It never Drains but it pours
Profiling and Burning a Drainer Campaign 🔥
It’s always DNS Drainers
Since discovering the malicious smart contracts scene (AKA “Drainers”), I’ve been fascinated by everything about it. It feels like a gigantic rig dedicated to every professional aspect of criminal engineering: Solidity and Rust backend programmers paired with skilled frontend developers, working side by side with UX and UI designers, malvertisers and mixers operators, all focused on creating their next counterfeit website to siphon millions from their next victims. It’s a cruel and unforgiving industry that pockets millions every month. But from time to time, we have a chance to bring one of them down.
SOLD
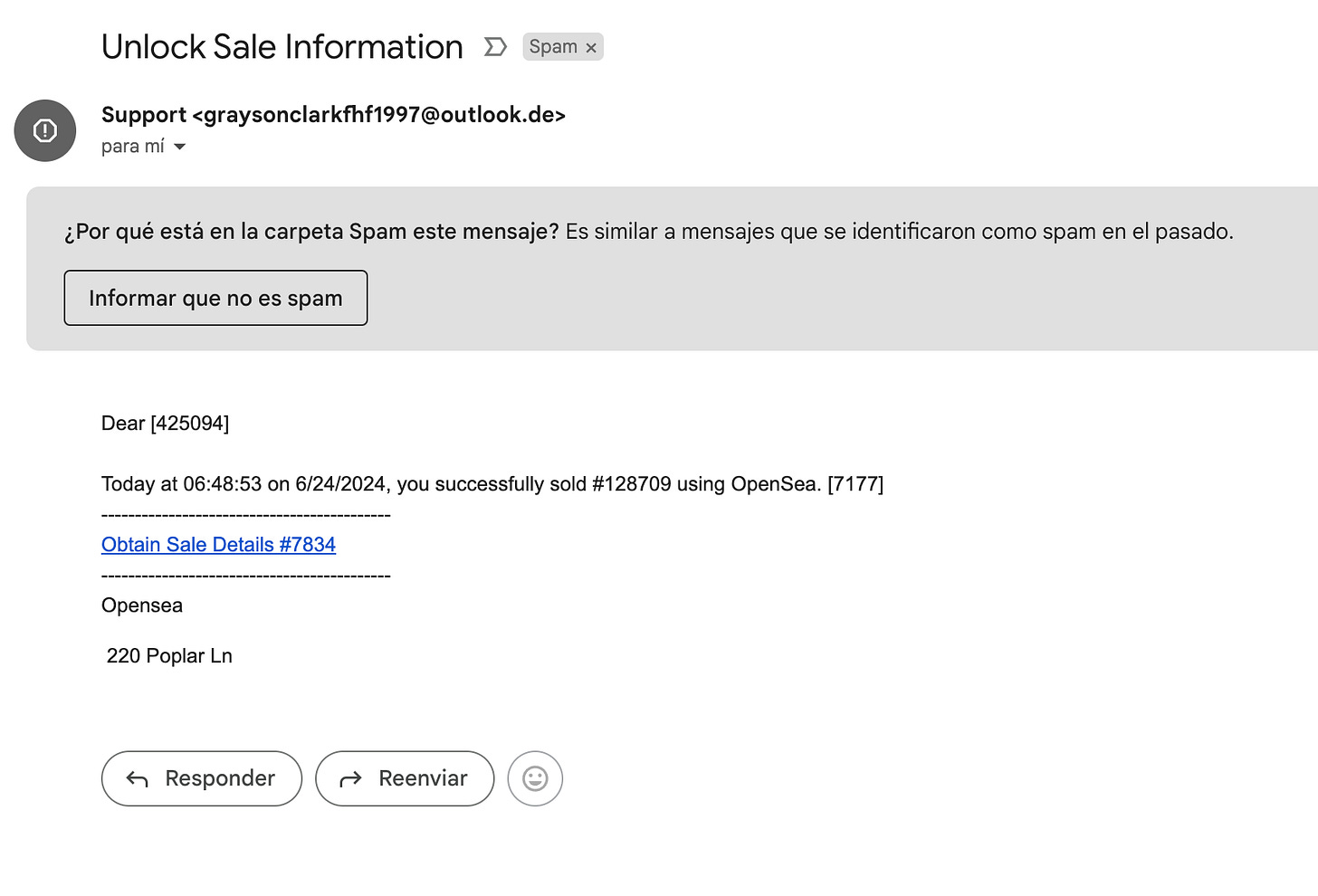
It all started after publishing my Malicious Fungible Tokens collection on OpenSea. This collection serves as a proof of concept for one of my talks and has a net worth of zero (and I’m also not willing to sell it at all). However, somehow, I received an email claiming I had just sold it, with a link to get the details of the purchase.
But the only thing this affiliate bought was a problem.
