Malware & Taxes
Profiling & Disrupting a banking trojan campaign
A tale of Cyber Bank Heisters
The banking trojans scene is particularly crowded with numerous organized actors and well-known malware families, including Janeleiro, Grandoreiro, Mekotio, and Casbaneiro, among others. Once a victim is infected with any of these trojans, the malware patiently waits for the user to visit specific banking or fintech websites, at which point it freezes the browser and displays a fake overlay. This overlay typically requests sensitive information from the user, such as credentials or MFA codes, or may even execute actions on behalf of the attacker. The distribution tactics of these trojans have been known for a long time and rarely vary. Their developers often distribute samples via phishing emails, sometimes casting a wide net and other times targeting specific individuals. These emails often masquerade as official correspondence related to tax or compliance matters, and occasionally attempt to impersonate government or tax agencies themselves. This was the exact case that targeted us recently, and we are not the kind to pass on an opportunity to reverse malware.
Malware and Taxes
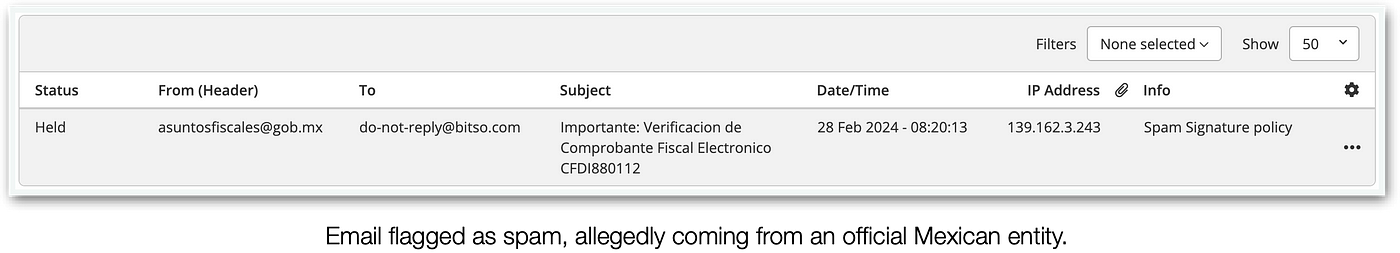
In life, there are two things you won’t be able to avoid: d̶e̶a̶t̶h̶ malware, and taxes. Sometimes, these two come bundled together. It all started when a suspicious email with a tax-related subject arrived from a seemingly official email address, automatically flagged by our anti-spam filter.
