Interview with the Chollima IV
We put the "Famous" in "Famous Chollima"
Some researchers like collecting indicators of compromise; others prefer watching silently and drafting indicators of activity, analysing their adversaries' behaviours and reactions.
I'm more in the second group. A threat actor's activity can sometimes yield (or help you infer) interesting information such as their level of veterancy.
Indicators of veterancy are those that tell you "this man here, it is not his first rodeo". Look at things like staying calm under fire, kind and educated communication (especially during extortions), and overall patience. These are things that separate bunches of Discord SIM swappers from long-time criminals and APTs.
Truth be told, the only way to discover these indicators is by engaging with threat actors, and what we learnt from doing so with the Chollimas is… well, disappointing to say the least:
Nervous: They are natural liars, and very bad ones.
They get nervous when questioned (like that kid the other day tweaking live on camera).
Their lies can’t stand basic questioning.
They blow up everything when fleeing (fake profiles, portfolios, their entire digital persona).
Backup: If one of them messes up, prepare for a quick follow-up.
Just as we saw in our last interview, a first candidate showed up wearing exaggerated AI filters and got rejected.
The very same day, another one showed up wearing a lighter filter.
One-up: If the backup plan fails, prepare to meet a bigger and nastier Chollima. Someone more experienced, confident enough to seek revenge for what you did to the other pony-heads (lovely little Chollimas).
This happened to us thrice:After the failed QRLog outbreak, where they attempted a follow-up attack a year later with another division using the same tactic and an improved malware.
After Interview with the Chollima I, they tried to attack me directly again, posing as a recruiter from Lockheed Martin.
After Interview with the Chollima III (yes, just two days ago), they sent a more senior Chollima to avenge his little pony-heads, whose faces we made viral all over the internet, including an article for HackRead.
And yes, this just happened less than an hour ago.
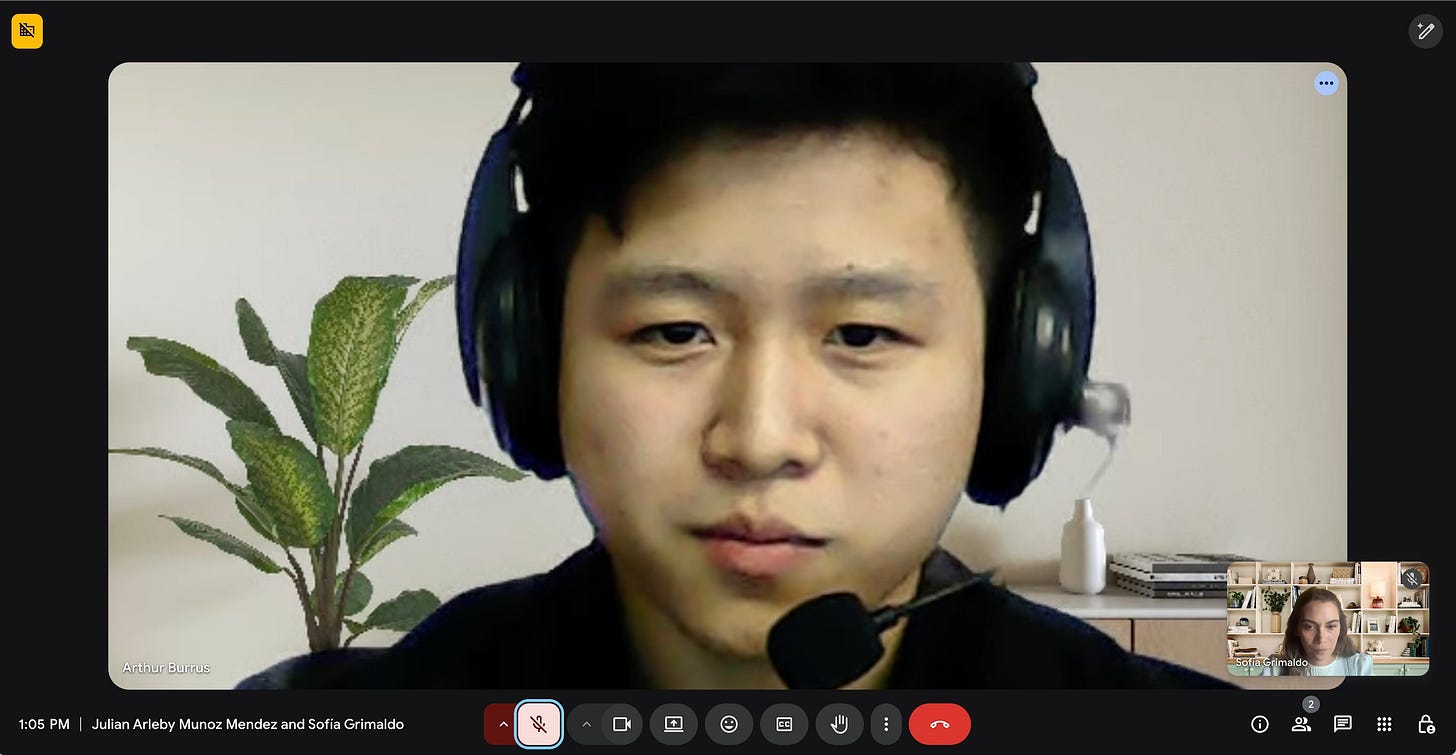
Dear readers, meet “Julián Arleby Muñoz Mendez”, Senior Chollima from the DPRK who calmly and bluntly decided to take an interview with Sofía, our Talent Acquisition Specialist, the same one that discovered his little ponies just two days ago.
“Julián” stole a resume and a portfolio from a Senior Full Stack Engineer from Colombia and tried to pose as him in order to gain a position at our company.
Born and raised in Colombia, “el señor Julián” does not speak a single word of Spanish, which is, once again, odd to say the least.
“I was sent abroad to Singapore from a young age” he states, “but I’m now once again in Colombia”.
Curious geographical choice, but I’ve seen this trick before: it is used to eventually match any timezone anomaly we could ever catch, as Singapore is in GMT+8 and North Korea in GMT+9.
Him not speaking a single Spanish word, along with the strange background story and added to the recent events, may tell us this is a dead giveaway of Chollima activity.
But for us at the Quetzal Team, who see the devil in the details, it is another thing.
Maybe, just maybe, it’s because this cattle-head stole Julián’s name, but forgot to switch identities and entered the meeting under the name “Arthur Burrus”.
An error like this is the typical indicator that this is probably not your first rodeo, but should be your last.
I hope you enjoyed this short article. We are the Quetzal Team: we put the “Famous” in “Famous Chollima”.
IOCs
URL:https://www.linkedin.com/in/julian-mendez-working0628/Yes, the profile URL says “-working”. I’m still picturing what other reasons I would have LinkedIn for.