Hostage situation
When the President herself asks for your help
Yes, that’s me.
You’re probably wondering how I ended up in a Zoom call with the President of Mexico, her generals, and high-level officials.
Just a normal day at the office.
Hostage Situation
It all started with a call to our CEO from an official number belonging to the Ministry of Foreign Affairs (SRE). They politely asked if he could take a call from the Secretary of Defense. Upon agreeing, the conversation moved first to WhatsApp, then to Signal.
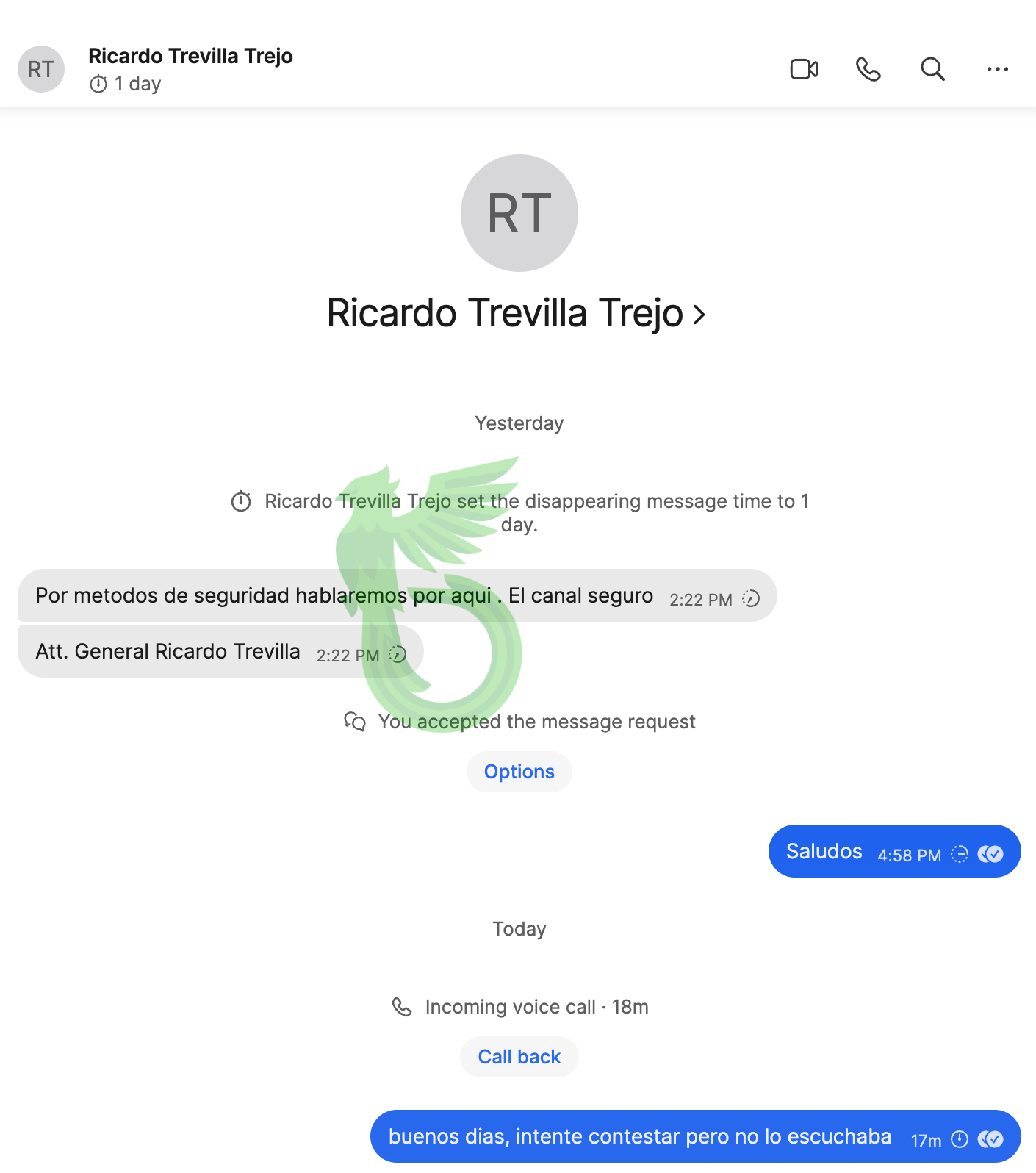
On Signal, he received a message supposedly from the Secretary of National Defense, General Ricardo Trevilla Trejo. The message claimed to urgently need our cooperation and invited him to a Zoom briefing.
Fearing our old fencing comrades might be back for a rematch, we agreed I should go first and join the call. Just in case.