Why would an “official” email with an important-looking subject like “Important: Electronic Fiscal Invoice CFDI […] Verification” end up in the spam folder, alongside unsolicited vendors, romance scammers, and foreign princes searching for their next of kin? Well, let’s give it a closer inspection.
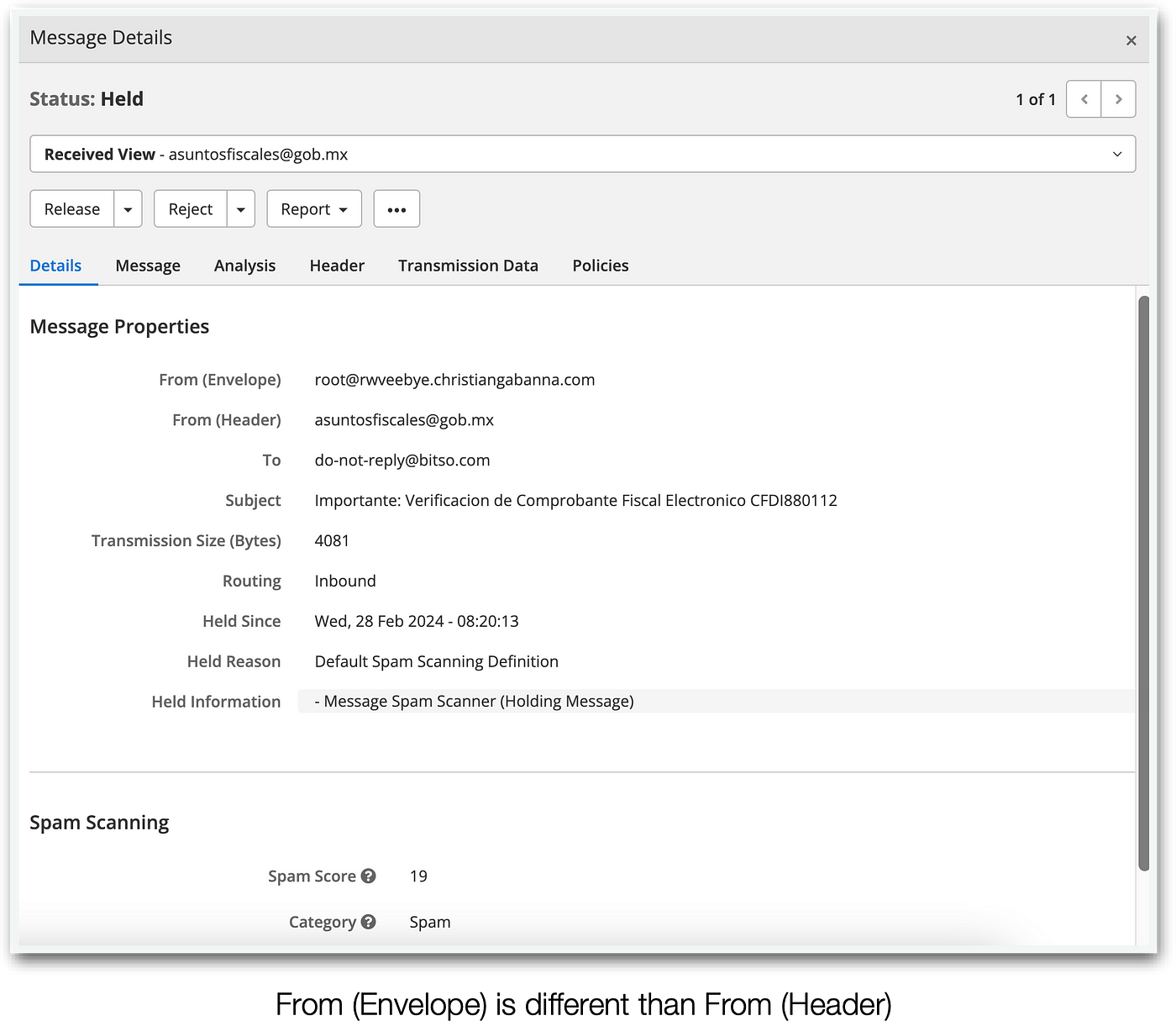
Now, that may be the reason: the original sender is not “gob.mx” but rather someone else’s website (either an attacker’s or a third party that got compromised). Let’s dive deeper into the email contents.
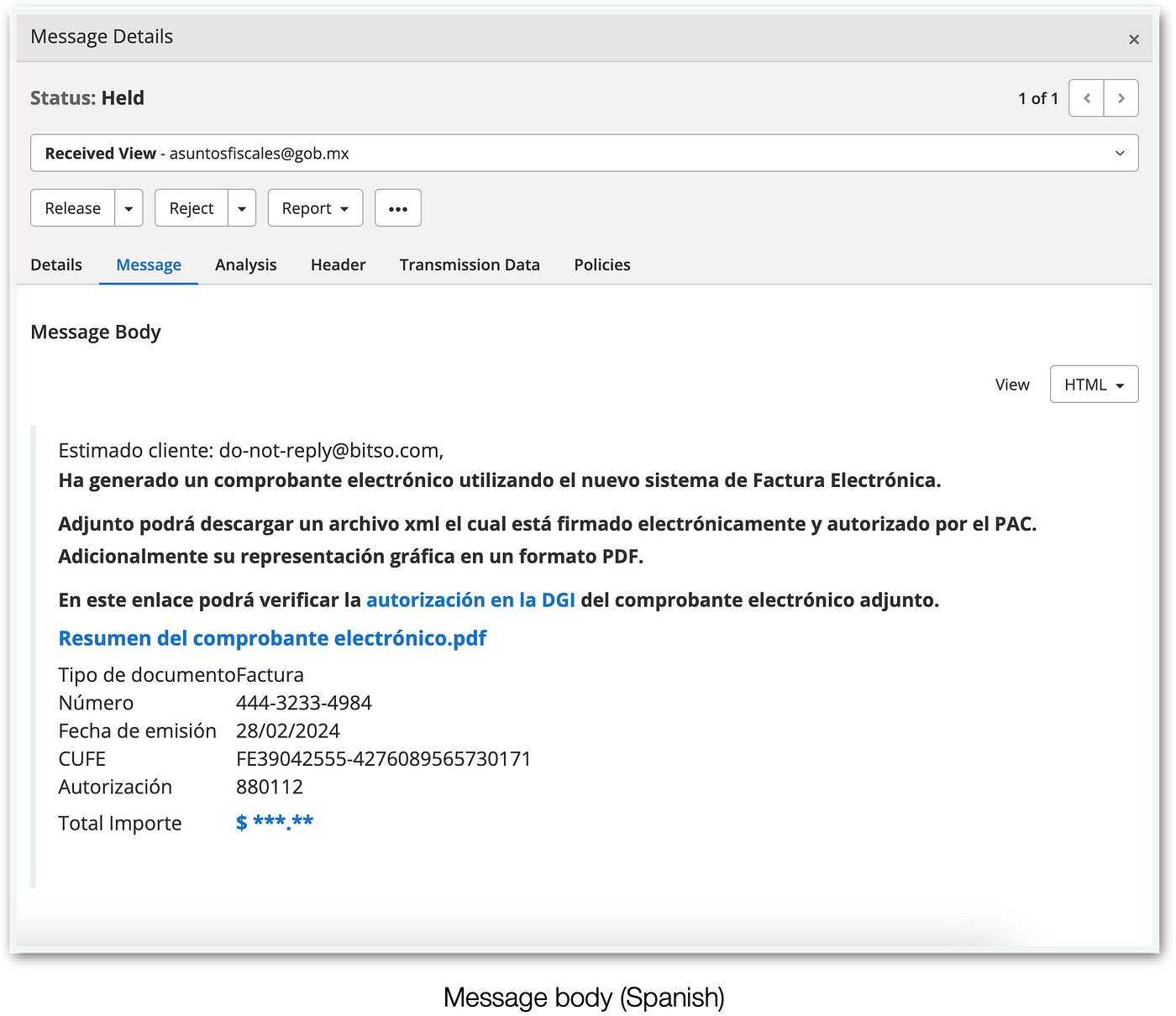
In fairly good Spanish (except for the PDF line, which is clearly broken and I will attempt to translate literally), the message body reads: “You have generated an electronic receipt using the new Electronic Invoice system. Attached, you can download an XML file which is electronically signed and authorized by the PAC. Additionally, its graphical representation in PDF format.”