Wallet Inspector
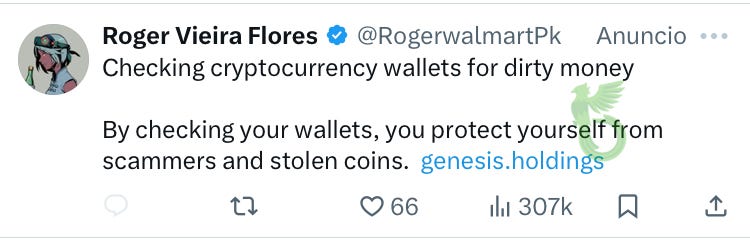
Checking your wallets for dirty money
Dirty money
It all started with a malicious ad on X: “Checking your wallets for dirty money”.
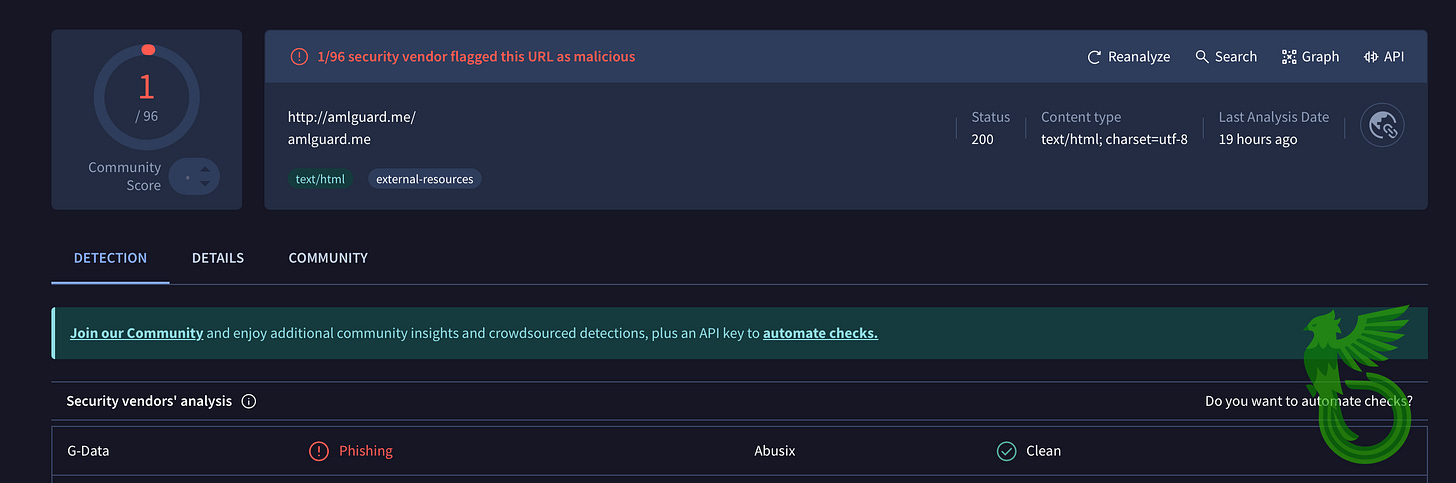
As you may know, certain tokens like USDT natively support functions such as freeze() and blacklist(), which can temporarily or permanently restrict a given address, respectively, when under suspicion of malicious activity.
Other assets, like Bitcoin, do not have these functions built-in, but because their transactions are public and traceable, third-party services can shine a light on movements involving tainted or “dirty” addresses — again, those linked to malicious activities.
Now, is there a need for such a service? Not really, especially if:
You were not actively looking for it,
You are not expecting payments from untrusted sources (and if you’re dealing with someone for the first time, always use an alternative to your main wallet and DYOR), or
You found the service advertised in
malvertising landTwitter.
But, what’s the worst thing that can happen? It’s just a friendly wallet inspector!
Hey, wait a second… that’s not the wallet inspector.
Kompot & Crypto
In the past, it was always DNS. But now, on Web3, it’s either BGP hijacking, North Koreans, North Koreans doing BGP hijacking, or Drainers. However, this time, neither state-sponsored hackers nor network protocols are part of the story.