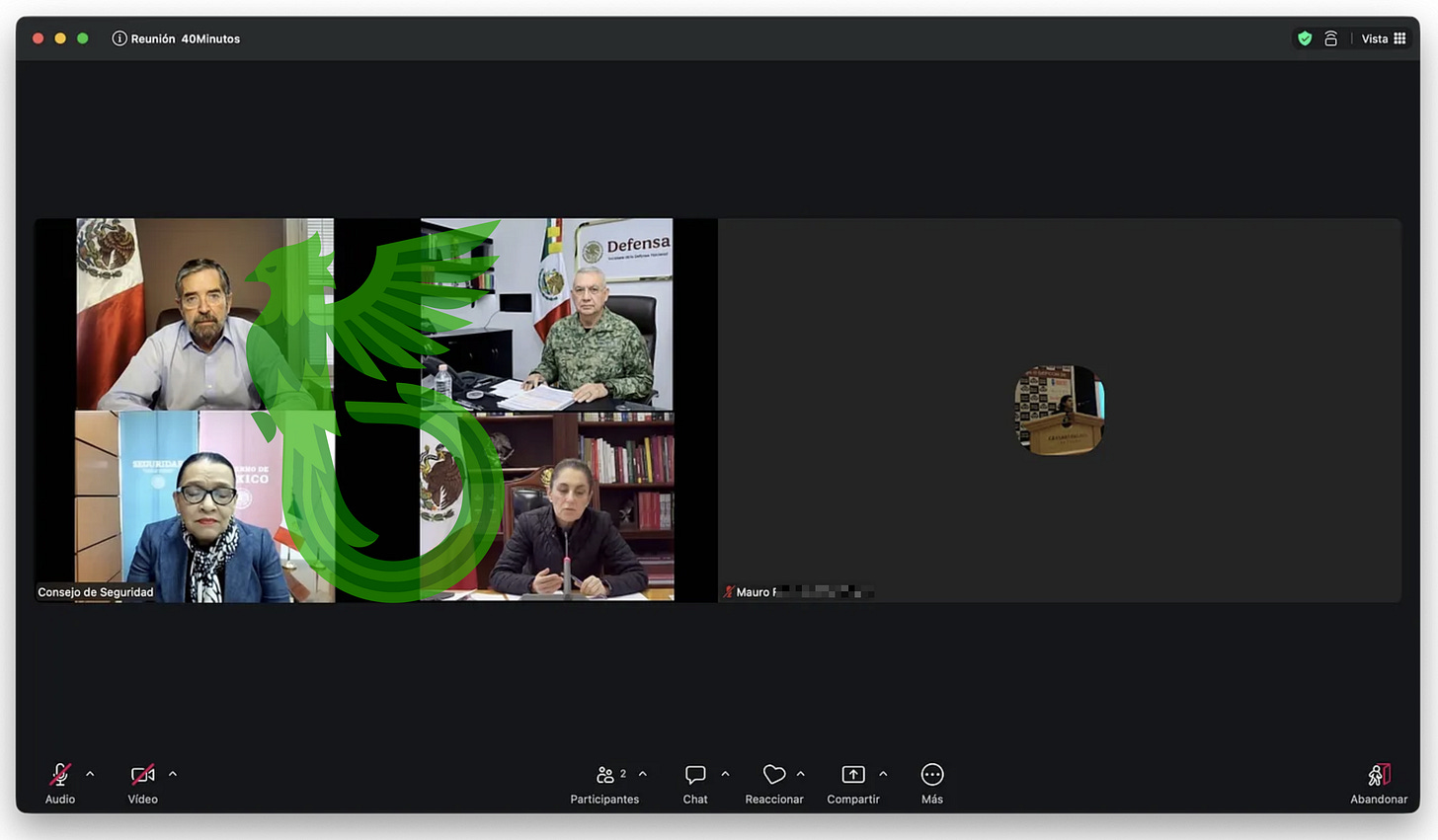
But as soon as I joined, the caller’s webcam activated automatically and began playing a deepfaked video showing Mexican President Claudia Sheinbaum, General Trevilla Trejo, and other cabinet members in what appeared to be an emergency meeting (translation below).
They discussed a hostage situation involving three Mexican citizens, stating that while they usually refuse to pay ransoms, this time would be an exception. They also expressed a desire to handle the matter discreetly, asking for everyone’s cooperation and assuring that all contributions would be appreciated and repaid once the crisis was over.
At this point, we were already involved in the negotiations without being formally asked. And while I don’t have the authority to release payments or negotiate this kind of crisis, I wasn’t going to miss the opportunity to tell all of LinkedIn about the 10 valuable lessons hostage negotiations taught me about B2B sales.
Technically speaking, the deepfake was flaky, but overall, the setup was solid. They were spoofing real phone numbers, impersonating the right people, and spear-phishing a high-value target.
Far more advanced than other threat actors we’ve fenced with in the past.
So, as a Threat Management Specialist, I had to manage this threat… in a special way.
Presidential Crisis
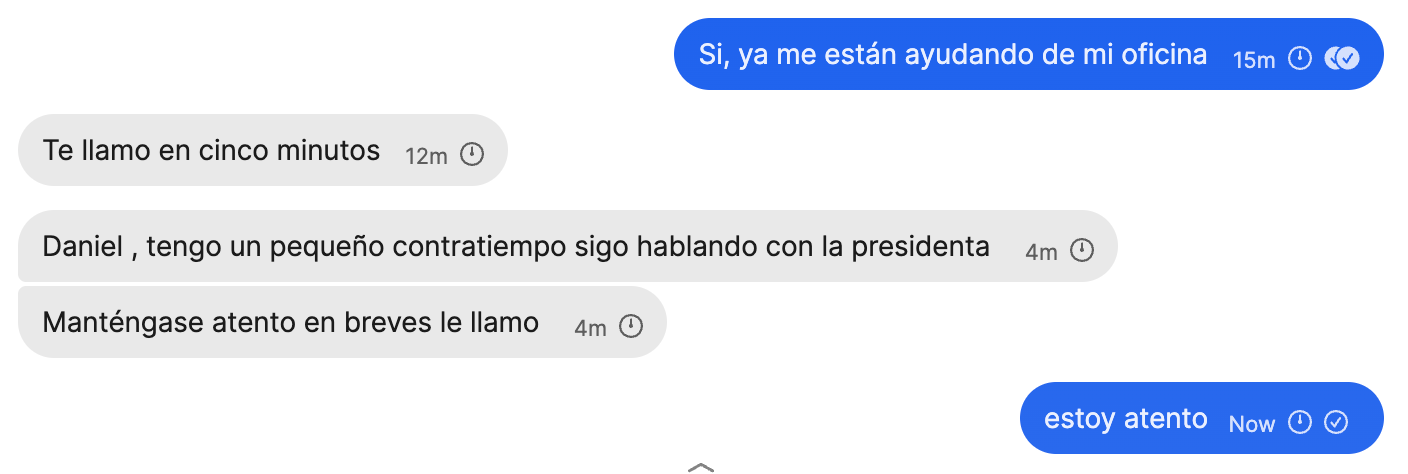
Time to rescue those hostages. We’ll bring you back home boys.
Our first move was to take some weight off our CEO and shift the conversation over to me. I’d handle the presidential crisis while he focused on CEO things, you know, like running LATAM’s number one crypto exchange.
Which, in case you thought otherwise, is no minor challenge.