. Then, a couple of links — all pointing to the same URL — are provided. Let’s explore them.
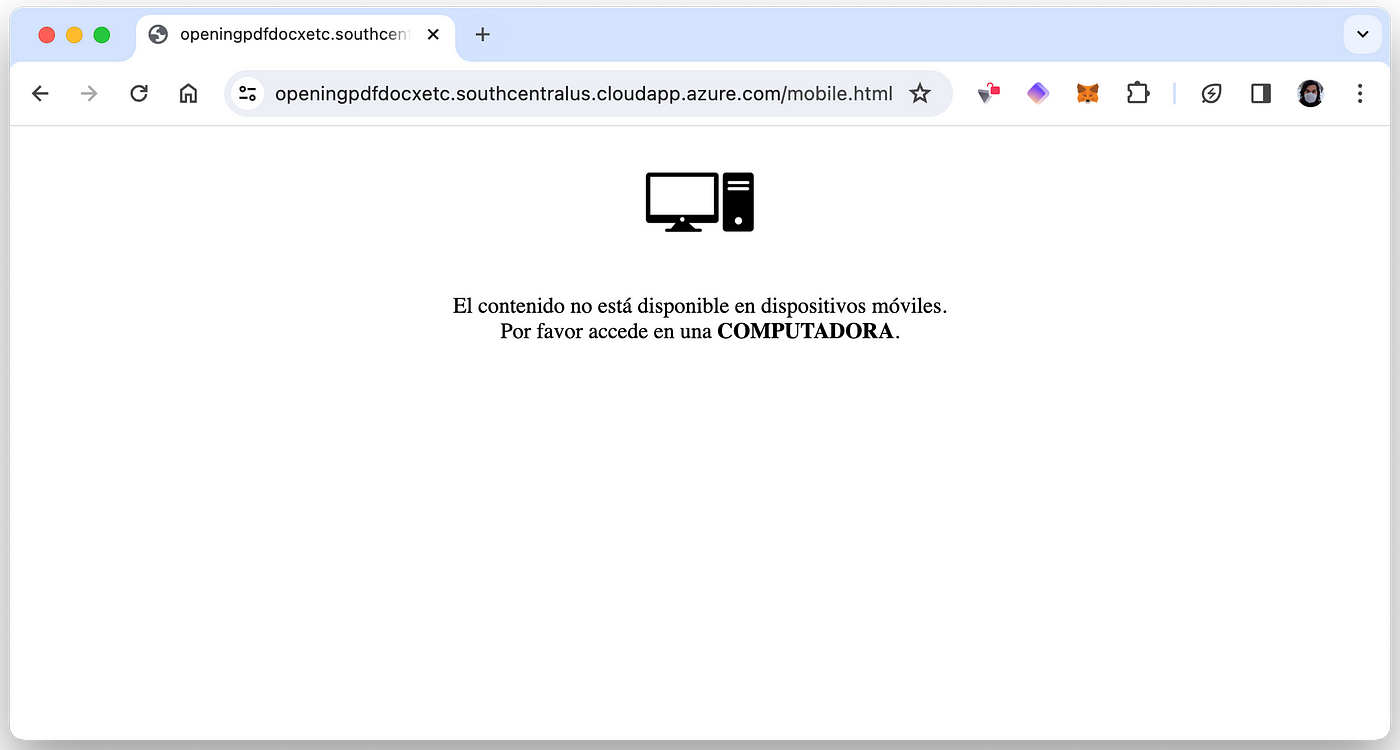
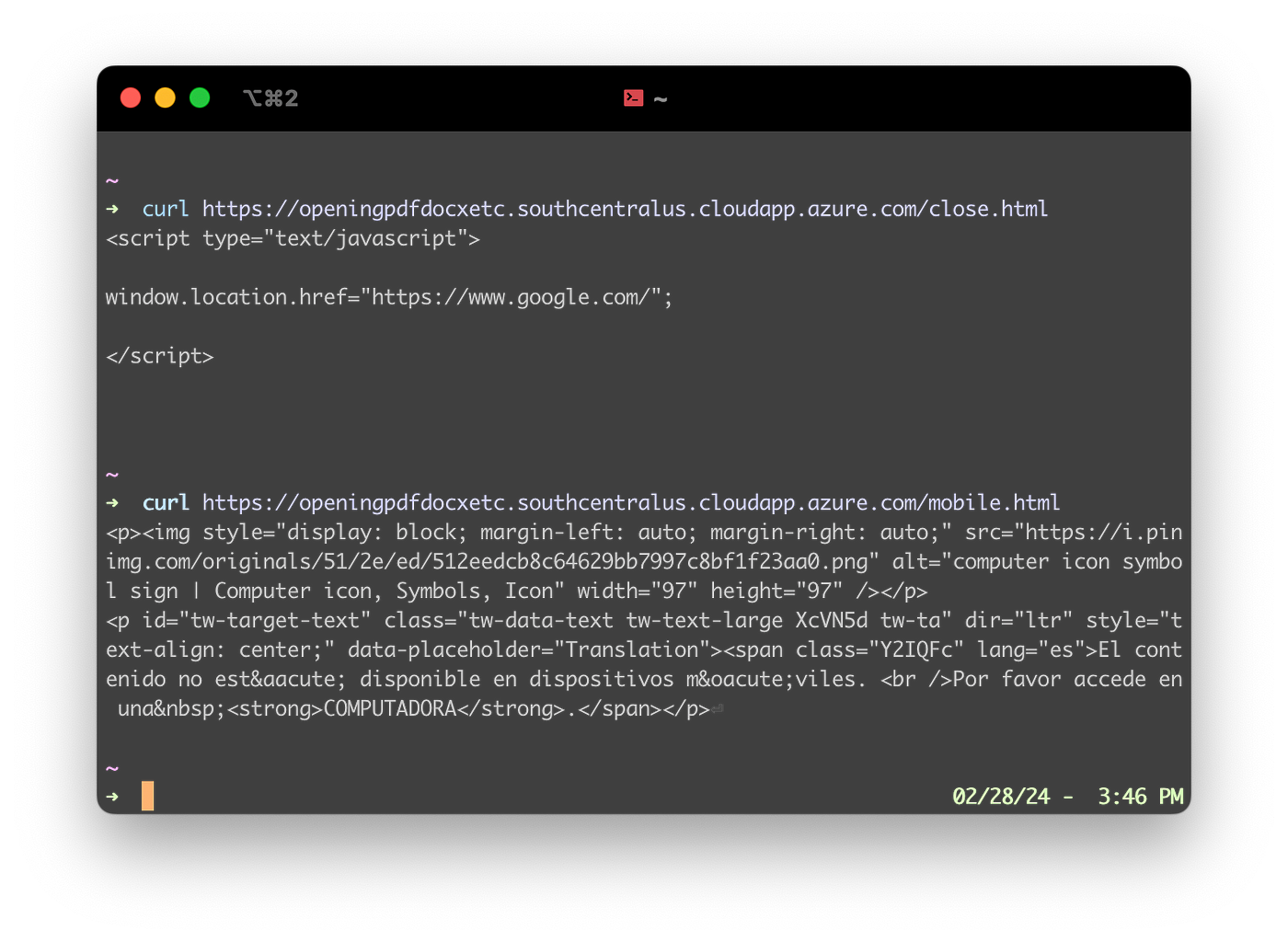
The website says: “The content is not available on mobile devices. Please access it on a COMPUTER.” Well, I’m on a computer already, so perhaps it’s expecting a specific User-Agent (web browser identification). After changing the User-Agent header I finally did some progress: the message was no longer visible as I was automatically being redirected to Google… But I’m not one to give up easily on free malware samples, so I decided to use Burp Suite to simulate the website interactions step by step and figure out why I’m unable to access it.
