Stealing Christmas
And this time it's not the Grinch
The holiday season is also open season for malware developers and operators. With teams at various companies working with reduced personnel—some resting at home, others eagerly awaiting their well-deserved break—it becomes an unmissable opportunity for the ecosystem’s bad actors.
While some see this as a problem, we see it as a chance to unwrap early presents and play with these rabid toys one last time before the year-end dinner. Here’s the story of how some bad actors tried to steal our Christmas, but instead became our Secret Santa.
The client who cried wolf
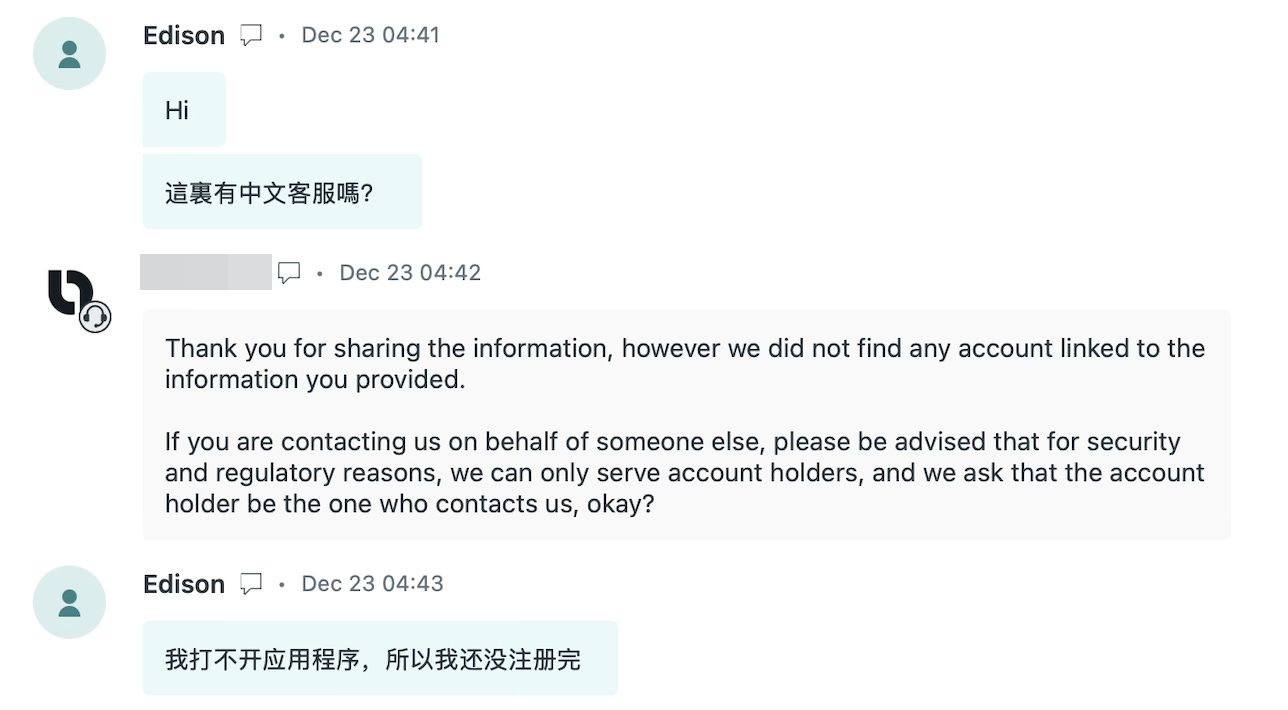
December 2024. It all started with a ticket—or rather, a flood of them.
Each one came from newly created, empty accounts, written in broken language, and asking for help in our support chat in Chinese.
And it gets weirder (social engineering at its finest).
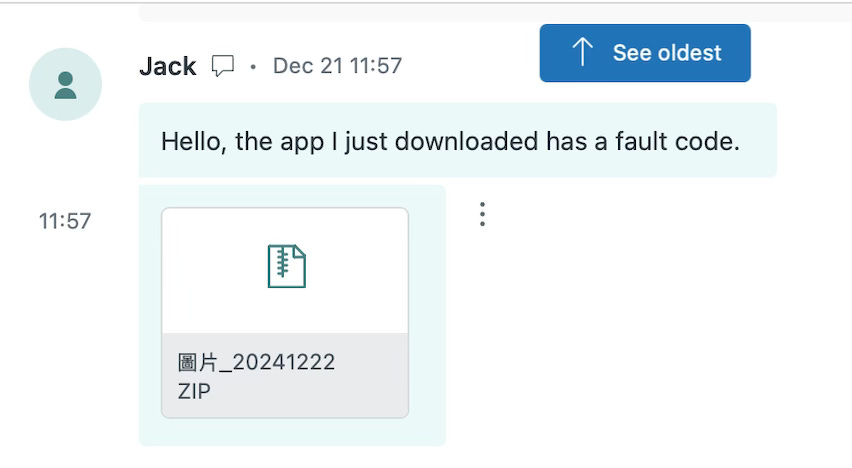
The pattern was the same: open a case and immediately attach a ZIP file with Chinese characters in its name, supposedly containing screenshots and additional details.