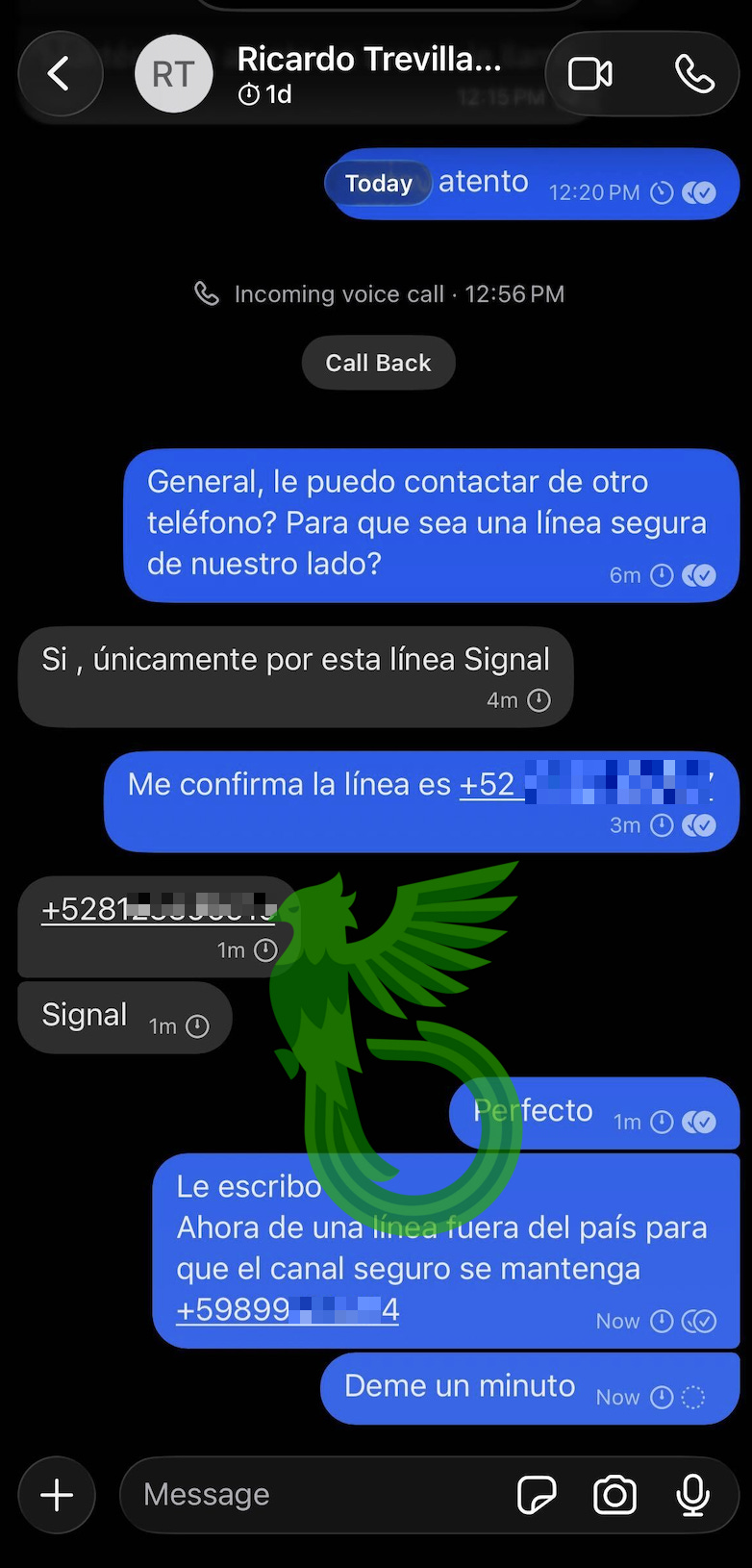
We shared a Uruguayan decoy number with them to shift the workload onto me.
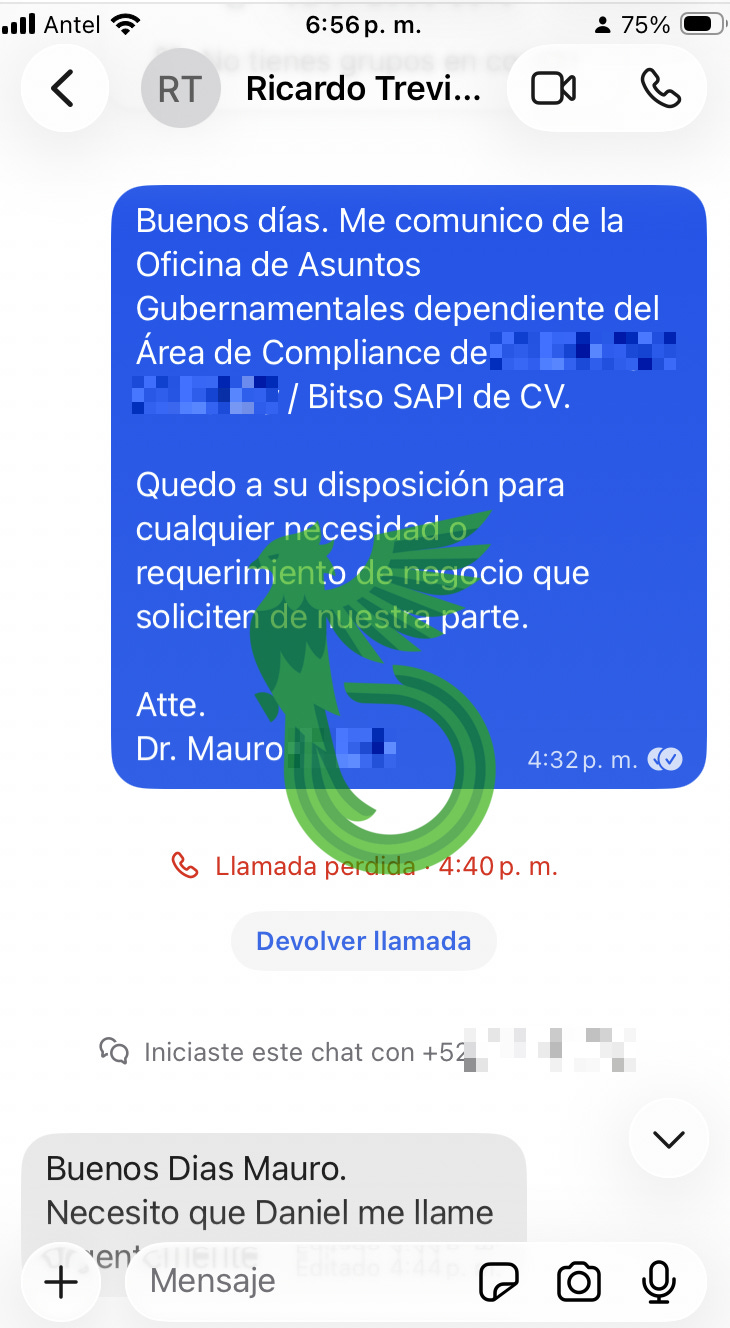
Posing as the Chief Government Affairs Officer (a title I pulled straight from thin air), I struck up a conversation with the threat actors in an attempt to lure them into our trap.
