. Naturally, my first thought was that the Pyongyang Crew wanted to have some fun and work on their score (they’re way lower on the scoreboard compared to us) so I accepted the quest. But this had nothing to do with the Kim Boyz.
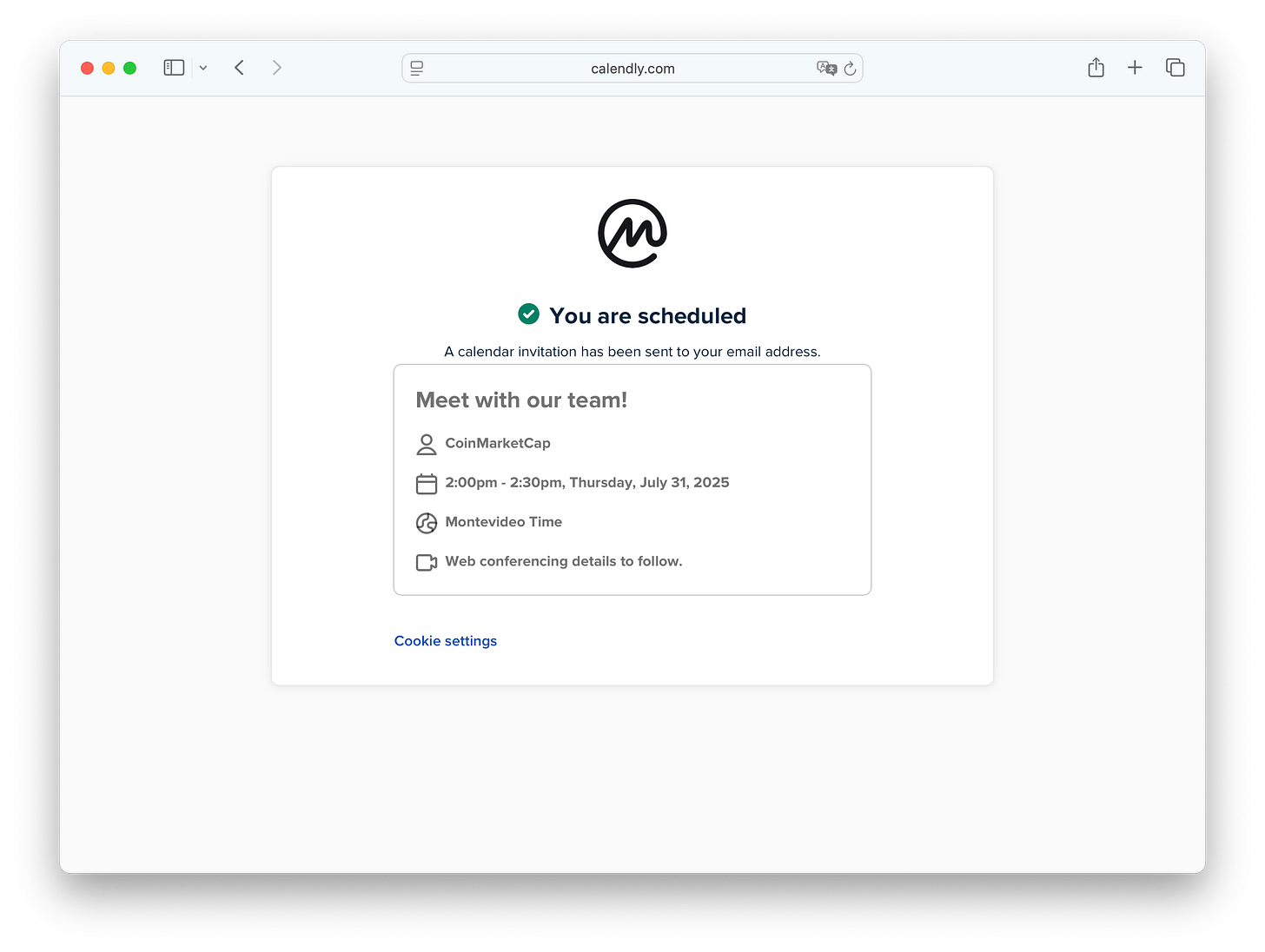
I booked a call via Calendly, where they had set up a fake profile using CoinMarketCap’s branding and naming, logos included.
While waiting for the meeting to take place, I started digging into their domain.