When analysed, these files brought us an unexpected Xmas surprise: free malware! For some, this might be the digital equivalent of coal, but for us, it’s a sign that we’re firmly off the cyber-naughty list.
Let’s take a look at our gift.
Not your usual Chinese tale
We’ve all heard of Chinese tales once in our lifetime, but this one is different and falls apart as a scam pretty easily:
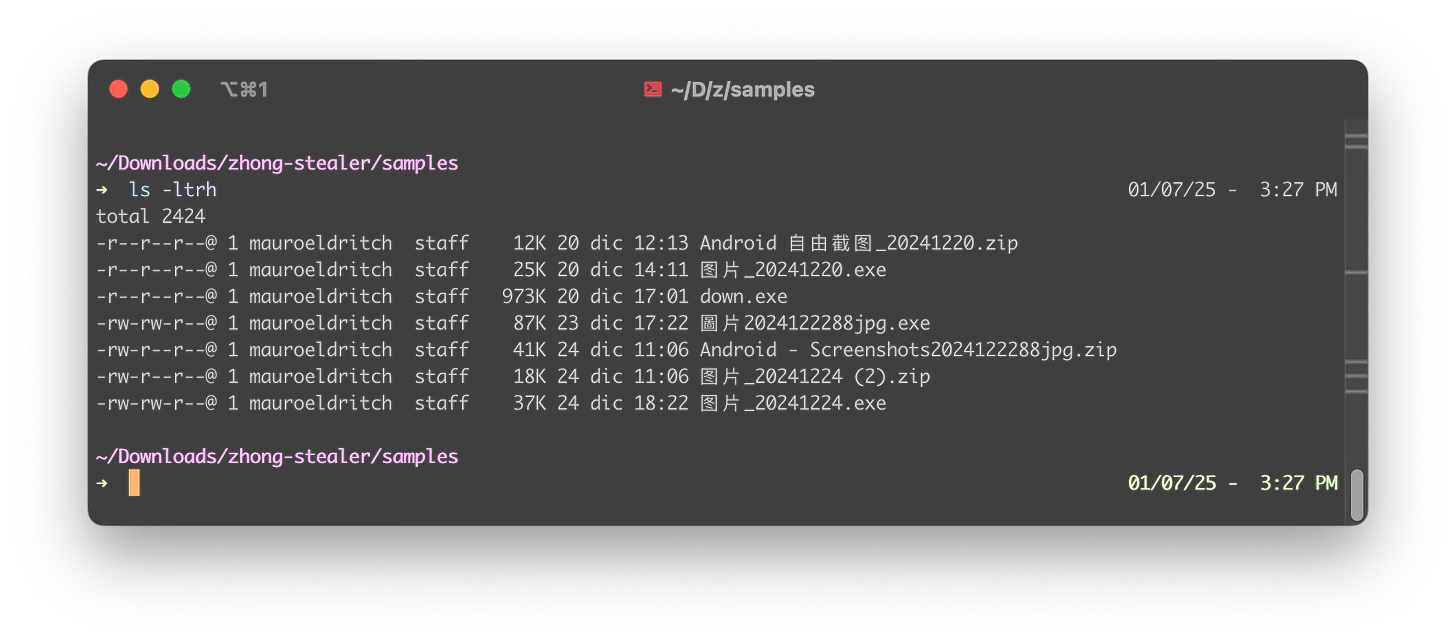
As stated before, the ZIP file names contain Simplified Chinese characters like “Android 自由截图_20241220” (Android Free Screenshot_20241220) or “图片_20241224 (2)” (Image_20241224 (2)).
Inside of them, executable files can be found, again, with Simplified and Traditional Chinese characters in their names like “图片_20241224.exe” (Image_20241224.exe - Simplified Chinese), “圖片2024122288jpg.exe” (Image2024122288jpg.exe - Traditional Chinese), or “图片_20241220.exe” (Image_20241220.exe - Simplified Chinese).
These executables communicate with servers hosted on China’s Alibaba Cloud.
And also for the little simple fact that we do not serve clients in the Chinese market…
So what are their intentions? Let’s find out, scalpel in hand.