We got their interest, and their attention.
Now let’s find out what they want, how they want it, when they want it, and what they expect from us.
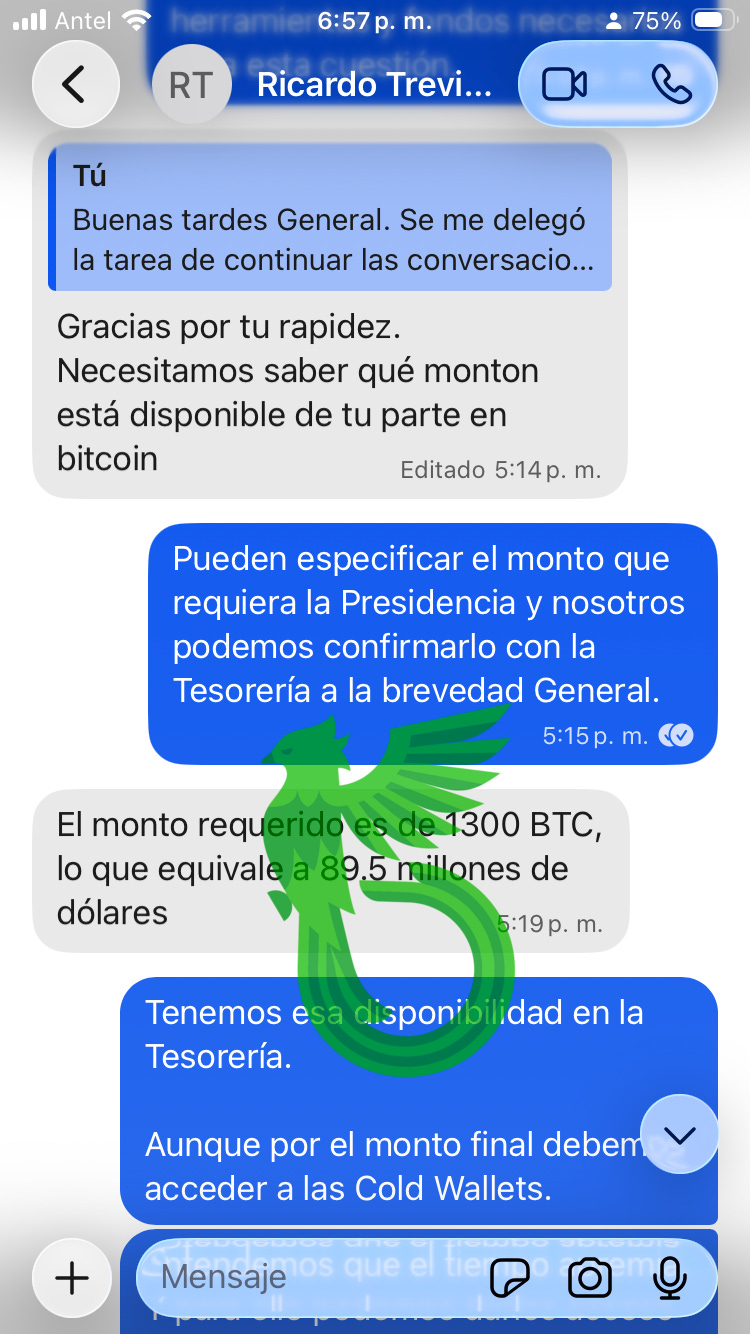
They name us a price, and we’ll play along with it.
Don’t worry, boys, we’ll bring you back home, even if it costs us 1300 BTC (roughly 89.5 million dollars). Let me get my wallet.
Or better yet, allow me to generate a secure internal environment with access to our cold wallets, so you can carry out the transaction yourself.
Help yourself. Take as much as you need.
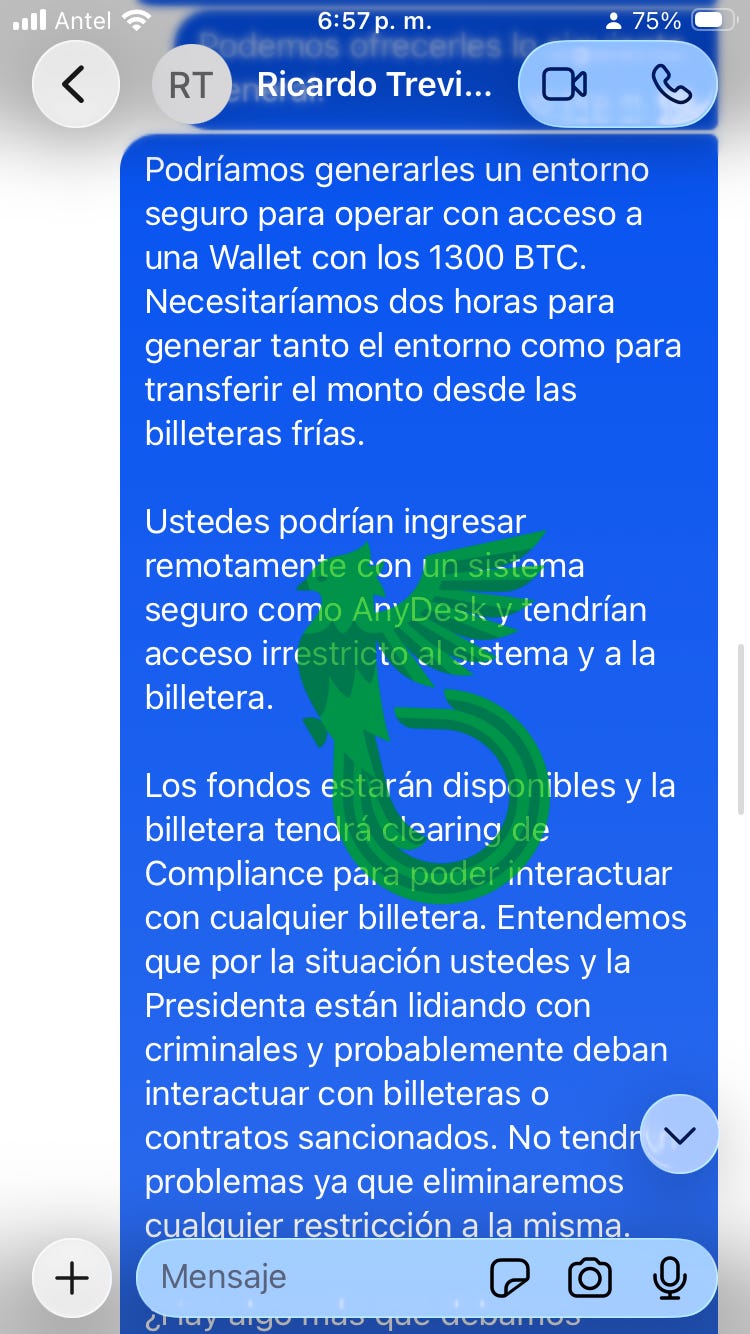
We make them believe that, due to compliance restrictions, the only way to claim their nearly 100 million dollar bounty is by connecting via AnyDesk to a “secure environment”, which is actually an ANY.RUN sandbox.