Lie to me
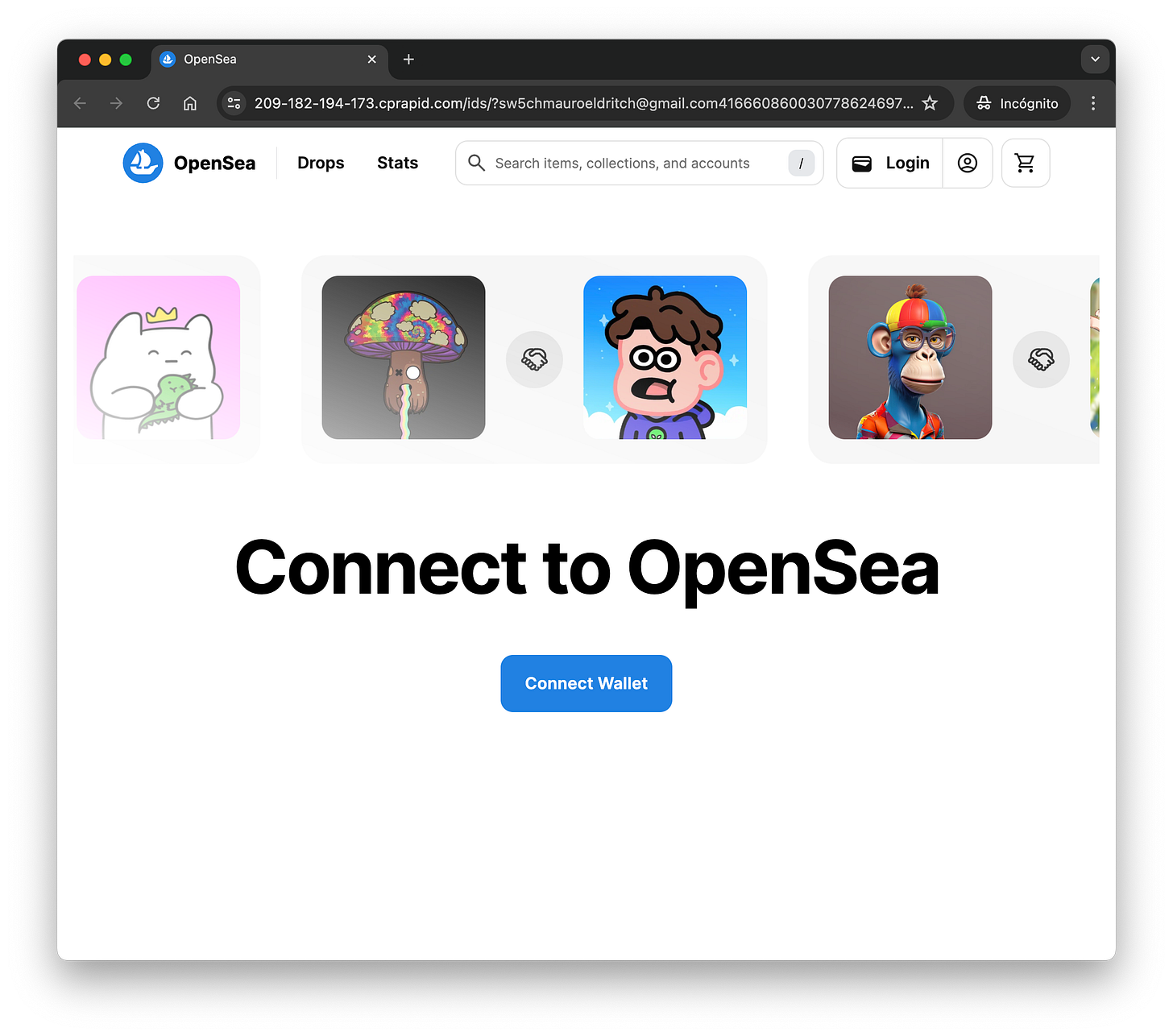
The first step in these operations is always phishing, regardless of the format: malicious advertisements, phony emails, you name it. Once you click on whatever link they shared with you, the next step is, well… more phishing: a website posing as a wallet, project, or even fake initiatives like a “gas fees refund fund”… again, you name it. In this case, they aimed too high by trying to impersonate OpenSea.
It looked pretty convincing, leaving aside the horrible domain name chosen. The next step is… well… even more phishing. Drainer operators will attempt to siphon your funds in two ways:
By asking you to sign a dangerous transaction, or
By asking you for your seed phrase (12 or 24 words) directly.
This case covers both of them. If you click any button on the website, a prompt asking to connect your wallet will appear.
