Your Ad Here
Profiling a Malvertising campaign
Malicious Advertising
Malicious Advertising, or "Malvertising" is a trending threat with a broad target of victims: essentially, anyone who uses search engines. When a user searches for something online, most engines display ads or "promoted" results, typically positioned above the organically placed ones. Sometimes, if the UI design allows it, these ads blend in with the organic content, giving the impression that they are the most relevant (natural) option. Malicious actors are well aware of this and are willing to invest in purchasing ads with specific wording, often referencing well-known brands and apps, to spread malware or capture users' private information. In this article, we’ll profile a real malvertising campaign posing as a popular calendar service.
Block your calendar
It all started when Samer, one of our colleagues, warned us about a phishing site posing as Calendly, a popular calendar application available across multiple platforms. Like most people, he searched for the application on Google instead of remembering and typing its domain (after all, many of us trust our search engines not just daily, but hourly). However, this time, the results he received were peculiar. The top result — which turned out to be an ad — didn't lead him to Calendly’s official site but to a sophisticated phishing.
The ad displayed the official Calendly domain, and everything inside looked identical to the original site, except for the download links, which hid something that may not exactly help you block your calendar, but perhaps your entire system…
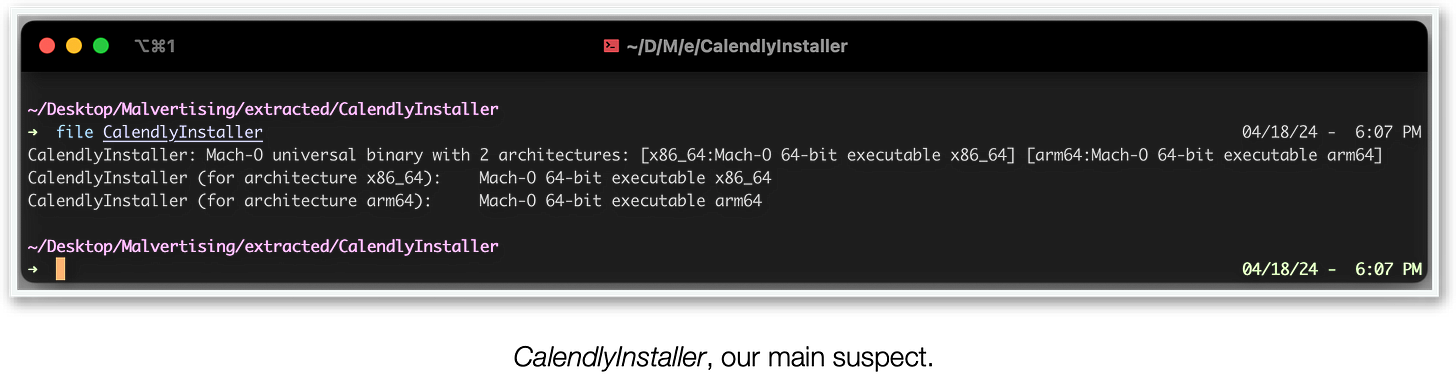
If your first thought was “malware” well that’s on me I set the bar too low. For the sake of simplicity we will only analyze the macOS strain of this malicious software. We start by downloading the “CalendlyInstaller.dmg” file linked on the landing page. Once mounted, the DMG file displays this creative and dangerous trick:
By default macOS prevents the execution of software from unidentified developers unless users “right click” (Command + click) and select “Open” from the contextual menu, which is what the malware is trying to trick users into doing. Bring your lab coat, let’s get our hands dirty with some malware dissection.
Almost the entire file size can be attributed to a single file: dictionary.txt which weights 64MB. This is a common technique sometimes referred to as bloating, where malware samples (which are usually compact) are packed along with other nonsensical files to increase their final size, discouraging certain antivirus solutions (and even entire platforms like VirusTotal) from scanning them. In this case, the dictionary.txt file contains latin text with no other purpose than to bloat the final product.
The malicious component seems to be CalendlyInstaller, a universally (x86_64 + arm64) compiled binary.
Let’s see what the experts have to say.