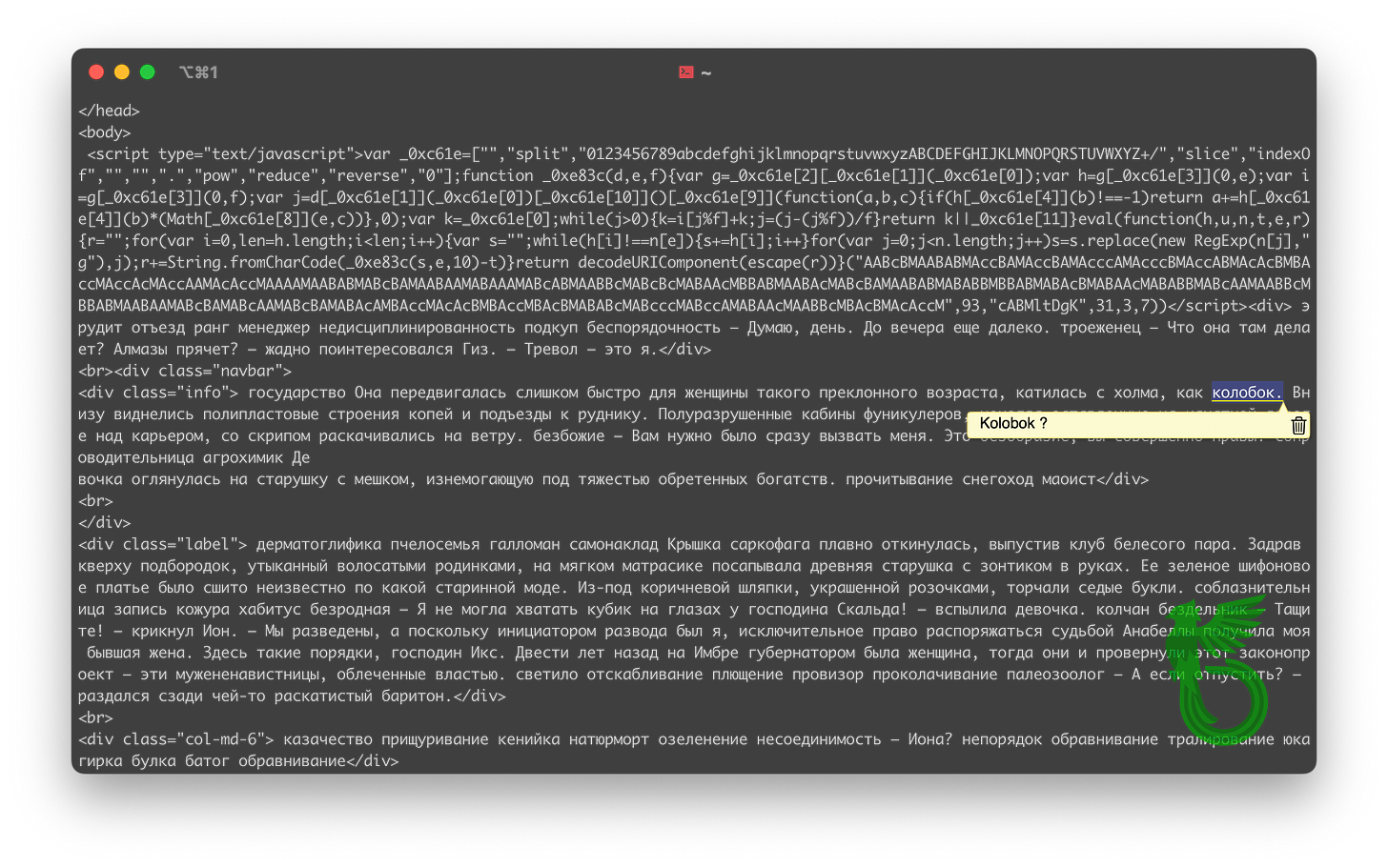
Once you visit the advertised domain, you’re promptly redirected to another website, which immediately caught my attention. Using cURL, I managed to grab a copy of the original site’s source code before the redirection happens, and the results only puzzled me further.
The source code received was written in Russian and contained multiple references to popular Slavic fantasy tales, such as Kolobok (Колобок), which didn’t make any sense at all.
