Final Chapter: Interview with the Chollima VII
Canaries and Quetzals
It has been a long year. We have tamed interviewed many Chollimas, torn apart plenty of their malware, and even managed to secure ourselves a place within their ranks, documenting their entire operation from the inside. A wild year, indeed.
But all things must come to an end, and it is time to sunset this saga. That said, it should not be a sad moment, because we are giving it the ending it deserves.
So, as usual: a North Korean walks into an interview…
Córdoba
When you think of Córdoba, Argentina, many things come to mind: the accent, the musicians, the festivals, the cuckoo clock, and even the UFO sightings. The last thing you would expect is a North Korean cosplaying as a cordobés, yet here we are. If we worked only with known knowns and the predictable, this saga would not exist.
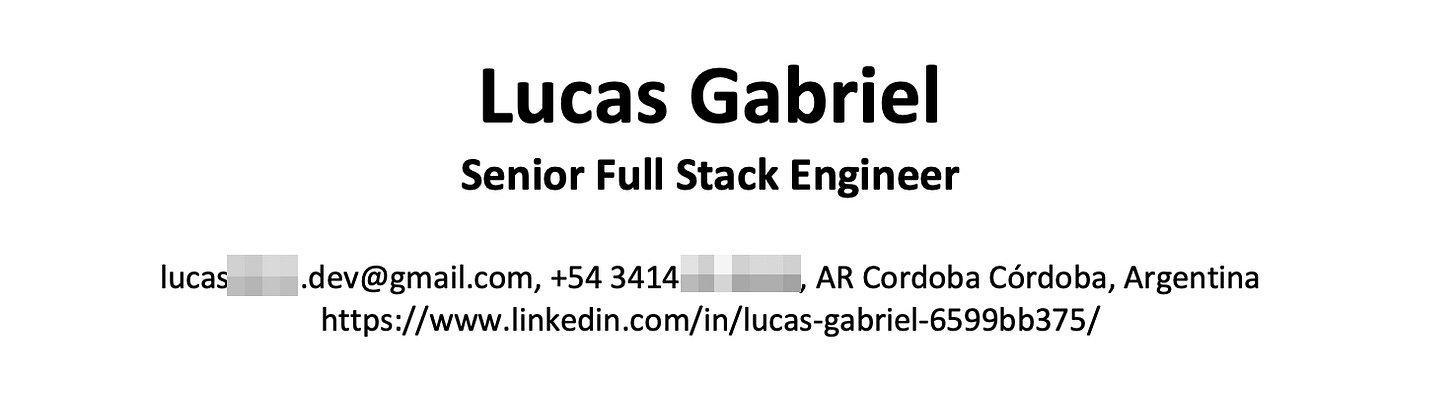
So that’s how we met Lucas Gabriel, a north-cordobés Senior Full Stack Engineer that applied for a position at our company.
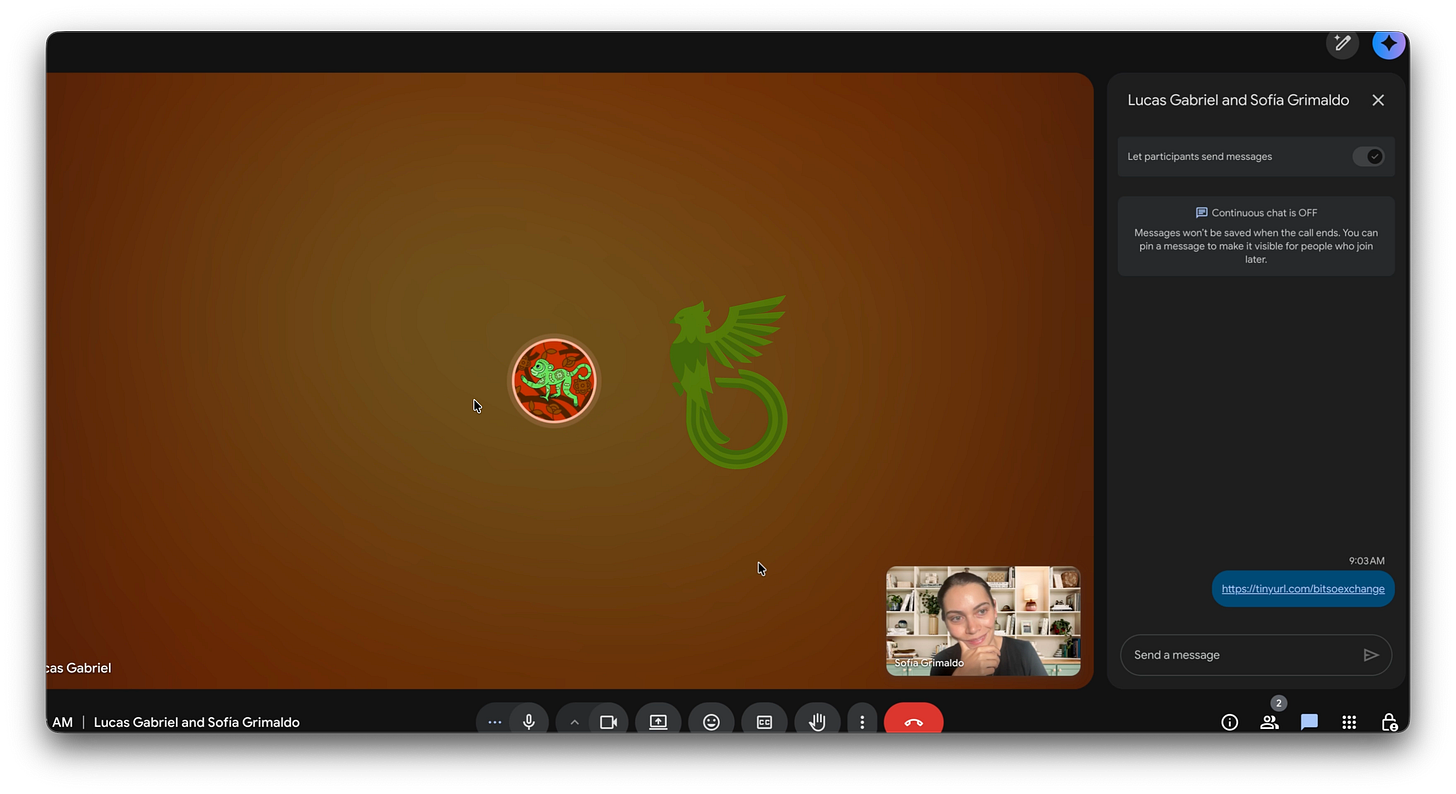
Sofía, our Talent Acquisition Specialist, met him for an interview, and things immediately stopped making sense. To begin with, Lucas seemed shy and refused to turn on his camera for reasons that will become clear later in this article.
From that moment onwards, the interview was a complete disaster. Suspiciously, he did not speak Spanish at all. When Sofía encouraged him to switch to his native tongue, he excused himself by saying that he “wanted to improve his engrish” (sic).
Sofía pressed on, insisting that the role required Spanish proficiency and that they needed to continue in Spanish. He reluctantly agreed, but after her first question he froze, as if struggling to understand what she had said, or perhaps waiting for an AI to auto-translate for him, something we had seen before. Unable to answer in a reasonable timeframe, he pushed again to continue the interview in English. When she declined, he simply vanished.
But that is not where the story ends. Notice what Sofía says at the end of the clip? For those who do not speak Cervantes’ tongue, like Lucas Gabriel, she says:
“Of course he’s already gone, but we got him”
and seems happy about it.
That is another detail that will become clear later on. Keep it in mind, together with the switched-off camera. Everything will add up in the end.
So far, for an APT (Advanced Persistent Threat), the whole engagement seemed unusually easy on our side. It felt like fencing with an inexperienced opponent each time, or as if we had an advantage no one had fully noticed yet.
I lean towards the second explanation, and since we have many loyal readers who have followed this series to this very day, I think we both deserve an ending with our very own parlour room scene (*).
(*) The classic climax where the detective gathers all suspects in a formal room (the parlour) to reveal clues, explain the crime step-by-step, and unmask the killer, solving the case.
The Manual
Many months ago, we started this series, Interview with the Chollima, after a DPRK agent posing as someone from a crypto company tried to spear-phish me into “working” for him. My supposed task was to fix a “bug” in his code, which was in reality laced with a malware called OtterCookie, which would later deploy InvisibleFerret (another malware) as his sidekick.
In that first chapter, I explained how I fully reversed the malware, played along just enough for him to believe I had taken the bait, and used that to pull him into a call where I confronted and recorded him.