Once the threat actor connects to the environment, we can record every action and extract every piece of information from them, including their IP address and every single click they make.
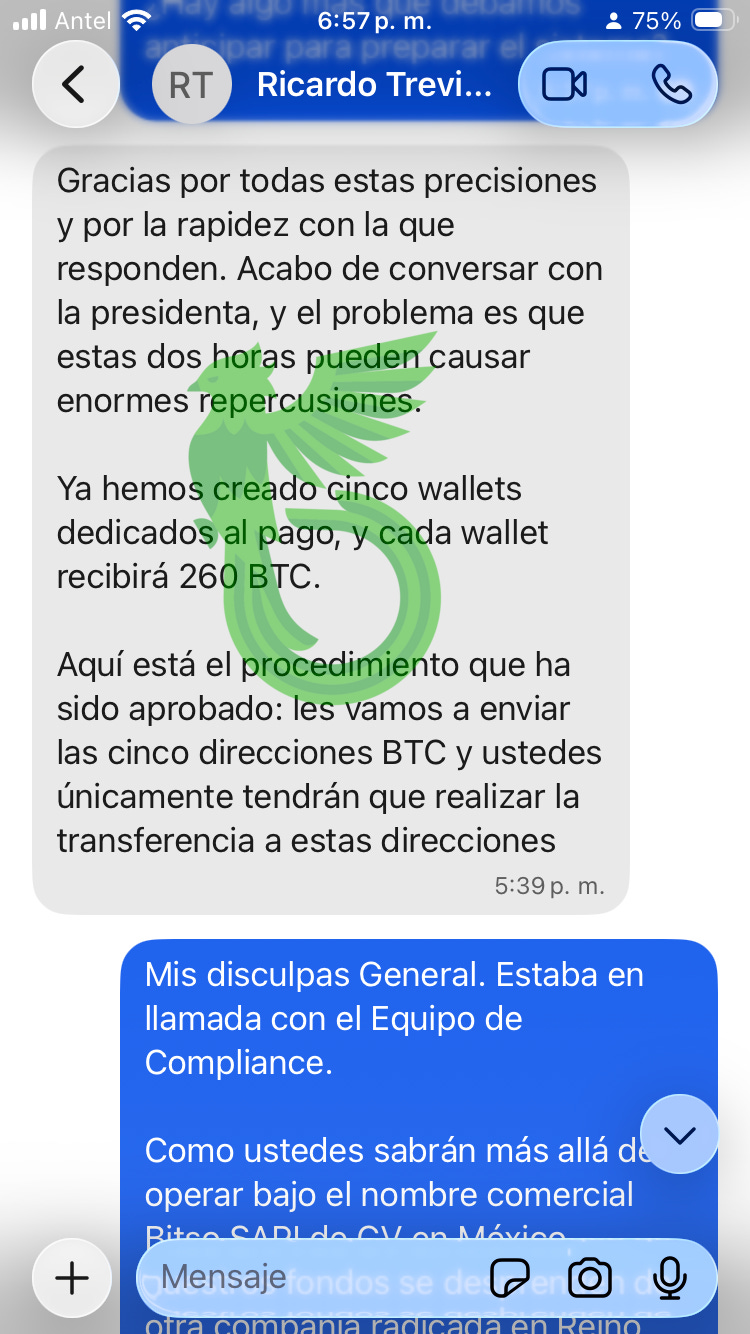
The muppets try to bargain, claiming they’ve set up five wallets and asking us to transfer 260 BTC to each. But I am the negotiator here.
We politely decline, stating that due to compliance limitations, we must set up a secure environment where they must manually carry out the transactions themselves.