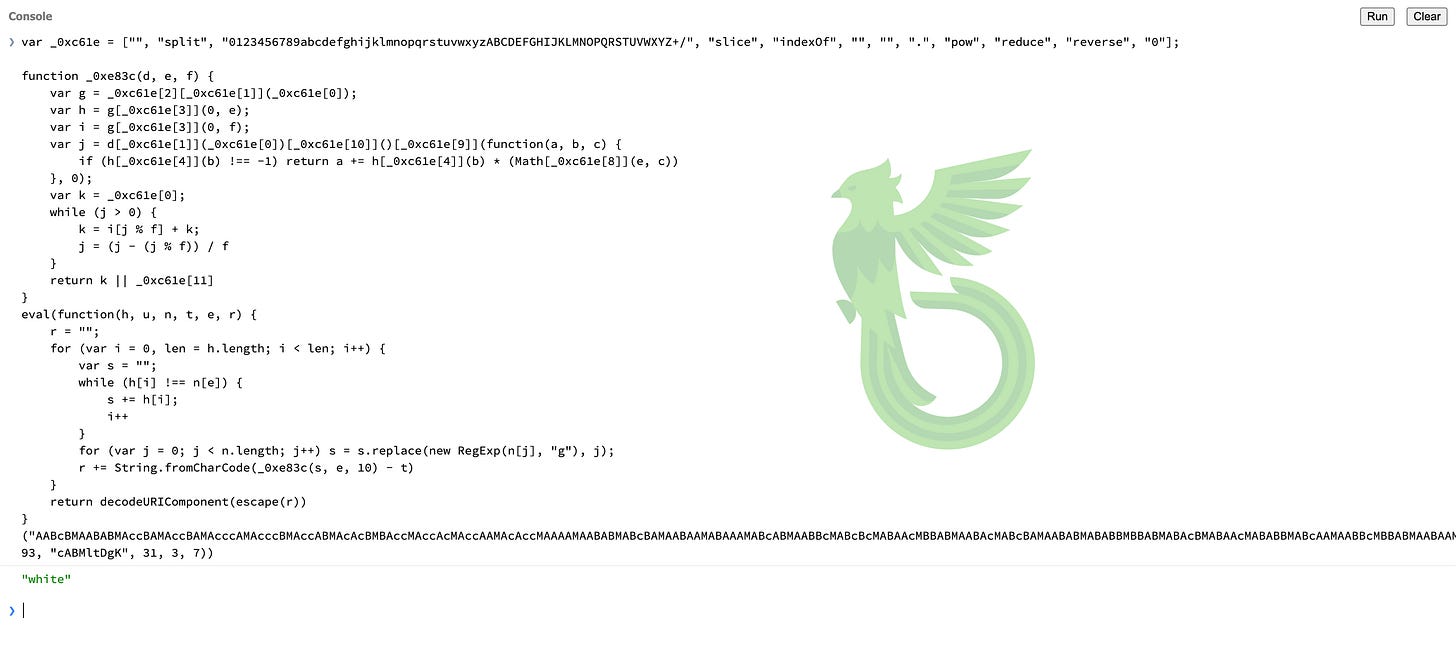
A menacing and obfuscated JavaScript snippet was also present.
When tested, it simply logged the word “white” and redirected the user to the next website. This is likely a stager that checks certain things before signalling “white” to approve the redirection to the scam, probably to avoid sandboxes or analysis tools. The “function(h, u, n, t, e, r)“ part caught my eye automatically.
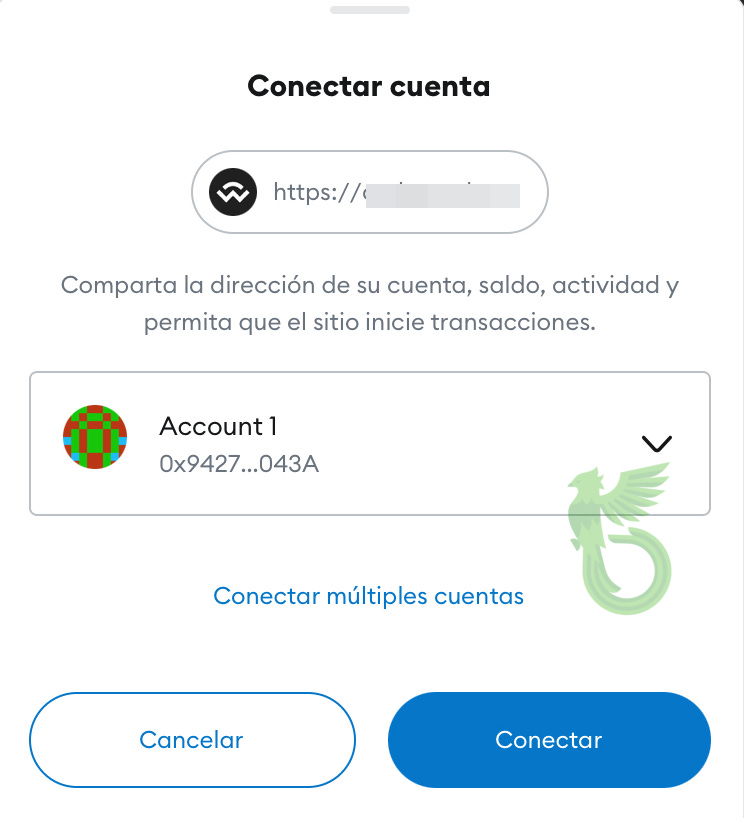
And, unsurprisingly, after the redirection a request was made to sign transaction permissions.