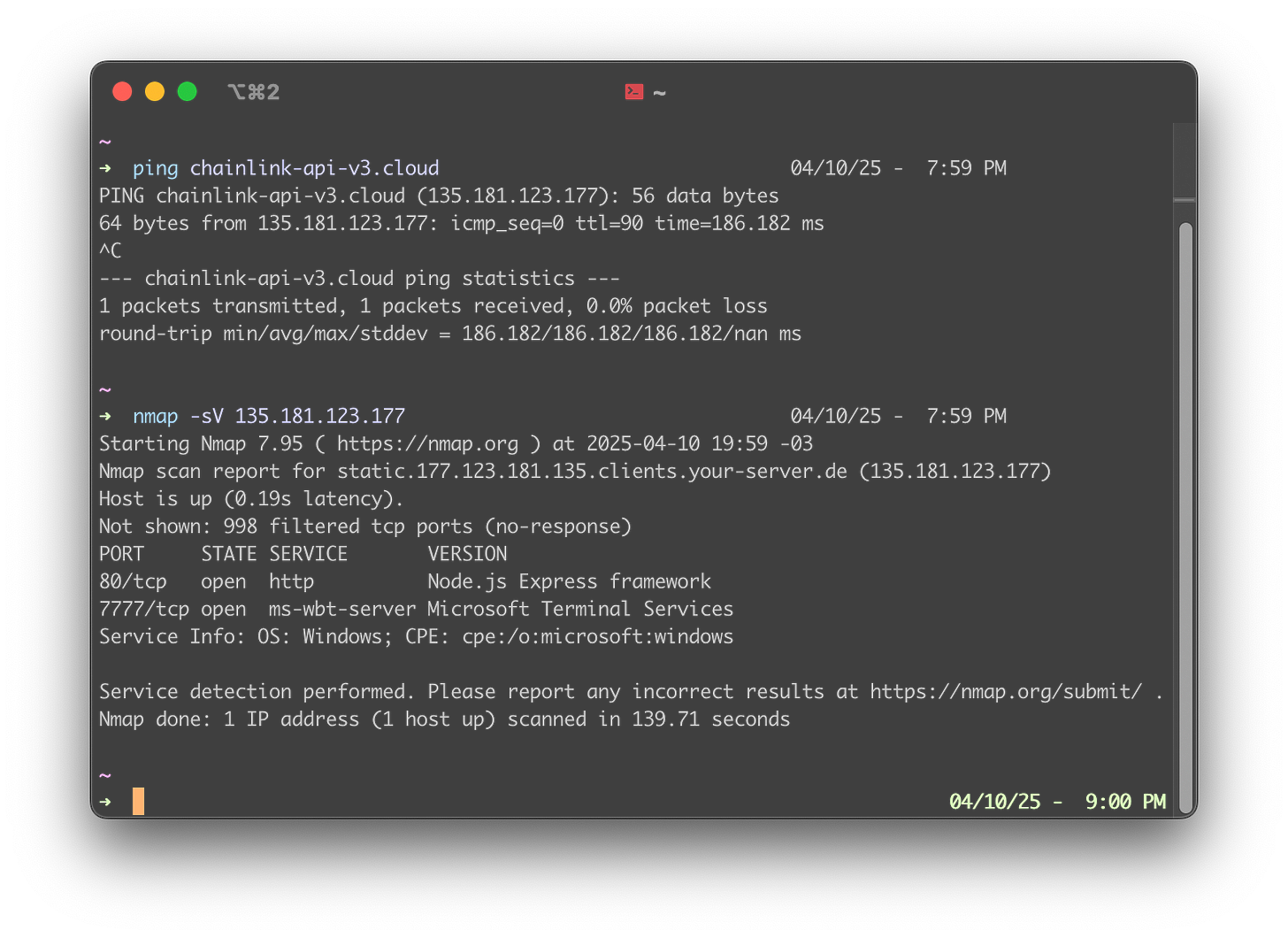
But that’s not the whole story, let’s take a few steps back. While reversing the malware, I discovered several domains referenced in the code. Scanning them revealed that he was running his services with Administrator privileges, and that a port hosting Remote Desktop Protocol was also exposed on a particular domain.
In my own words from the first chapter:
“The other service running on port 7777 is Remote Desktop Protocol, which allows us to authenticate, if only we had the necessary credentials.
But that’s a story for another day”
That day is today, so here is the full story.
I tried to tease this during my talk North Korea’s Fur Shop at DEF CON 33’s Malware Village, but only a few Mexican attendees actually caught the cue and came to see me after I left the stage.