I managed to identify a redirection to a file named “close.html”. A closer inspection reveals a rather simple but effective trick: a JavaScript redirection.
A few moments later, after changing my VPN node and the User-Agent header once again to simulate Firefox on Windows, I was able to proceed with the infection chain. The next steps led me to… Dropbox. It was quite disappointing to see this distribution method, but at least the malware sample started downloading immediately, compressed as a 1.7MB zip file named “IMPUES_TOTRIB-UTZMHYfcpyLUGCCHYMPLAG.zip”.
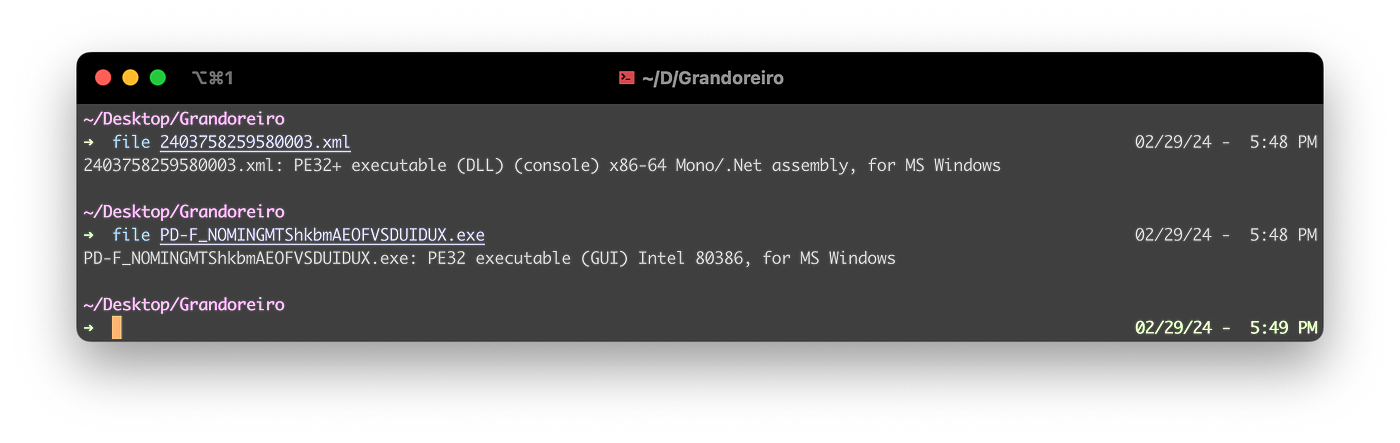
Inside the zip file, the disappointment continued: there was an EXE file, just like the good old times, accompanied by an “XML” file which was actually another executable.