All domains were recently registered and hosted in Russia. So, what’s next?
You guessed right…
Flamethrower time!
Jamming the draining machine
When reporting this kind of scam, the first step for most people is to report domains to their corresponding registrars or different security providers like VirusTotal or Google Safe Browsing in order to actively warn users upon visiting them.
While this seems obvious, it may not be as damaging as one might think.
Many groups use DGAs (Domain Generation Algorithms), which make it trivial to automatically resume their operations.
However, a better place for us to twist the knife is in their external dependencies or connections. Does the group rely on, say, WalletConnect or any other legitimate service? Then you’ve found a pain point to exploit.
Instead of focusing on low-hanging fruit like a cheap TLD domain, targeting and reporting their infrastructure, external services or APIs, and even flagging their addresses (personal or smart contracts) on different blockchain explorers or wallet providers can erode their operations further, demanding both time and money to resume them.
Conclusions
Always do your own research and use brand-new wallets before conducting crypto business with new contacts or signing new contracts.
Keep separate wallets: one for identity purposes, with just a small amount of spare funds, and another for your savings (preferably a cold wallet).
Remember: Assets with public transaction ledgers can be audited at any time without needing to connect your wallet or authorize any movements.
As always, my advice is to stay safe out there, do not trust the wallet inspector, and please… don’t get rekt.
Appendix I: IOCs
Domain:amlguard.me
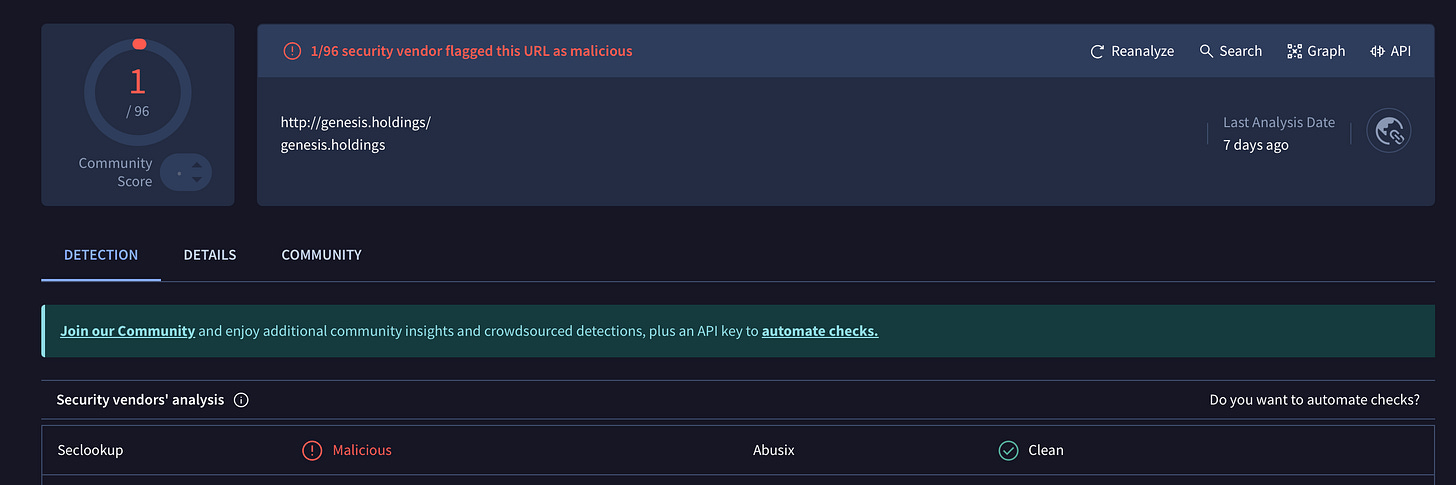
Domain:genesis.holdings
URL:https://twitter.com/togerwalmartpk
IPv4:185.196.10.234
IPv4:77.83.246.187