Let’s say that SWIM (Someone Who Isn’t Me) found numerous hardcoded credentials inside certain DPRK malware samples, all of them simple and predictable, and decided to try stuffing them into the Remote Desktop Protocol login window.
That SWIM got access after only a few attempts and ravaged through the filesystem like a ferret, a pretty visible one, and found some tools. Some of them were classics like OtterCookie, while others were cheaply programmed Drainers, some even containing hardcoded DB credentials to remote servers, which made dumping them trivially easy.
Let’s say that SWIM also stumbled upon a weird short document, something between a homemade manual and a set of notes from one operator to himself or another on different topics:
How to set up their online personas and emails, strangely suggesting the use of “.dev” or “.work” in their handlers,
Enforcing the use of specific VPN services (such as AstrillVPN) and residential proxies, resorting to VPS providers only as a last option,
Advising them to claim they were based in Los Angeles or Texas,
Recommending AI prompts to create “social media posts” to maintain an active online presence and build their network, and to comment on compatible job postings something like “I believe I am a good fit for this position”.
I was able to confirm this (strange) point by looking at a DPRK’s profile latest interactions on LinkedIn, which are public.
Sharing a list of excuses to deal with awkward social situations, such as not speaking the language of the country they pretended to be from: “tell them you left as a child because your father worked abroad”.
Do any of these points sound familiar? If you have been following this series, probably all of them. This gave me early warning about their behaviour, and it also explains why their social media AI-slop posts, handlers (“.dev”, “-work”, “-projectname”), backstories, excuses and claimed locations are always the same among all candidates. This was their playbook, kind of.