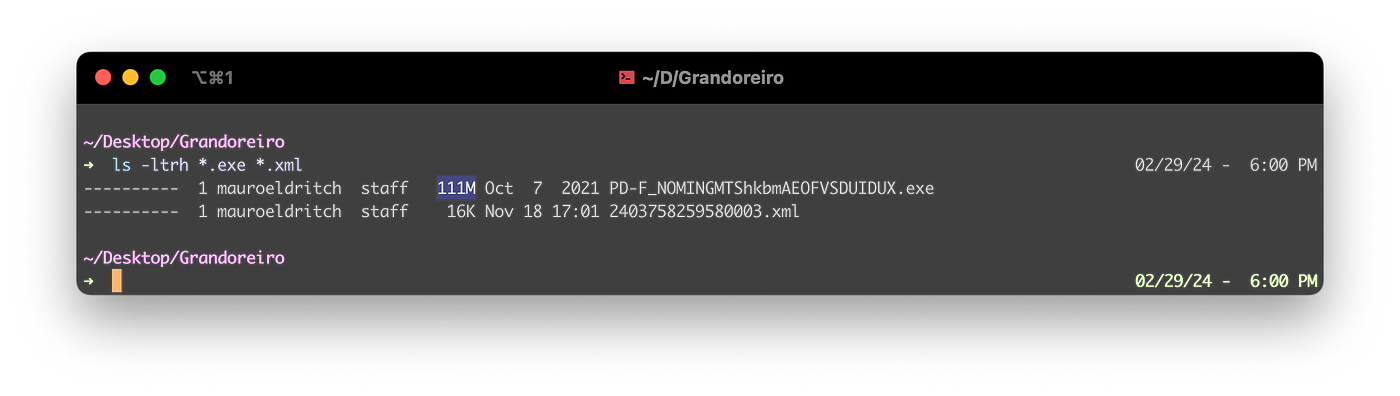
What immediately caught my eye is the outstanding growth of the EXE file, which ballooned to 111MB. This growth is likely due to an artificial pattern that can be easily compressed for distribution, but expands upon decompression, potentially discouraging antivirus programs from scanning the file due to its size. To put things into common talk, think about a malware developer adding 50.000 zeroes (“0” character) at a random point, which upon compression can be summarized as — using lots of imagination — “0*50.000” (50.000 times “0”), saving lots of space, but upon decompression will express every “0” character back, adding up to the final size.
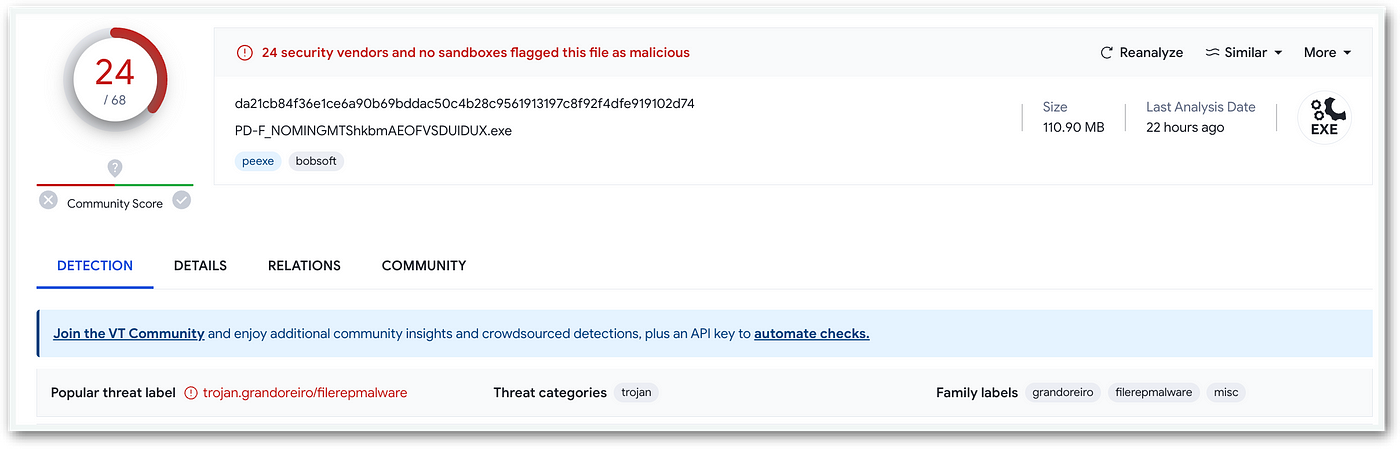
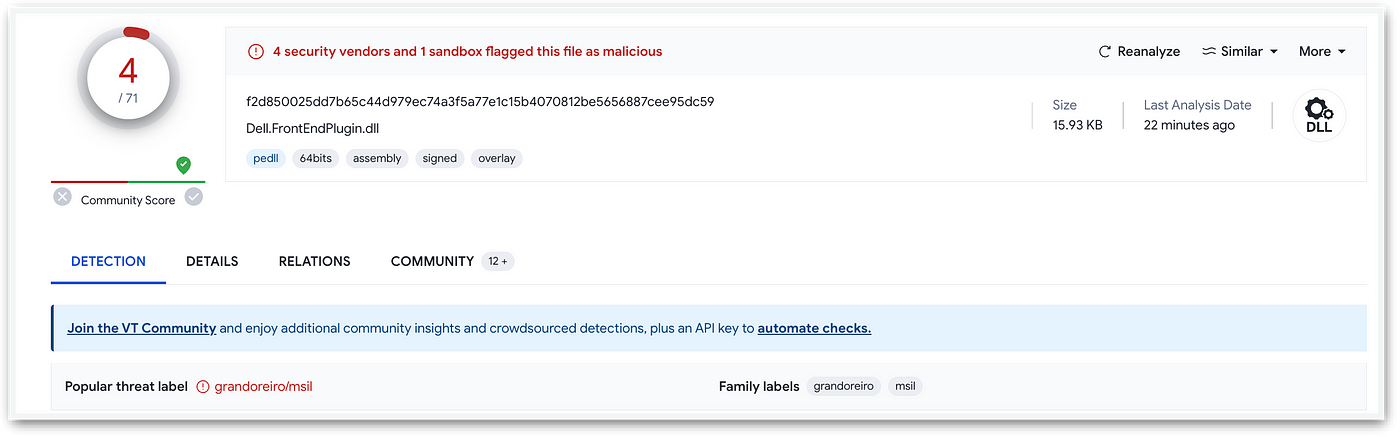
A quick analysis of both files pointed fingers to a usual suspect on the Banking Trojans Scene: Grandoreiro, a family which recently faced an important takedown of part of their infrastructure at hands of Law Enforcement, and whose shenanigans are well known, documented and even fought back.