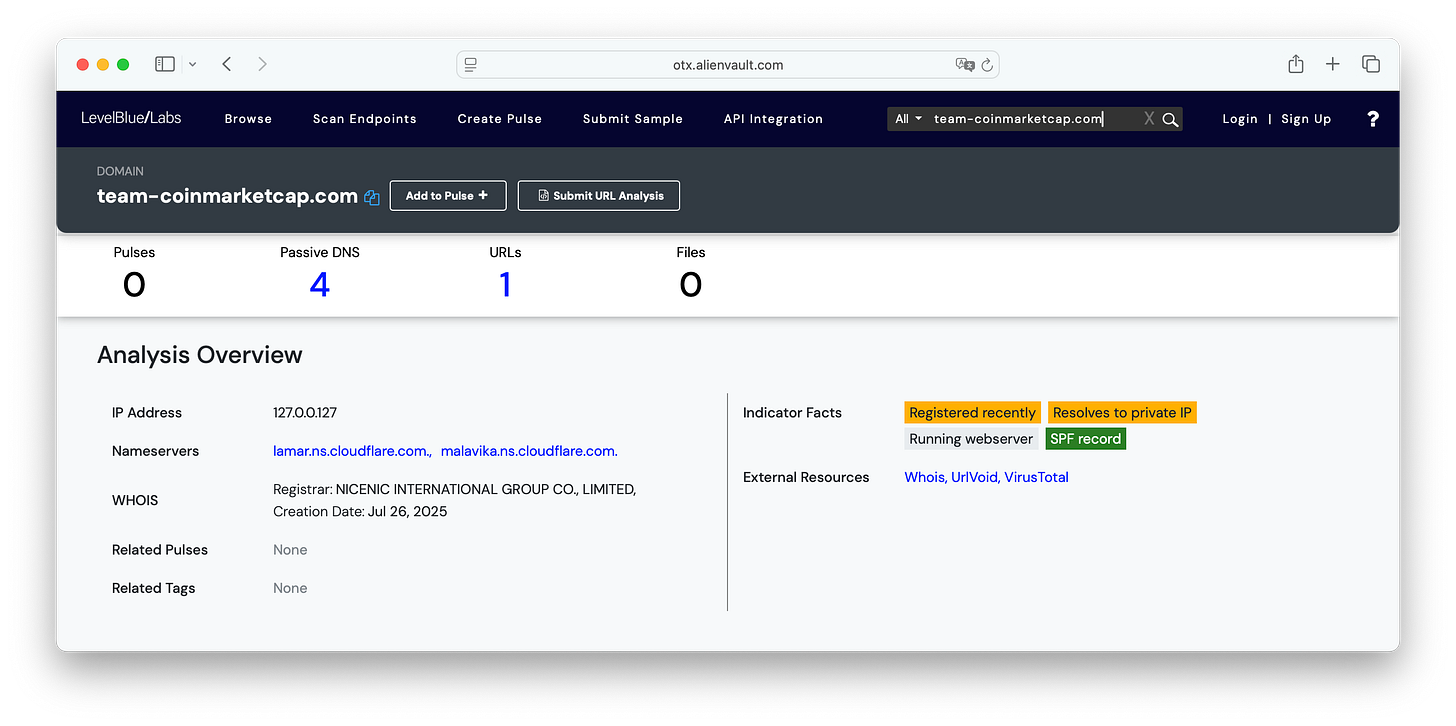
Our first stop is LevelBlue OTX (formerly AlienVault), our favourite open threat intel exchange hub.
Here, we noticed three interesting things:
The website points to a private IP address (127.0.0.127), meaning it’s unreachable from anywhere and unable to serve content.
It was delegated to Cloudflare.
It was created on July 26th of this year (yes, just a few days ago).
Why buy a domain without hosting any content?
Maybe they’re hosting something else. Time to dig in (literally, using the dig tool).