Sadly, at no point did that short document shed any light on why they run away once they are discovered and delete all their online accounts, as I see this as a standard procedure.
But adding loathing to ridiculousness, one last point caught my eye: a suggestion that “female recruiters are easier to deal with [to fool] than male recruiters”. A bold claim, considering how a woman (Sofía) caught every single one of them live on camera. One of them was even shaking like a leaf during the interview.
I’d say she was not exactly “easy” to deal with. Speaking of which.
Fight like a girl
With internal intelligence on how they operate, my team and I moved ahead and blocked their entire toolset: the IP ranges of their VPN providers, the residential proxies they relied on, the exit nodes of their remote desktop tools, and very specific ASNs they used. I was genuinely curious to see what they would try once they realised that none of their tools or hosts could reach us anymore.
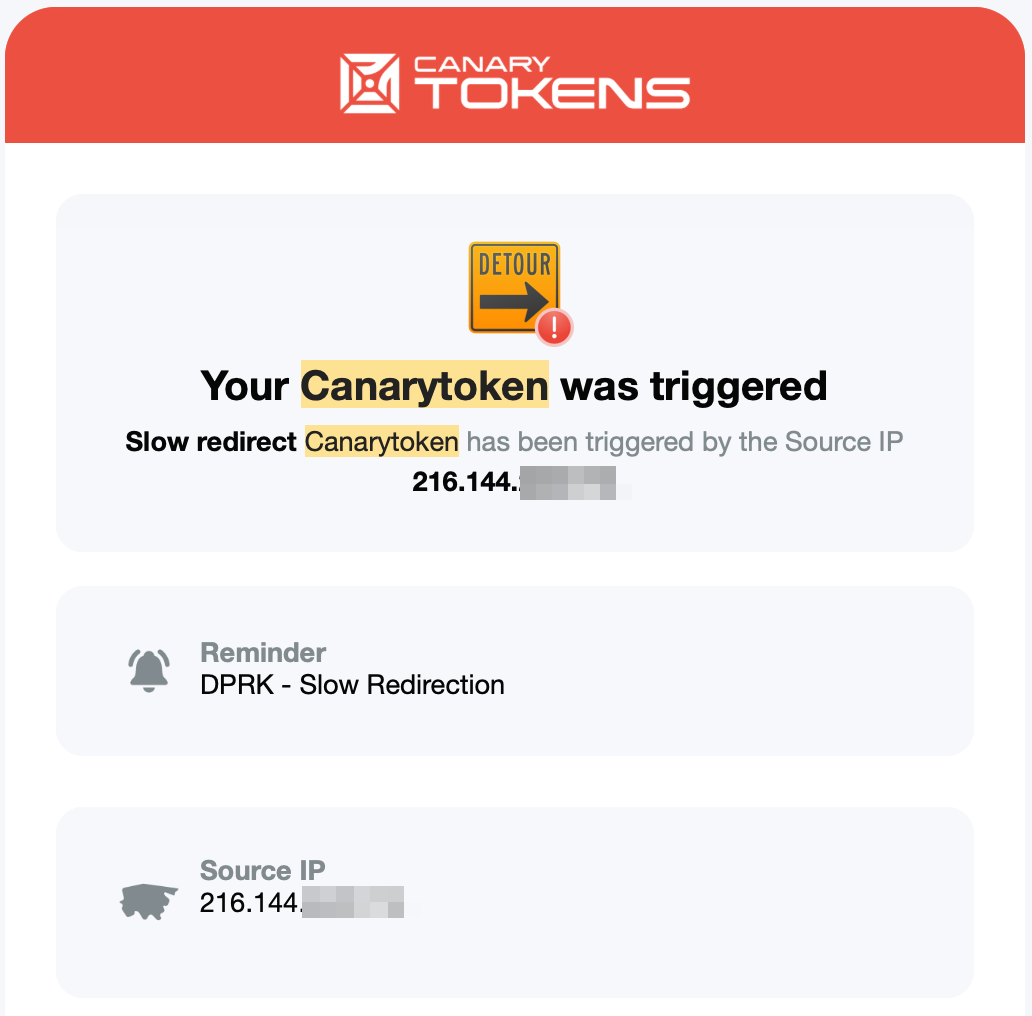
I spoke with Sofía and shared a set of canary tokens with her: links, QR codes, documents and other measures that, once opened, would privately send us all sorts of information about whoever activated them. Ideal for hunting Chollimas, Moles and other vermin.
When our north-cordobés friend joined the call, Sofía shared one of those canaries with him under a specific pretext, and he fell for it instantly, triggering it.
Easy to deal with, sure thing.
Now do you understand why she said, “Of course he’s already gone, but we got him”?
I received a notification via email about the trap being stepped on, so we started investigating.