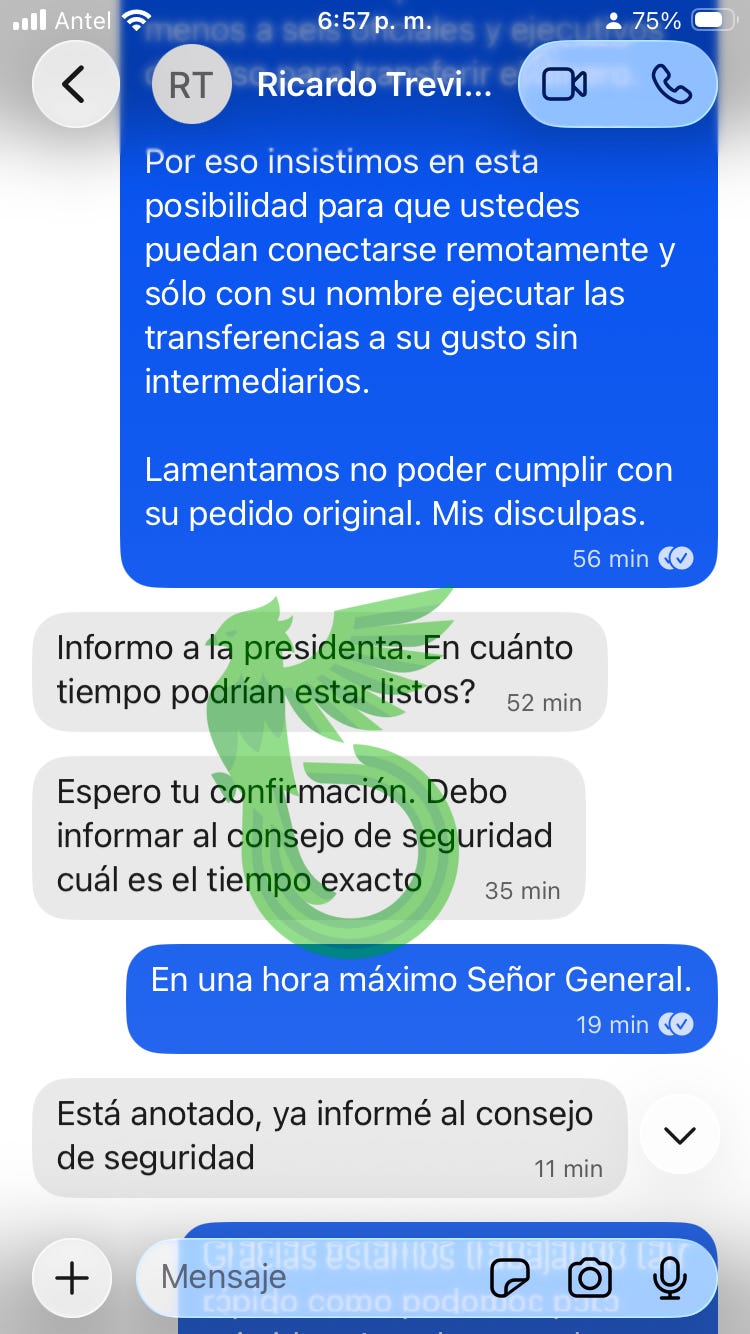
Now for the best part: we have a whole hour to set up tricks and traps.
In the past, we’ve managed to trap and tame professional threat actors like EVILNUM, Labyrinth Chollima, Kimsuky, and Famous Chollima. All of them approached us and left recorded, mocked, and most importantly, empty-handed.
So we can definitely settle the score with these threat stuntmen. And, why not, make an example out of them.
An hour went by, and I had finished setting up our sandbox and laying down some tripwires.
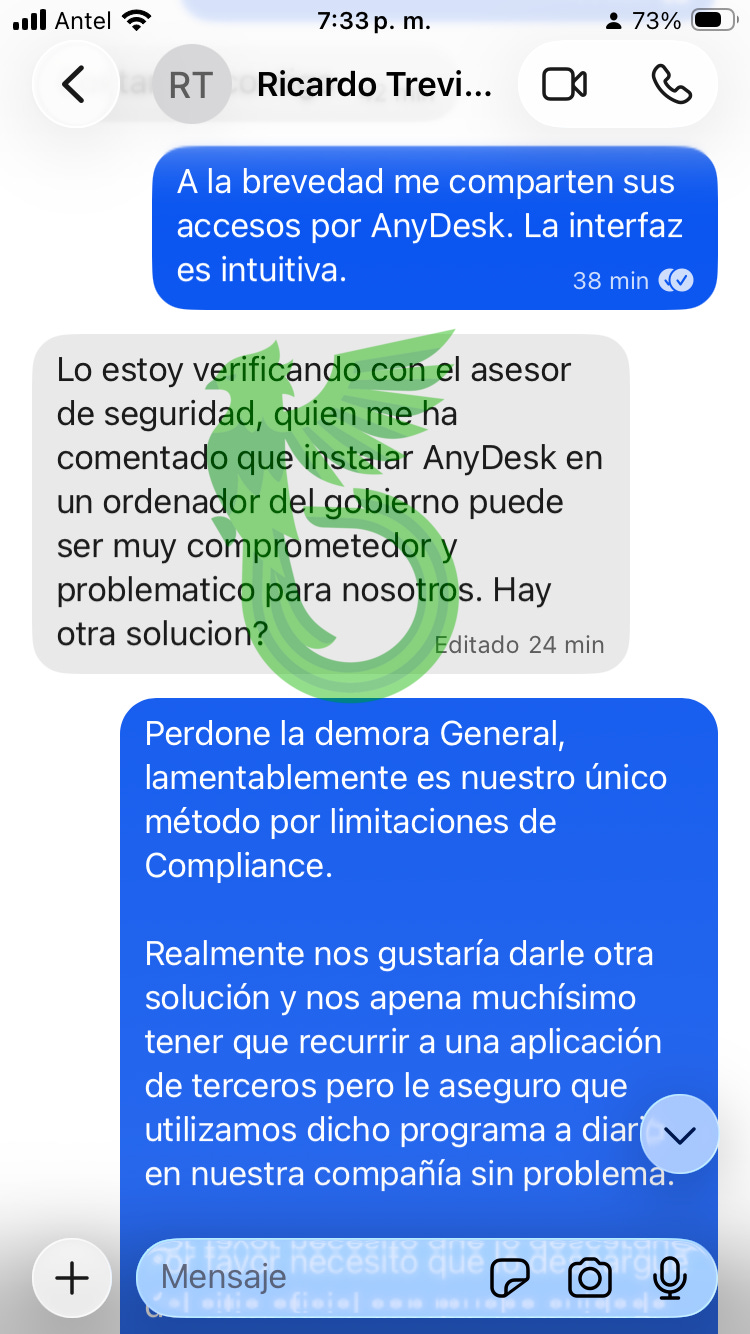
Some suspicions arise. He’s afraid of installing AnyDesk.
And that’s where we have to draw a line, an interesting one.
DPRK agents use AnyDesk daily to work for remote companies under fake or stolen identities. They don’t care.
Chinese APTs literally set up legal companies just to issue valid code-signing certificates, so their malware runs as trusted software.
And you’re scared of installing AnyDesk… for the chance to win 1300 BTC?
But this is my case, I’m the negotiator here, so I convince him to keep going.