恶意软件
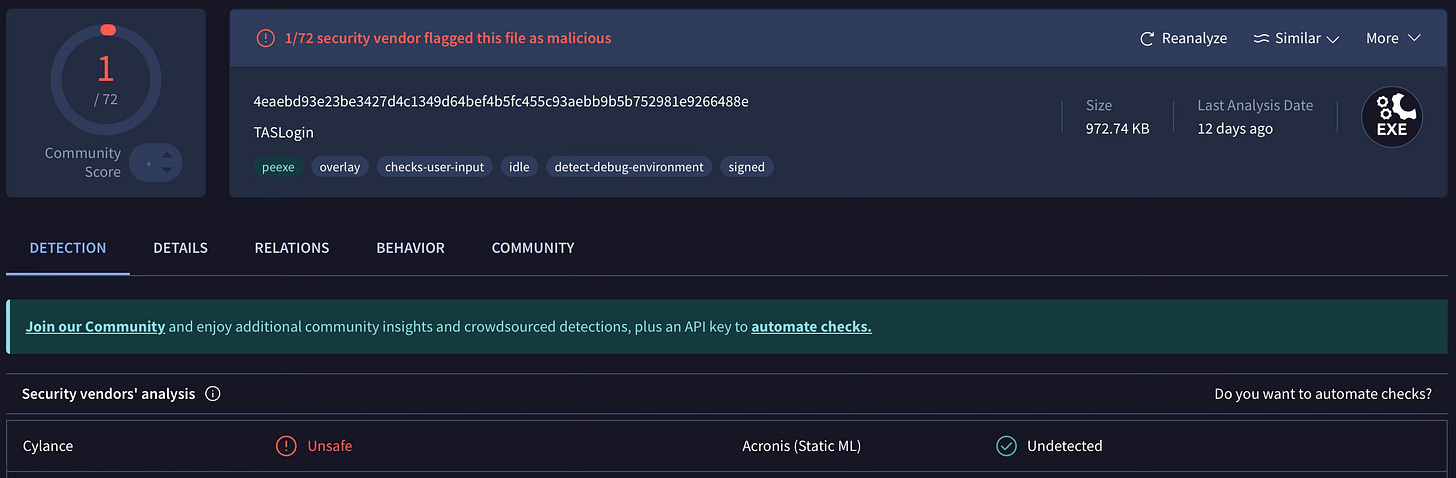
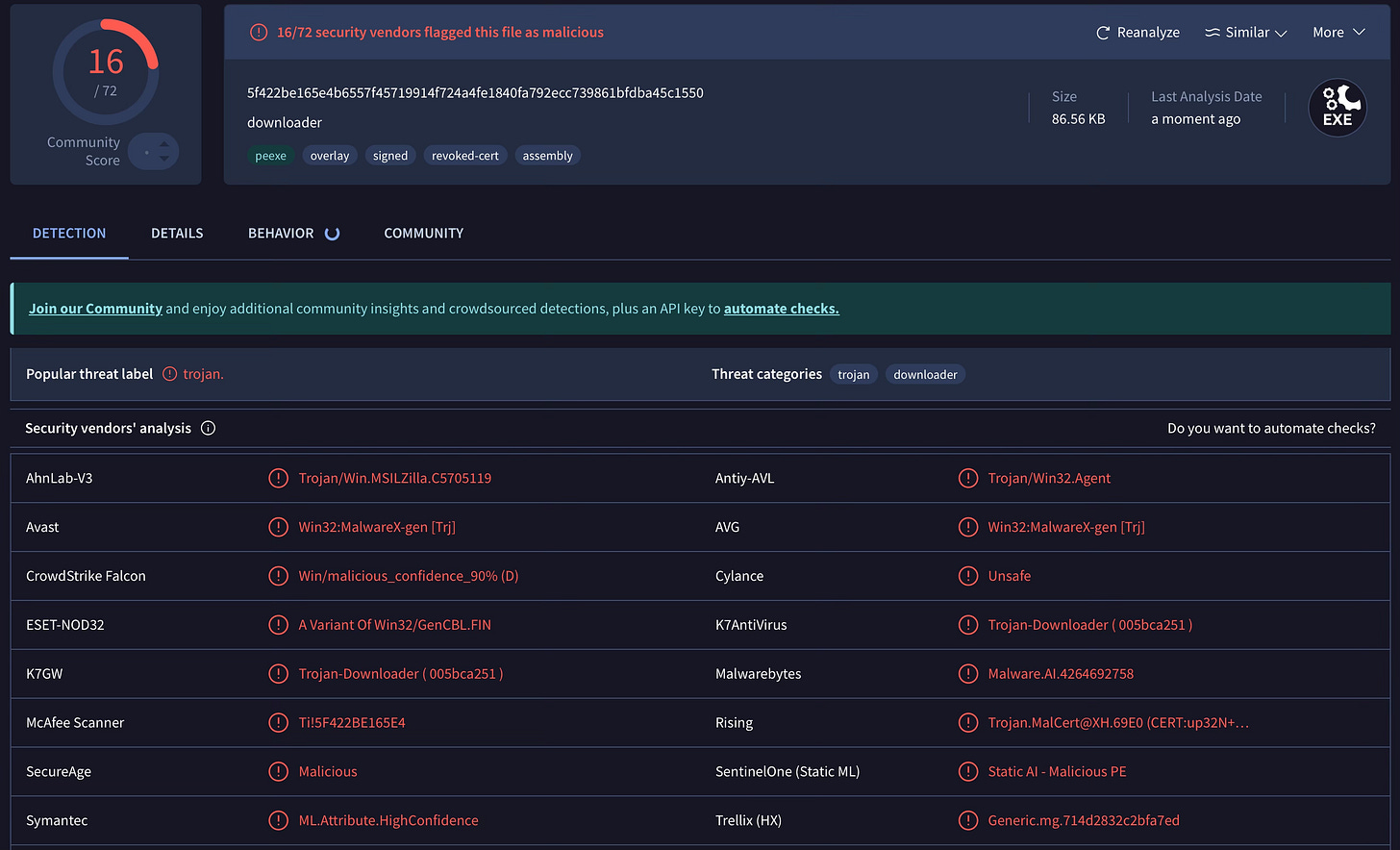
We started with the basics: was anyone else targeted by this campaign? Surprisingly, the malware components had very few detections initially, as shown below.
Over time, different strains of the malware (remember, we received three of them) began receiving more detections from various antivirus vendors.
However, all detections were labelled generically, without assigning a proper name.
Most of these names are heuristically generated, often appearing as placeholders like “AIDetectMalware,” “Malware.AI,” “ML.Attribute.HighConfidence,” “malicious_confidence_90%,” “Static AI,” or simply “Generic.”
These labels reveal little about the malware’s actual characteristics or behaviour. So, we took a closer look at the sample to give it a proper identity. We named it “中窃者” (Zhong Stealer). The word zhong means “central,” inspired by the original username from which we received the fake ticket.
Now, let’s dig deeper into its mechanics and see exactly how it works.
Zhong Stealer (中窃者)
The first thing our new friend will do in order to steal christmas is to download a new binary called “down.exe” from chinese servers hosted on Alibaba Cloud, along with a DLL library, a LOG file and a TXT file with mirrors just in case something goes bad acquiring the components. This process will then create a BAT file on the users temporary folder which will prepare the environment and communicate with a Hong Kong based server before continuing.