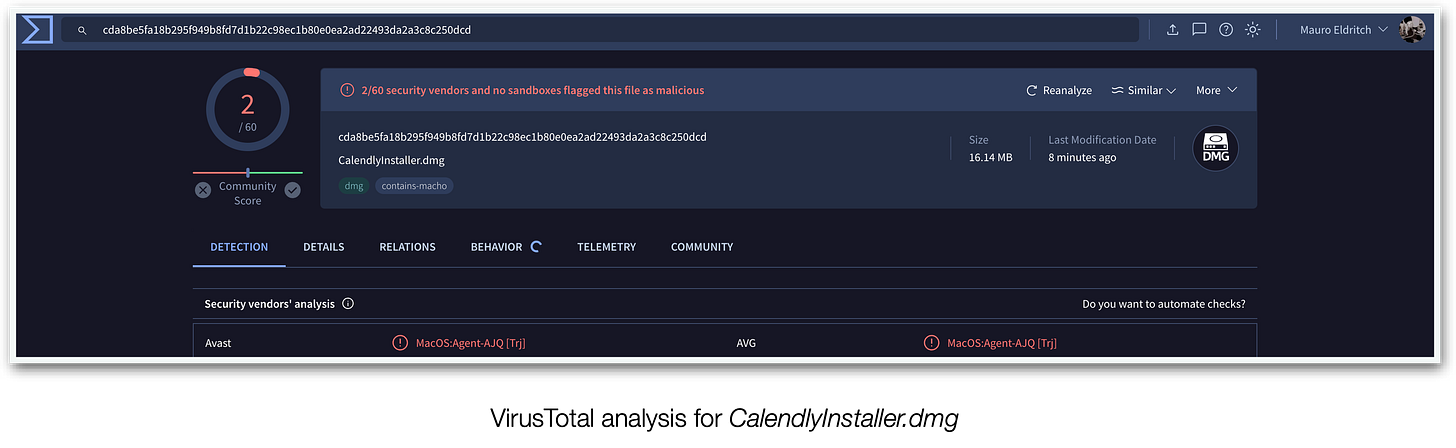
The DMG file is detected by only two antivirus solutions which label it as “AGENT-AJQ”. Let’s see if we have a better luck with the binary itself alone.
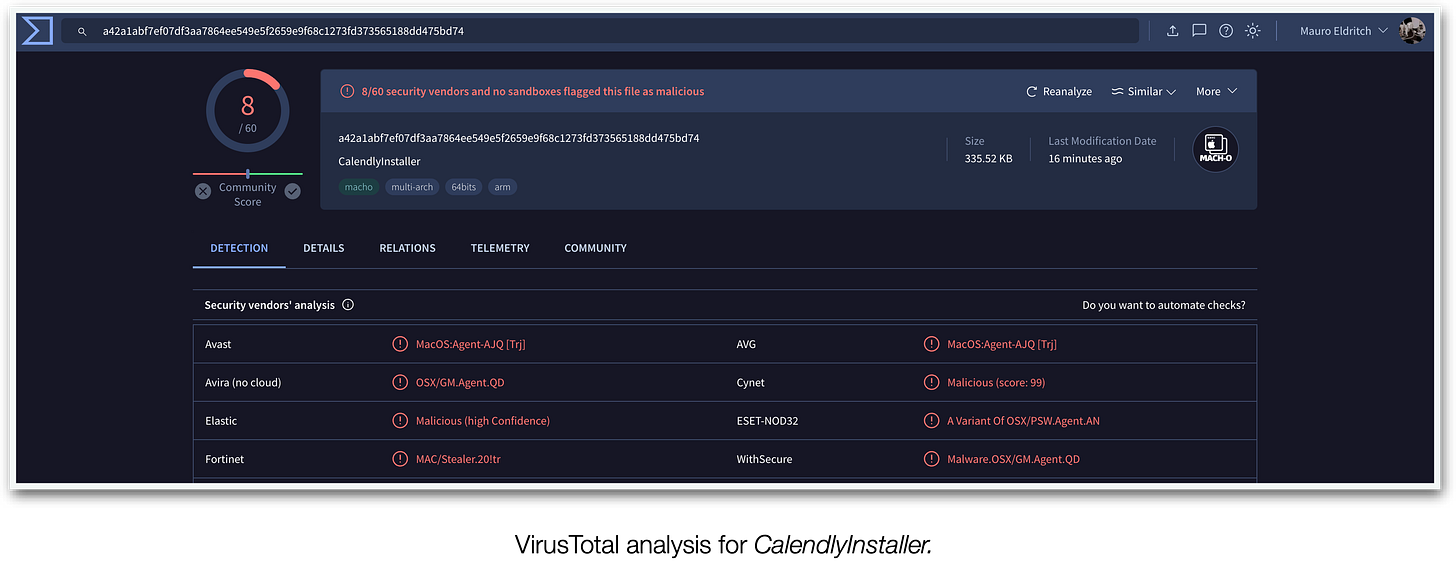
The binary alone triggers eight total detections, with different labels and names. One of them refers to this strain just as “Stealer” which is still very illustrative.