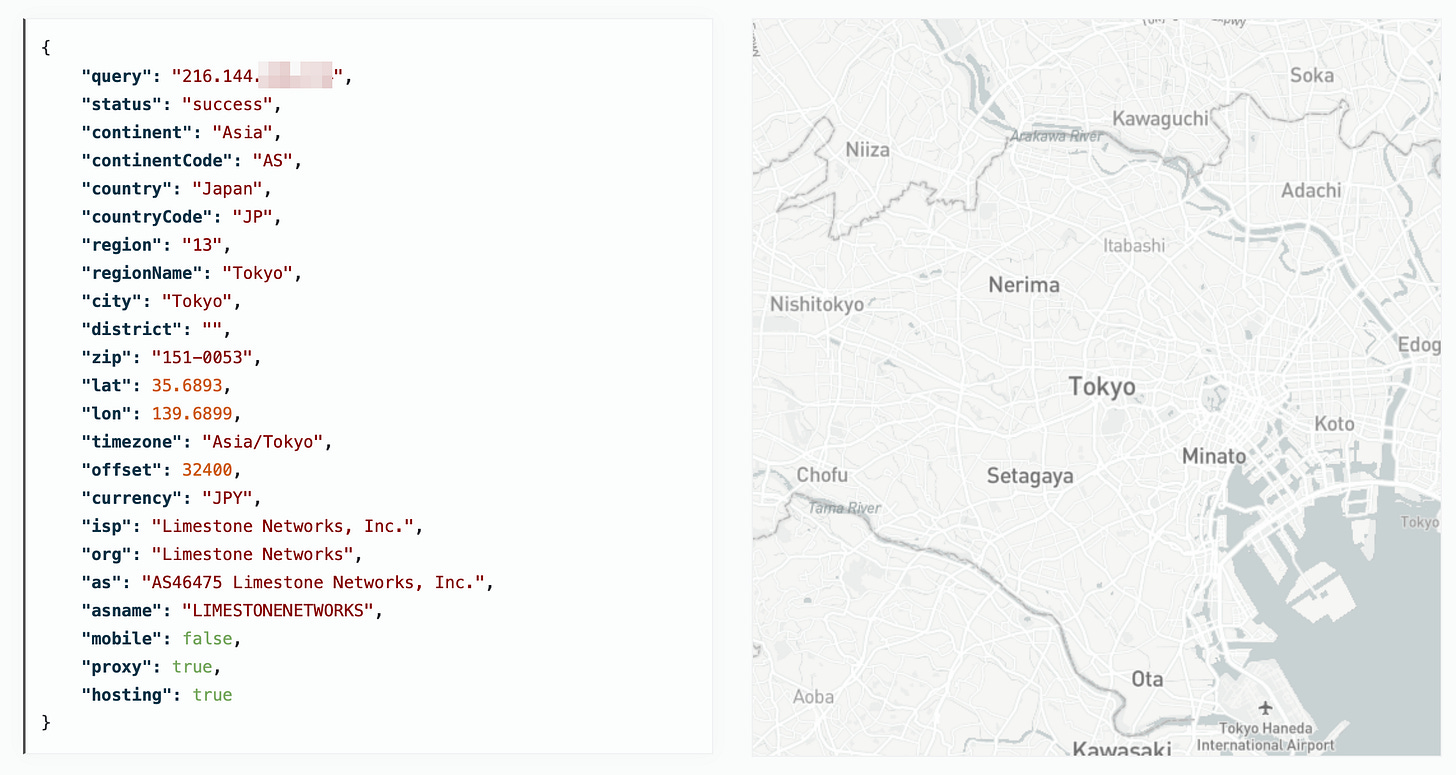
He disappeared, but not without leaving behind an interesting trace. He was using a VPS located in Japan, although some tools place it in the United States, owned by Limestone Networks. This aligns neatly with what was described in the manual: when everything else fails, they are instructed to fall back on spinning up VPS instances. Having already blocked the providers they rely on most, this appears to have been their second choice.
The IP address itself is not important, even though it had no prior records across intelligence platforms, nor is the fact that they were using a VPS as a bouncer, which again, we already knew from the manual. The point, echoing what we have shown in previous articles, lies in their disastrous OPSEC and just how gullible they are.
That last part, them being a herd of gullible pony-heads, is particularly interesting. They will believe almost anything you tell them, which is precisely how we were able to escalate from talking to them daily on Telegram/Discord to observe them from the inside for months. During that time, we learned a great deal from their perspective, and not only on the technical side.
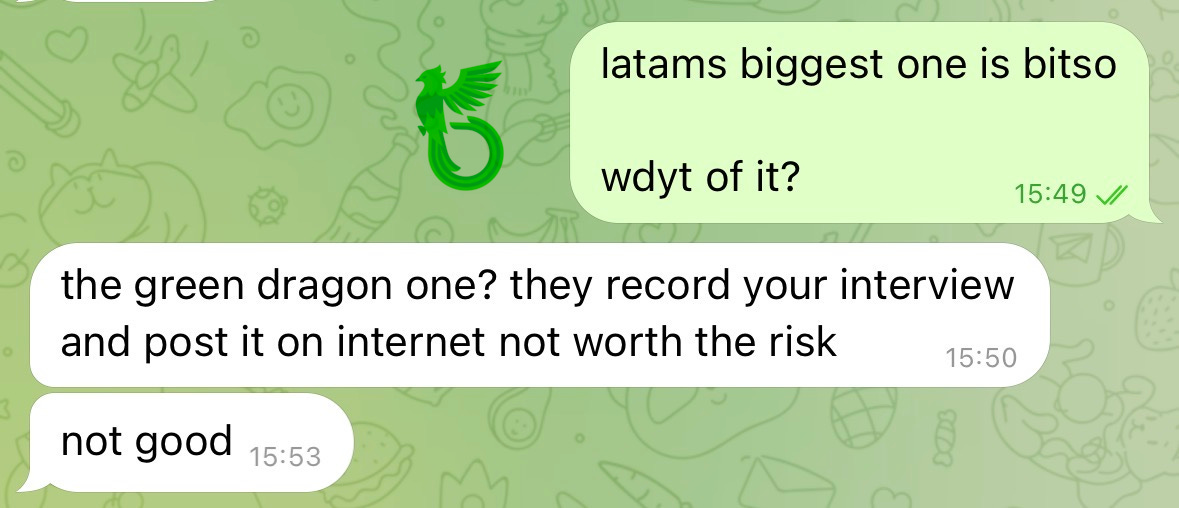
One detail that has stuck with me ever since, and that might explain why Lucas did not turn on his camera this time, came from an internal chat I had. It said that if you attempt to interview with a specific company whose team has a “green dragon”, “they will record your face and post it on the internet” and that was “not good”.
I am still trying to figure out what kind of monsters would do that to innocent job-seekers.
The End
This saga ends here.
The intel may be kept private, but the laughs should always be shared.
Stay safe.
Don’t hire spies.
Fight like a girl.
And don’t get rekdt.