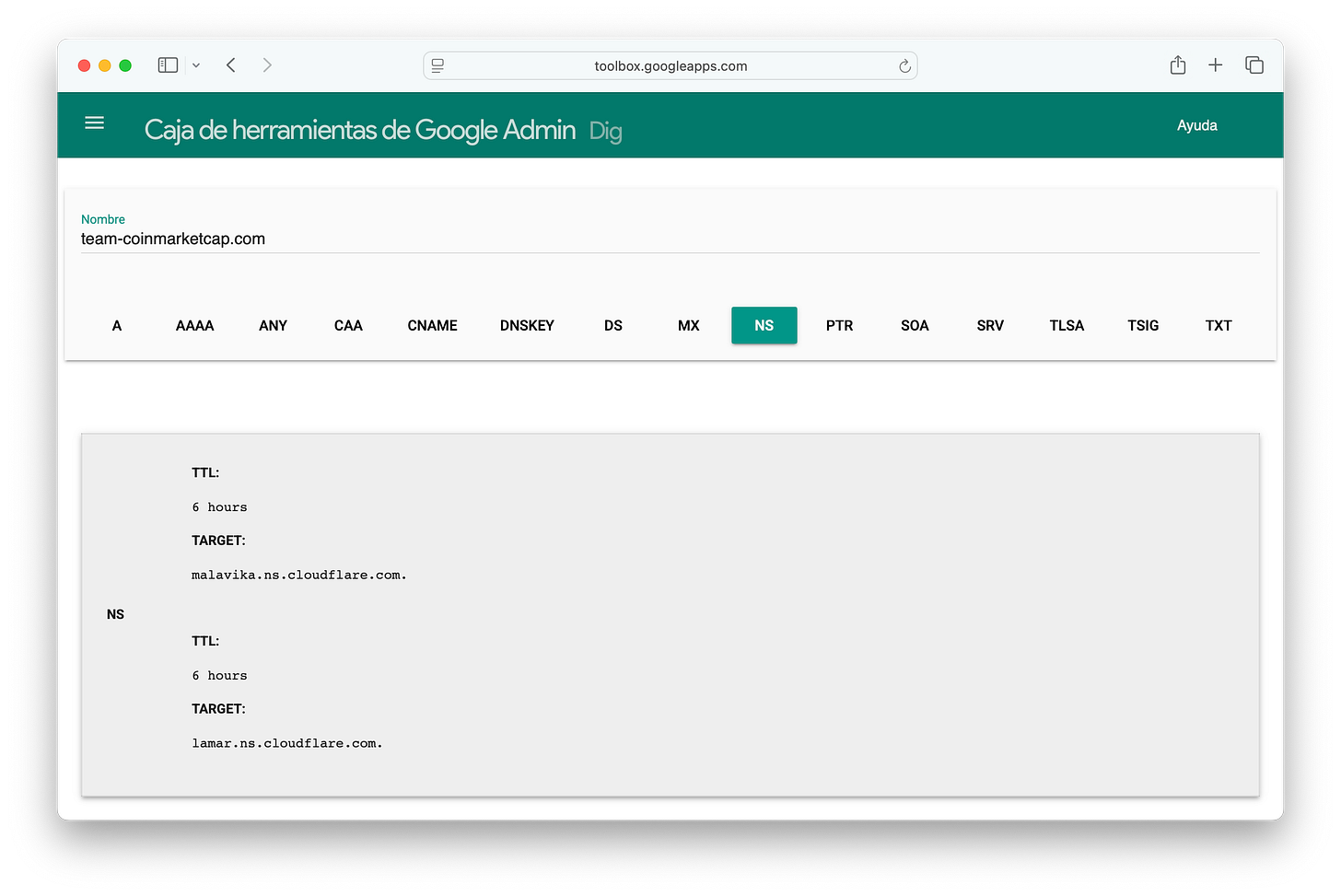
Using Google’s Toolbox, we can run dig online.
dig is a utility used to query DNS entries for a given domain, and it’s pretty useful for recon and intel work.