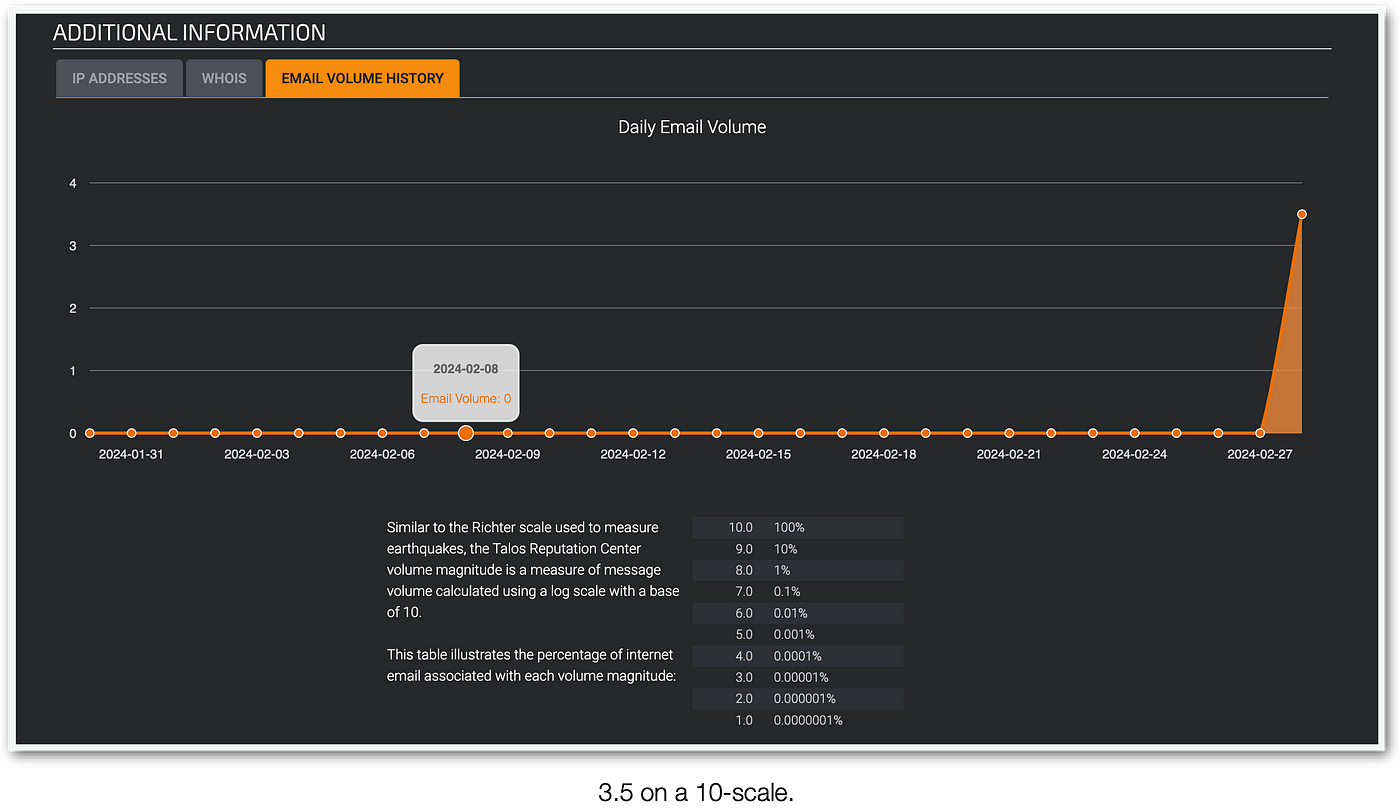
But what about their distribution domain? And I’m not talking about DropBox. The TA behind this effort used Azure to distribute the sample (URL available in the IOCs section). A quick look at its reputation and email volume on Cisco Talos tells us that it had a recent spike in its activity, marking that an active campaign took place after the “takedown” and is not residual activity.
Up to this point, we have seen a lot: compression and bloating tactics, oversizing files to discourage scanning, email sender spoofing, phishing via mass emailing (with almost no customization), good old .exe files sharing and even cheap JavaScript redirections… but all of these, techniques and artifacts, are long known and flagged, revealing what Grandoreiro truly is: an old dog failing at learning new tricks.