This was enough information to broadcast an intelligence pulse to warn the community about this campaign while we establish contact with the abuse team of Google and their registrar.
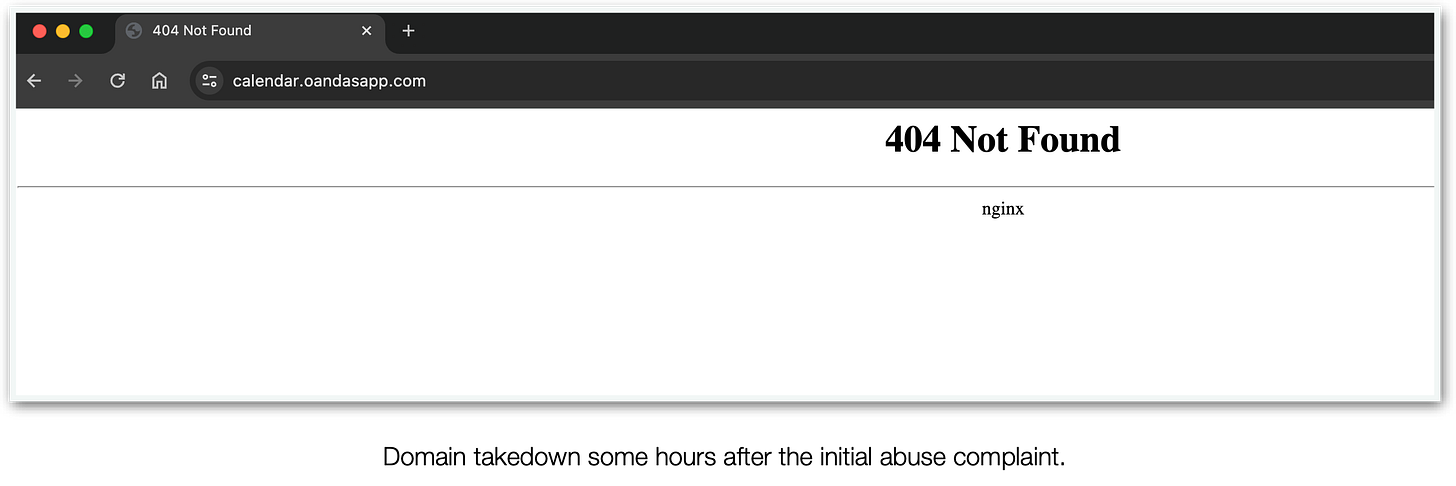
Just a couple of hours after our initial contact, we are safe to assume that the TA had not only his calendar blocked, but also his domain and ads account as well.
Malvertising is here to stay and its something we all should add to our cyber dangers bingo card. Bookmark your favorite sites, pay attention to your search results (even when the ads display the official site URL) or if possible avoid sponsored results at all when looking for a specific site, platform or app. Stay safe out there, and don’t get rekt.
Acknowledgements
This campaign was originally spotted by our colleague Samer Rida. A special mention to him for his quick reaction and reporting.
Appendix I: IOCs
Domain:oandasapp.com
Domain:calendar.oandasapp.com
MD5:2d872756a73528129bd60a808bcfcfee
MD5:dabcf1b16d7a0e60f4000c8b959802f8
SHA256:a42a1abf7ef07df3aa7864ee549e5f2659e9f68c1273fd373565188dd475bd74
SHA256:cda8be5fa18b295f949b8fd7d1b22c98ec1b80e0ea2ad22493da2a3c8c250dcd
IPv4:141.98.233.61
File:CalendlyInstaller.dmg
File:CalendlyInstaller