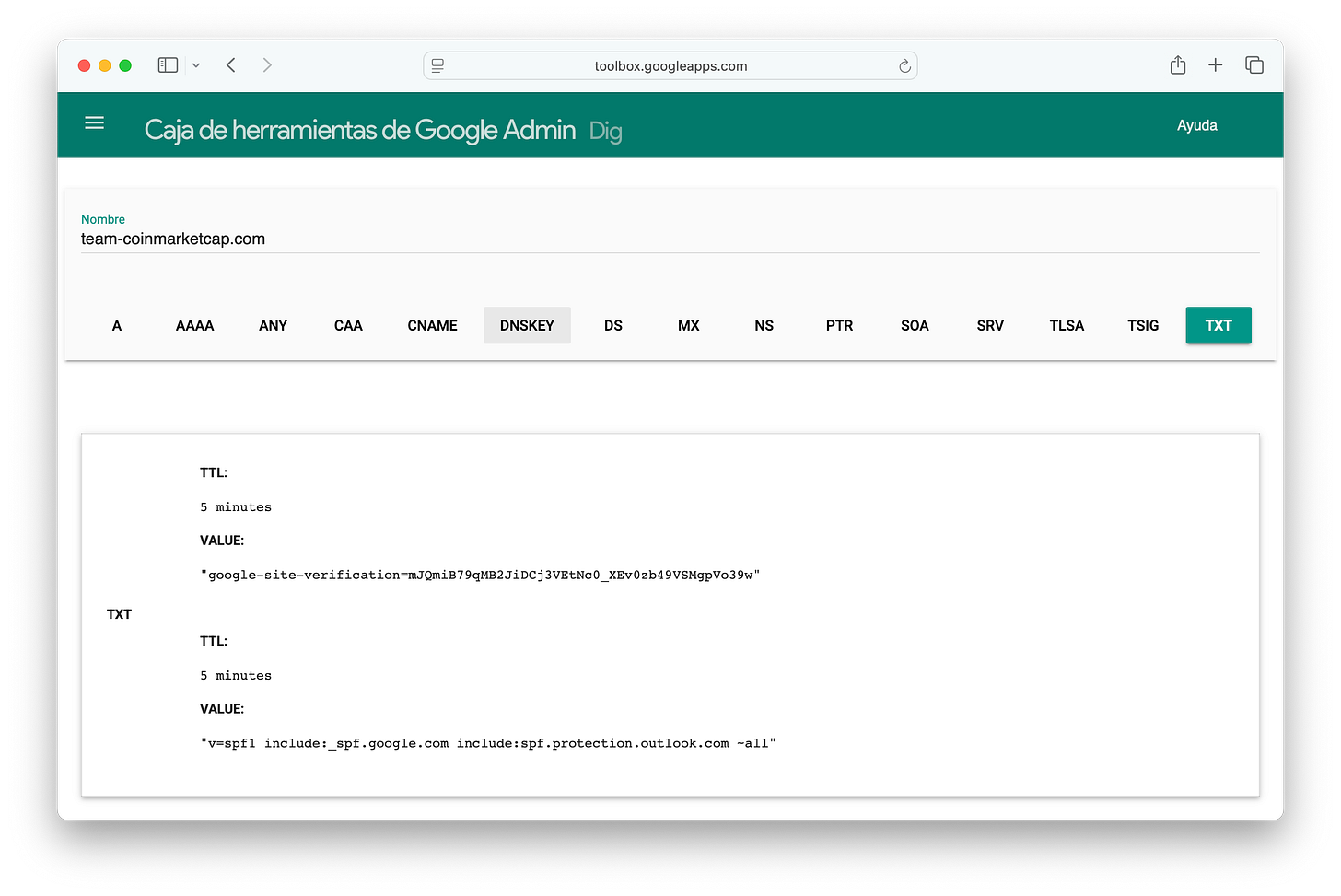
The first thing we notice is that the NS records point to Cloudflare (a clever move).
The second thing is a couple of TXT records: one for Google verification, and another one to declare an SPF record (also for Google).
So why Google? Why SPF? These are both related to email.
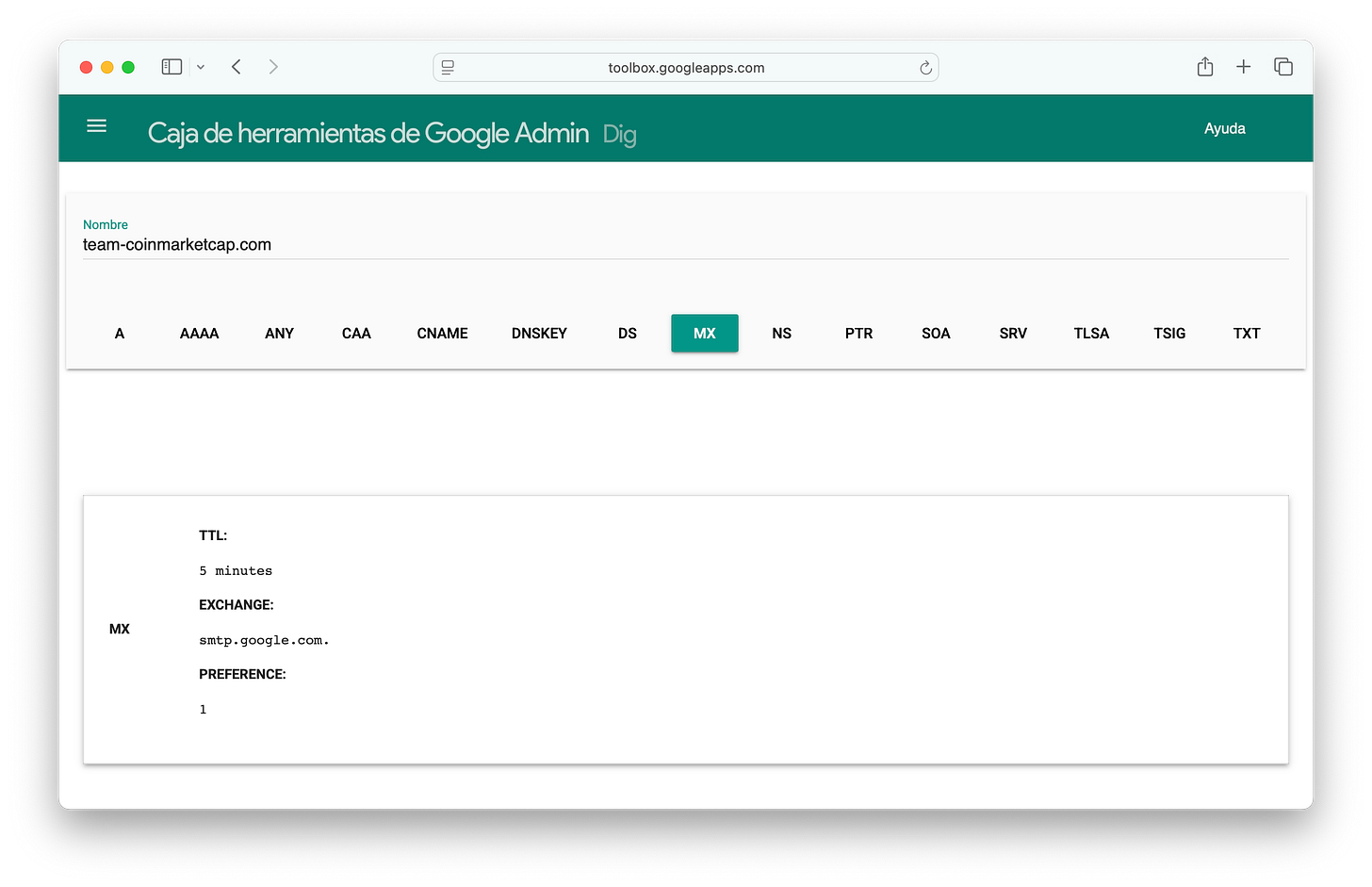
When checking the MX records (also email-related), we see that this domain serves a single purpose: to send emails using that domain.
There’s a second domain, from where they send the initial contact: contact-coinmarketcap[.]com.
This one has its MX records delegated on Hostinger and its NS records on DNSOwl.
With not much else to do, I waited for the day of the interview.
And here’s what happened.
The meeting
I jumped into the Zoom meeting and met Igor and Dirk. I was posing as someone in a position to control transactions and with visibility over user activity and personal information, a shiny bait they wouldn’t let slip by.
It was clear that Igor was the frontman, doing all the talking and introducing himself as someone super tech-savvy, born in Poland and educated abroad in the US.
Dirk, on the other hand, was impersonating a real CoinMarketCap editor, using both their name and profile picture. He barely spoke, and when he did, it was only to back up something his colleague had just said.
Igor asked me something quite specific: if I could change my application’s language to Polish, because “his note-taking app would act up if not.”
He immediately tried to excuse himself, saying his English was good, but not that good.
To me, it was obvious:
a) He didn’t have an Eastern European accent, at all. And I recognise Eastern European accent for… reasons that I’ll share later.
b) He spoke fluent English, so it was odd he struggled to understand me.
c) Note-taking apps rely on your local system language or a manually set preference, not on the remote participant’s language.
He used this excuse to also ask which operating system I was using, supposedly to “better help me change the language.”
I complied, for the sake of understanding the ruse. Igor warned me that the call would drop and that I’d need to restart Zoom. It did, and after rejoining, they began setting up the questionnaire. Then, suddenly, they tried their luck.