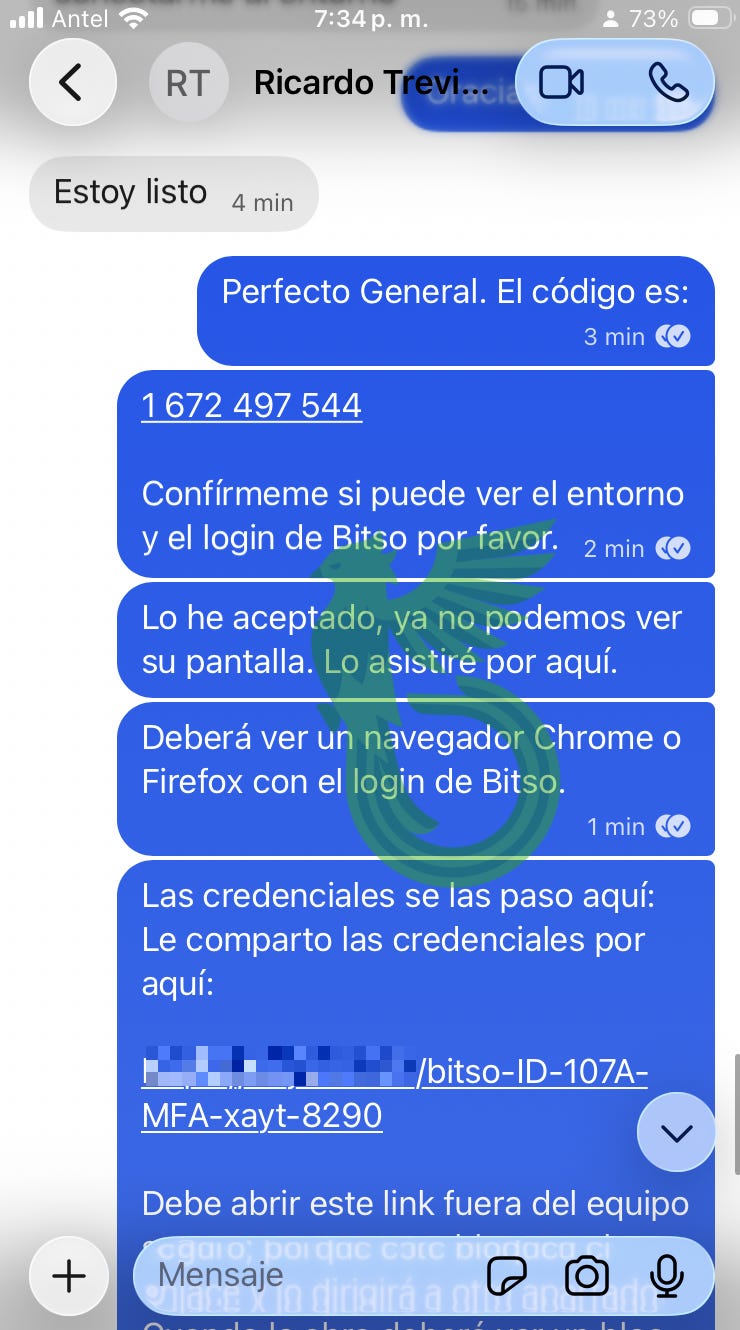
We shared the AnyDesk access code and a link to the “wallet credentials”.
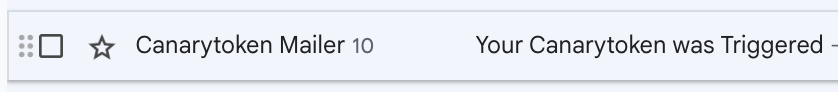
Of course, if you’ve been following our posts, you already know what that link really is: a canary token. Once triggered, it reveals everything about the visitor: location, IP address, browser fingerprint and more.
And if your eyes are sharp enough, you might have noticed that the leetspeak in the URL spells out a not-so-friendly (but deserved) nickname for our guest.
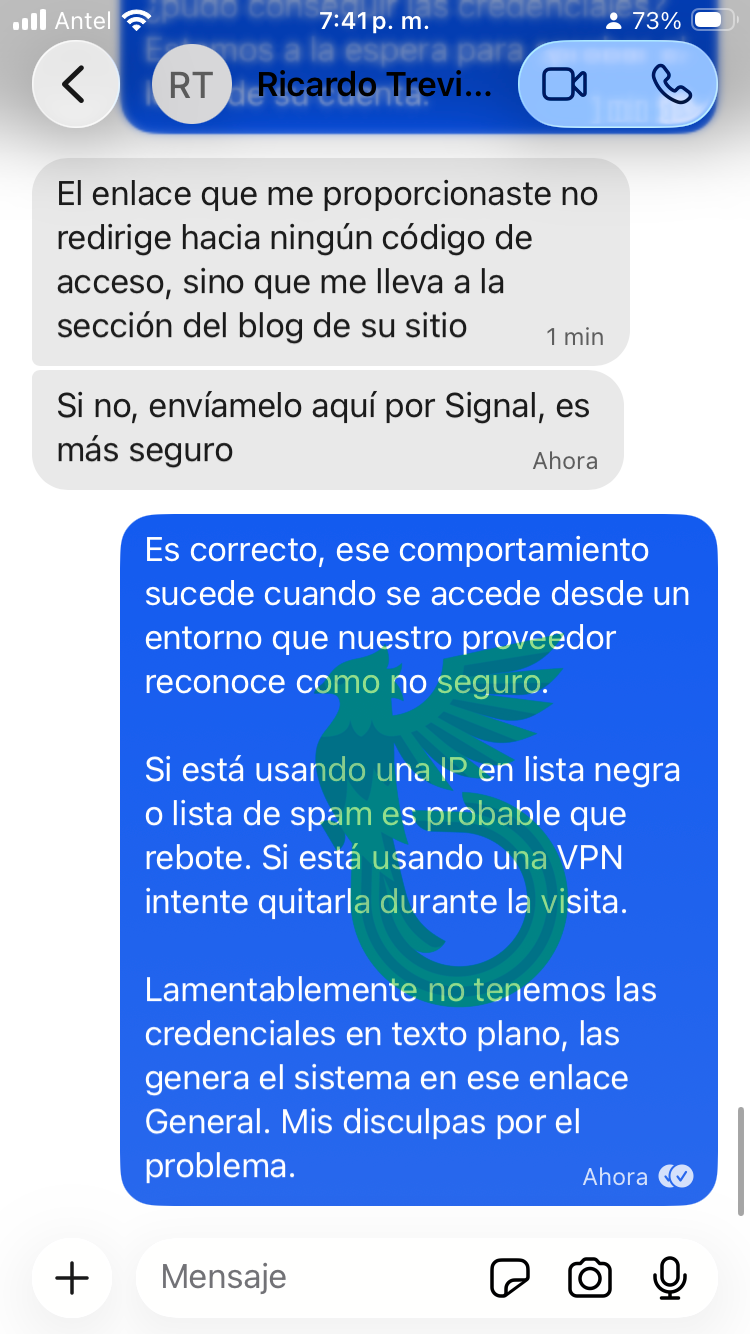
The threat stuntman complains that the canary token link sends him into a never-ending redirect loop.