Then, the Christmas heist takes place. Zhong will start a recon routine on the system reading security settings, hostname, supported language (possibly to avoid attacking on specific regions), and then will add persistence via a Registry Key.
Then, it will start looking for credentials and sensitive data stored on browsers like Edge and Brave.
The rest is a well-known story: our Secret Santa turns into a Krampus.
To avoid falling into the same trap, remember: even on Christmas Eve, not every package is a gift. Let suspicious packages be handled by your security team—and don’t open them yourself.
Stay safe!
IOCs
FileHash-MD5:778b6521dd2b07d7db0eaeaab9a2f86b
FileHash-SHA1:ce120e922ed4156dbd07de8335c5a632974ec527
FileHash-SHA256:02244934046333f45bc22abe6185e6ddda033342836062afb681a583aa7d827f
FileHash-SHA256:1abffe97aafe9916b366da57458a78338598cab9742c2d9e03e4ad0ba11f29bf
FileHash-SHA256:4eaebd93e23be3427d4c1349d64bef4b5fc455c93aebb9b5b752981e9266488e
FileHash-SHA256:dd44dabff5361aa9b845dd891ad483162d4f28913344c93e5d59f648a186098
FileHash-SHA256:e46779869c6797b294cb097f47027a5c52466fd11112b6ccd52c569578d4b8cd
FileHash-SHA256:5f422be165e4b6557f45719914f724a4fe1840fa792ecc739861bfdb45c1550
URL:hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/TASLogin.log
URL:hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/TASLoginBase.dll
URL:hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/down.exe
URL:hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/uu.txt
email:zhongmaziil992@outlook.com
hostname:kkuu.oss-cn-hongkong.aliyuncs[.]com
IPv4:156.245.23.188
IPv4:47.79.64.228