Appendix I: IOCs
IP:139.162.3.243
Domain:rwveebye.christiangabanna.com
Domain:openingpdfdocxetc.southcentralus.cloudapp.azure.com
URL:https://openingpdfdocxetc.southcentralus.cloudapp.azure.com/mobile.html
URL:https://openingpdfdocxetc.southcentralus.cloudapp.azure.com/close.html
URL:https://openingpdfdocxetc.southcentralus.cloudapp.azure.com/?4443233_4984_880112695617-355202355202427608953904255539042555.pdf
SHA256:da21cb84f36e1ce6a90b69bddac50c4b28c9561913197c8f92f4dfe919102d74
File:PD-F_NOMINGMTShkbmAEOFVSDUIDUX.exe
SHA256:9b0db4ab7e469e1b74e801ed943e7deabe1ed4a6514d3755de7694c39852036a
File:IMPUES_TOTRIB-UTZMHYfcpyLUGCCHYMPLAG.zip
SHA256:f2d850025dd7b65c44d979ec74a3f5a77e1c15b4070812be5656887cee95dc59
File:2403758259580003.xml
String:Importante: Verificacion de Comprobante Fiscal Electronico CFDI880112Appendix II: Intelligence Pulse + New IOCs
A new campaign was launched mid May, which produced new intelligence and indicators of compromise.