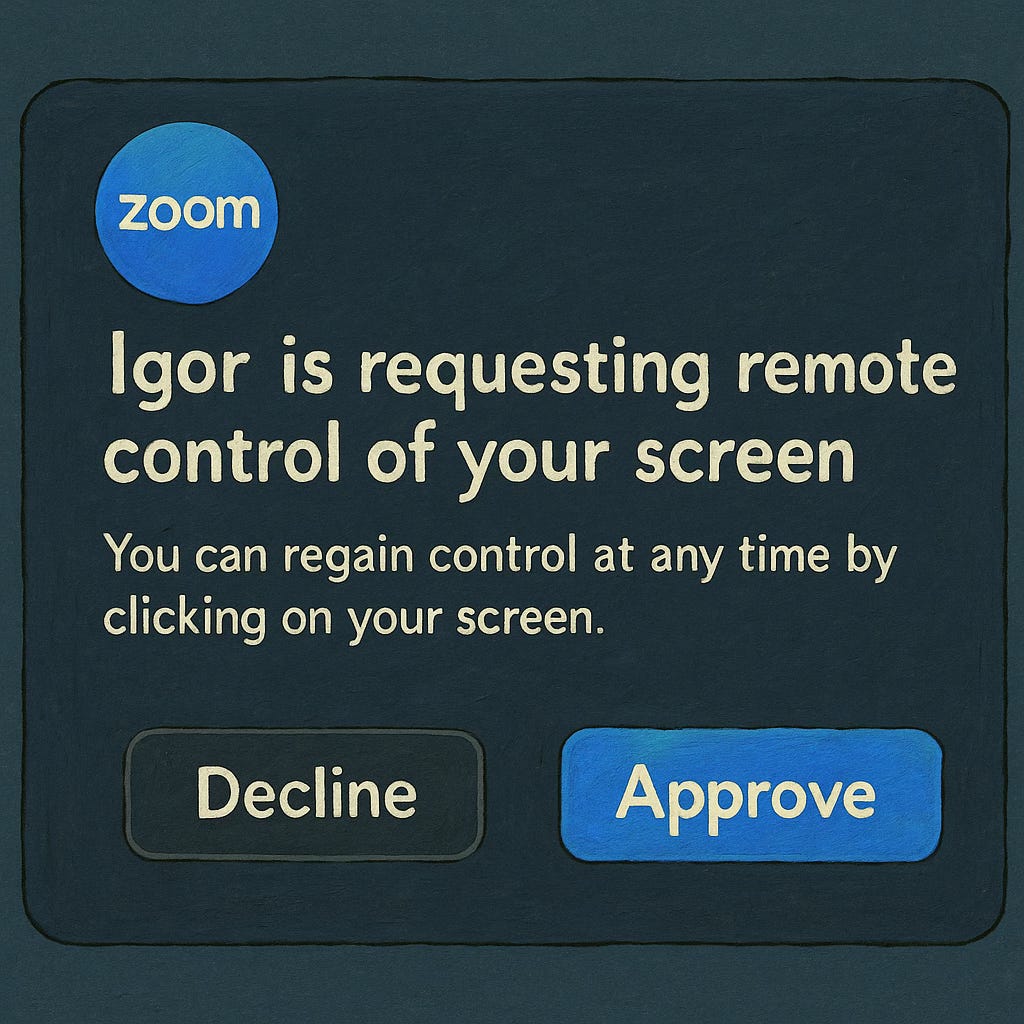
A window popped up, displaying a message in Polish with two options, also in Polish. One of them was highlighted in blue. According to Igor, it was something related to the note-taking app. He excused himself and asked me to click the blue button to continue.
In reality, the window was a notification that a remote participant wanted to take control of my screen (a standard Zoom feature). It did include a warning about the associated risks and permissions… but all of it was written in Polish.
If I had accepted, they would have gained full access to both my mouse and keyboard and with just a few key shortcuts, could have downloaded malware, granted remote access, or even attempted to steal files or credentials.
But their luck was far worse than mine, because they didn’t take into account two basic things:
a) I was recording the whole thing.
b) My second last name… is Polish.
Zemsta
I decided to cut off communication and moved on to emit an intelligence pulse and write this article.
I’m also sharing part of our conversation here, so users and companies can be aware of this new attack vector.
The following video has been edited to avoid disclosing certain indicators.
We may upload a full version in the future.
As usual, stay safe out there. Reach out to your Information Security team when in doubt, and please don’t get rekt.
Indicators of Compromise
Domain:team-coinmarketcap[.]com
Domain:contact-coinmarketcap[.]com
Email:dirk@team-coinmarketcap[.]com
Email:no-reply@contact-coinmarketcap[.]com