Choosing Trezor or Ledger would trigger a prompt asking for your seed phrase directly:
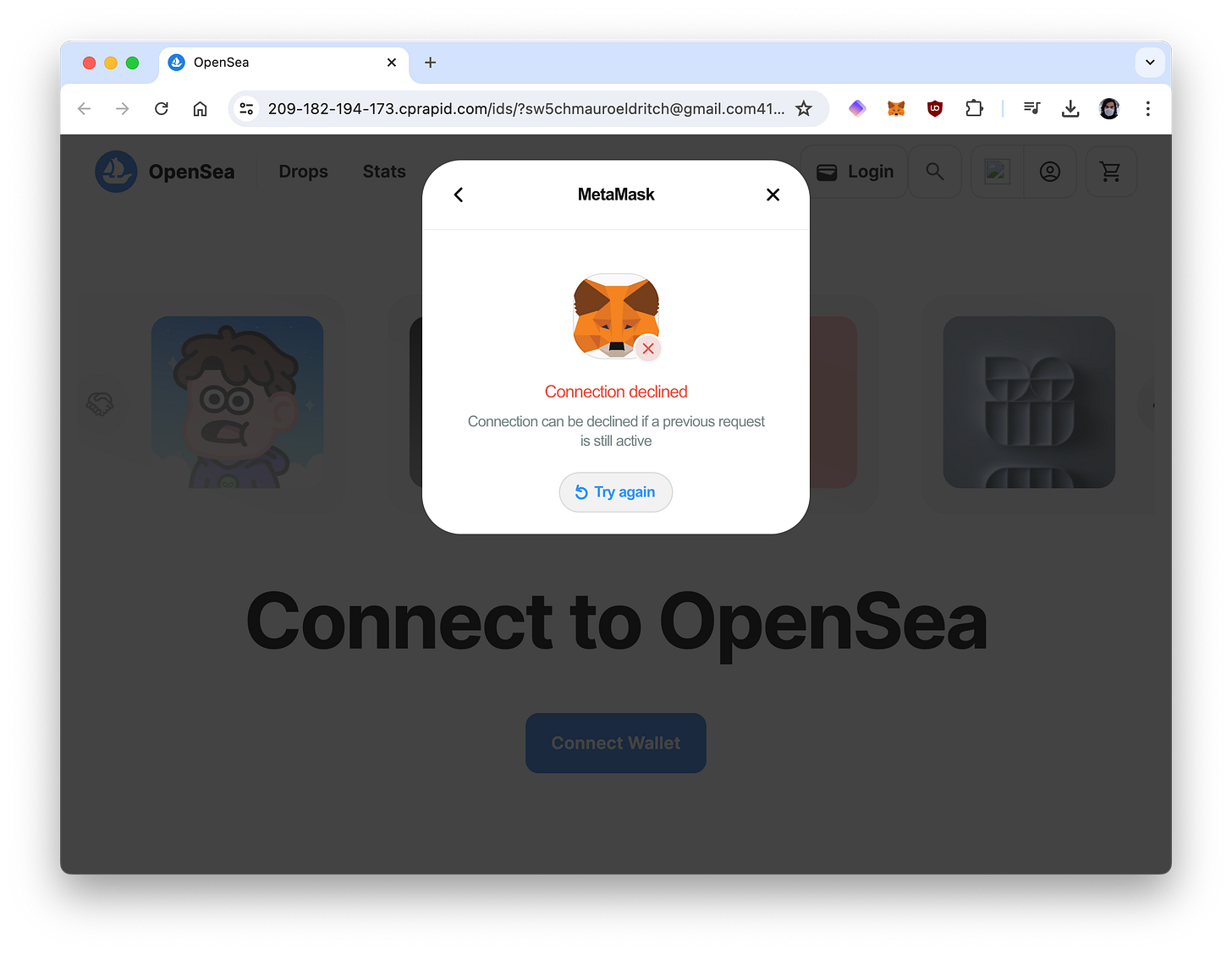
While choosing Metamask would trigger a transaction on your wallet:
The text says, in Spanish, that this site wants the following permissions:
See your address (hey, that’s understandable).
See your account funds (well, I may oposse but…).
See your activity (well, that escalated quickly).
Conduct transactions (💀).
I don’t think I’m signing that any time soon. But let’s take a look at what’s going on behind the scenes…
Flame Thrower Love
…And by taking a look I mean burn everything to the ground.
Analyzing the website interactions I found out two interesting parameters, one called “projectId” and another one called “auth”:
When decoded, it would show the following:
It’s a token for WalletConnect, a legitimate service that allows DApps to interact with your wallet in a safe way. But it doesn’t mean the DApp is safe or well-intended at all… So we report this token along with the rest of the identifying information like the Project ID.
A quick lookup on WHOIS services shows up NameCheap as the host registrar, we’ll let them know as well…
Some days later, everything vanished: domains, integrations, and spam senders. But that’s easier said than done.
At the end of the day, it’s the small victories that count.
Anyway, we can safely say… 🦊 Connection declined.
IOCs
Email:graysonclarkfhf1997@outlook.de
URL:hxxps://mielassurance[.]com/lp/.wp-cli/?asd@gmail.com41666086003077862469750951344
Domain:mielassurance[.]com
IP:23.235.205.99
Domain:209-182-194-173.cprapid[.]com
URL:hxxps://209-182-194-173.cprapid[.]com/ids/