How to survive a Ransom DDoS attack
A real case
A brief background on Ransom DDoS attacks
What if you received a message from one of the most famous extortion actors on any given Friday as you were about to leave to enjoy the weekend with your family? Worse yet, what if that message is asking you for money so as not to affect your infrastructure?
Well, that is called Ransom DDoS or DDoS extortion and has been around for a few years, but has been increasing in recent years. One of the first cybercriminal groups to do so was cybercriminal group DD4BC (Distributed Denial of Service - DDoS - for Bitcoin), who attacked more than 140 companies, whose victims were online gaming companies, online exchange houses and financial services and entertainment companies.
Years later, in 2020, we have seen how Ransom DDoS attacks have evolved into more sophisticated campaigns by cybercriminal groups such as Armada Collective, Fancy Bear and Lazarus Group.
What is a Ransom DDoS Attack?
In a nutshell, Ransom Distributed Denial of Service (RDDoS) attacks are a type of extortion attack in which cybercriminals threaten companies with DDoS attacks if a ransom is not paid. In general, these attacks start with a ransom note and a small DDoS attack to demonstrate the seriousness of the threat.
Anatomy of a Ransom DDoS Attack
The Sampler
Cybercriminals often send a moderate DDoS attack to demonstrate that they have the power to launch a larger one.
The Ransom Note
After sending the moderate DDoS attack, the cybercriminals send a ransom note notifying that they may send a larger attack if a ransom is not paid. In addition, they notify you of the previous small DDoS attack to show that they are being serious.
Typically, this ransom note is sent a few hours before the target date of the attack to put pressure on the organization and achieve their goal: getting paid.
The Attack
Sometimes it happens, sometimes it doesn't, but on the day of the attack, you see a bunch of packages flooding your public assets.
Break in case of a Ransom DDoS Attack!
In this section, we will share insights on how we deal with a Ransom DDoS attack, how we prepared, and measures taken before and during the attack.
The Ransom Note
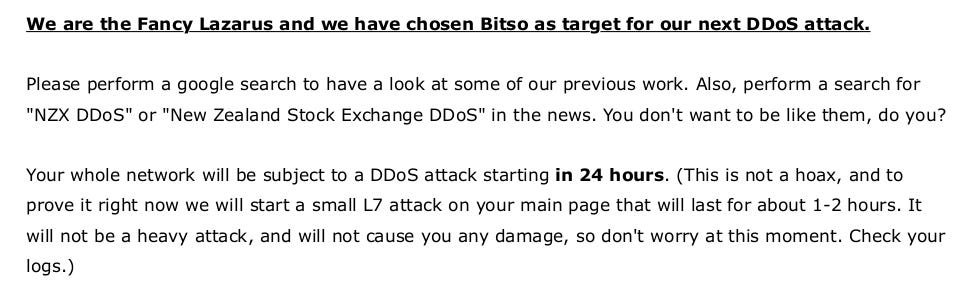
Our story begins on Friday at 17:00 hrs, our customer support team notified us about a note signed by one of the most famous cybercriminal groups: Fancy Lazarus. They mentioned that our company would be subject to a DDoS attack in the next 24 hours and to verify that they were not lying they invited us to check the logs. They attached the ransom price and the address of the wallet to send the funds.
Be calm and do not pay
This is one of the most important things to keep in mind. Cybercriminals want you to fall into the sense of urgency and execute actions without thinking. Instead, organize your team, follow the playbooks and activate the controls you have. Communication is the key to success in incidents like this.
Threat Profiling
Threat profiling is one of the most important activities in cases like this, as it provides valuable threat actor context to speed up the response process. Understanding the threat actor's Tactics, Techniques and Procedures (TTPs) allowed us to identify their techniques used and implement countermeasures in a more informed manner with the goal of minimizing impact.
There are many bulletins and feeds from which we can obtain threat intelligence, but also programs such as Cywatch and Infragard, which are partnerships between the FBI and the private sector that seek to share threat intelligence that will help companies to prevent hostile acts from harming them.
Teamwork
Another important factor is team collaboration. When we received the ransom note, we immediately created a warroom with all the teams involved in the operation: DevOps, Cloud Security, Customer Support and Leadership. In addition, we contacted our security providers to notify them about the upcoming attack, shared information about the threat actor and requested their support to verify that the configuration applied in their solution could help us successfully mitigate the attack.
Enable your defenses
Knowing the threat actor is important, but knowing the controls you have in place is crucial to success in mitigating attacks like these. Thanks to the incredible work of Bitso's engineering team, we have implemented security controls at different layers, which have allowed us to ensure that in the event that the threat overwhelms our outermost control, the next level control can block it. In our case, Cloudflare played an important role during the incident thanks to their DDoS protection and the Under attack mode.
Most of the malicious traffic was automatically blocked by the tool and those who managed to pass this control were successfully stopped by our inner controls. The security controls alongside the amazing job done by the engineers allowed us to say that no impact to our operations and users were observed.
Conclusions
There is no doubt that these types of attacks will continue to occur and the best thing we can do is to be prepared and ensure the least possible impact. Keeping calm, not being tempted to pay the ransom, organizing your team and reviewing (and reconfiguring, if possible) the controls in place will undoubtedly help us increase our chances of success when facing this type of attack.