I calmly explain that it’s likely because he’s using a blacklisted IP (probably from a VPS or a VPN) which triggers the system to bounce the request.
He then spends a lot of time (and I do mean a lot) switching between different VPS and VPN services, desperately trying to bypass the control.
You can trip over the same stone twice.
But ten times?
That definitely sets a new record.
Finally, when laughter turns into pity and second-hand embarrassment, he starts to realise what’s going on: He’s the one being hunted.
There are no 1300 BTC. There never were.
No 100 million dollars to claim. Not even close.
It was all for nothing.
He tries to confront me, but I had already prepared a handcrafted gift just for him.
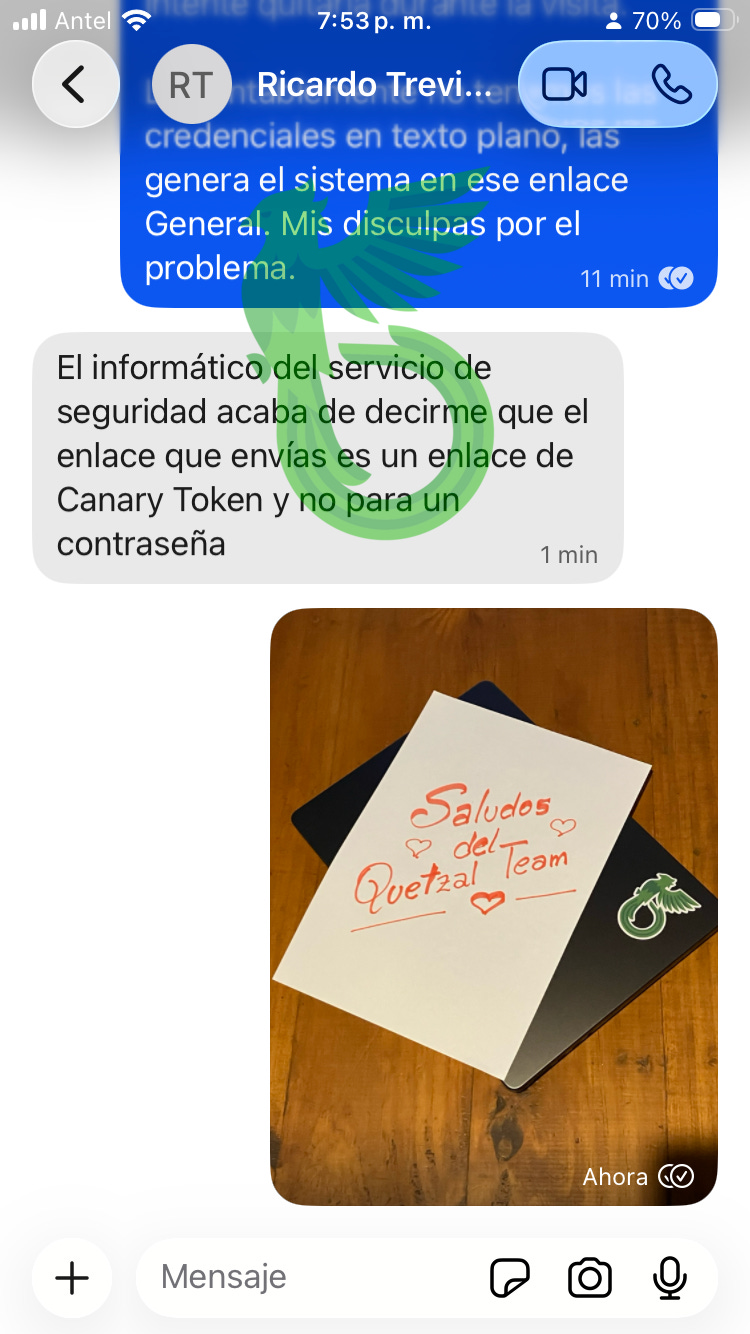
Saint Valentine’s spirit is in the air, honey.
Of course there are no credentials, you nerd!
Go touch some grass, love someone, spread pheromones. You unloved, uncared, unmoisturized threat stuntman.
And if you were counting on this money to gift your significant other something cute… I’m sorry to spoil it, bunny.
But you can have this handcrafted letter for free:
Outro
I’m not the empath type, but sometimes I like to put myself in the Threat Actor’s shoes.
Try it, just for a second.
It all looked so good. The perfect plan.
You were gonna be rich. It was your last “job” with the boys.
One last run, and you’d all retire to Cayman, Belize, Seychelles, Palau, you name it.
You’re counting the money in your head.
1300 BTC. Almost 100 million dollars.
You fantasize about anything with a price tag. And even things without one.
In your head, you’re already spending it.
But some weirdos with a green bird logo show up and call you a nerd.
There is no Cayman. There is no 1300 BTC.
The dream is gone.
You were so close!
But hey, at least you have a nice hand crafted sign for this Valentine.
Moral of the story is:
Don’t be a nerd. Spread love, not malware.
Happy Valentine’s from Quetzal Team!
IOCs
IPv4:79.127.229.179
IPv4:15.220.188.32
IPv4:38.165.237.105
IPv4:46.62.158.224
IPv4:142.93.176.189
IPv4:3.85.167.157
URL:hxxps[:]//us05web[.]zoom[.]us/j/83413214716?pwd=KYKBnV0oDagfujaE3b5lmIFuKLmSwN.1
Phone:+525536865100
Phone:+528123396516